What has ransomware looked like in 2025 so far? And how has the events of 2024 shaped the ransomware ecosystem today?
In this episode of Leaky Weekly, the show that covers cybercrime current events, senior threat intelligence researcher Tammy Harper from Flare joins host and security researcher Nick Ascoli to dive into the events that shaped the 2024 ransomware landscape and what 2025 looks like to date.
Tune in for current events on the podcast on Spotify, on Apple Podcasts, check out the video episode on YouTube, or keep reading this article for the highlights.
More of the Same for 2024
In many ways, 2024’s ransomware landscape mirrored the events of 2023 with established players still dominating underground markets and new entrants seeking to gain traction.
The 2024 Cybercrime Ecosystem
At the beginning of 2024, the disruptions caused by law enforcement takedowns were not quite on the horizon yet. The ecosystem remained stable with cybercriminals using well-oiled frameworks for deploying attacks.
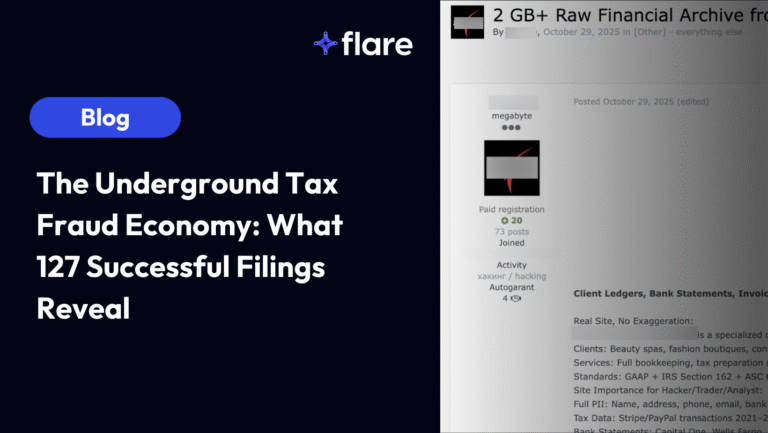
Source: RansomLook
For example, before the major disruptions occurred, ransomware groups like Scattered Spider began making a name for themselves and leveraging social engineering techniques to achieve their objectives.
Operation Chronos took down LockBit which disrupted the dark web Ransomware-as-a-Service (RaaS) cybercriminal ecosystem. This created an opportunity for smaller, newer threat groups to pick up steam, including:
- Medusa: first identified in June 2021 with over 300 victims as of February 2025.
- RansomHub: first identified in February 2024 with over 210 victims by August 2024
- Black Basta: first identified in April 2022 with over 500 victims by May 2024. (Learn more about what Flare Research investigated with Black Basta’s infrastructure based on a chat leak)
- BianLian: first identified in June 2022 shifting to exclusively exfiltration-based extortion around June 2024.
Victim Statistics
Every year, committing cyber crime gets approximately 5% easier, correlating to an increase in victims. From 2023 to 2024, the cybercriminal ecosystem saw a shift in players. For example, a Cybersecurity and Infrastructure Security Agency (CISA) advisory noted the increased activity from ALPHV, also known as Blackcat, targeting the healthcare sector.
In 2024, ALPHV and RansomHub accounted for almost half of all victim claims. However, as the year progressed, Qilin, originally launched as Agenda in July 2022, became increasingly active claiming responsibility for more than 60 ransomware attacks between January 2024 and June 2024.
Source: RansomLook
Another factor shaping the cybercrime underworld was the ease of circulating, monetizing, and distributing credentials. Initial access brokers (IABs) providing these leaked credentials for a fee has continued to make the ecosystem more efficient.
2025: Catching Up After Takedowns
The 2024 RedLine take down has played a role in 2025’s disruptions, as threat actors seem to be pseudo-retiring or ghosting forums. Additionally, many cybercrime groups conduct attacks then take time before they take public responsibility.
Cl0p and Vulnerabilities
Cl0p focused its late 2024 attacks on two vulnerabilities in the Cleo’s file transfer tools, Harmony, VLTrader, and LexiCom. While Cleo deployed the attacks in November and December 2024, it only published a high-level warning to victims threatening to expose them publicly.
Likely due to the holidays, Cl0p took nearly two months to publish additional information, making victim lists available in January and February of 2025.
Compromised Credentials
Most ransomware operators focus on using compromised credentials to gain the initial access since identifying zero day vulnerabilities and creating exploits is more time-consuming and resource-intensive. For example, the malicious actors arrested and imprisoned for the attacks, Kiberphant0m and Waifu, likely used stolen credentials that stealer malware harvested so they could gain unauthorized access and exfiltrate sensitive data.
Over the last year, the number of IABs selling access has increased. In tandem, more ransomware operators buy access which makes it easier for less technically sophisticated cybercriminals to deploy the attacks.
Leaky Weekly and Flare Academy
Leaky Weekly is brought to you by Flare, the world’s easiest to use and most comprehensive cybercrime database that integrates into your security program in 30 minutes.
Flare now offers Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick!), and more.