
Digital risk protection (DRP) refers to the “proactive defense of business assets against the threats they face.” This definition starts off with the notion of proactive defense which translates to concrete actions taken by companies to eliminate threats and identify leaks before they hurt their brand and reputation. As shown below, companies can benefit from an increasing number of enterprise-grade security solutions to fend off digital risks.
- Password and API key leaks on source code repositories.
- Personal information leaks.
- Public screenshots of Account Takeover Fraud, which includes customer IDs and names.
- Automated take-down requests sent to administrators of source code repositories.
- Automatic lookup in victim directory to identify potential identity fraud, and additional screening when applying for credit.
- Automated flagging and freezing of account takeover attempts as potential fraud.
DRP customers mainly interact with digital risk lists and alerts, as well as with automated remediation recommendations. An essential part of DRP solutions should be, however, a full transparent history of how digital risks are identified in the first place, and whether these risks represent the most significant liabilities a company is facing at any given time. This transparency is crucial to evaluate a DRP solution and can be evaluated by a simple question: what coverage does a Digital Risk Protection solution have?
Digital Risk Protection Coverage Explained
Coverage is most often understood as the number of websites indexed by a DRP solution to identify digital risks. This is an important metric, as malicious actors tend to cluster in niche websites with their peers from the same geographical region, or are active in the same type of fraud. This is best exemplified by the many dark web markets that cater to the needs of specific malicious actors:
- Hydra for Russians
- Canadian Headquarters for Canadians
- French Dark Net Market for French
- German Plaza for Germans
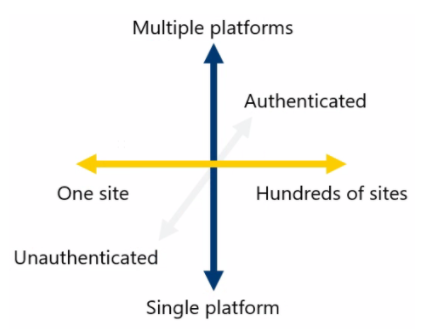
Collecting intelligence on as many websites as possible is useful to tap into multiple criminal underground communities and get a holistic view of the threat landscape. Coverage, on the other hand, is much more complex because several factors need to be addressed in assessing DRP solutions, beyond the number of websites. We present below a model that details the three axes of coverage.
How Actionable Intelligence Enhances Security Defense
The horizontal line shows the coverage continuum based on the number of websites indexed by a DRP solution. In addition to this, coverage should also address the number of platforms monitored, beyond websites. Malicious actors are known to be active on the dark and clear web, but also on instant chat messaging systems (ex. ICQ), voice systems (ex. Discord) and social media (ex. Facebook). The same malicious actors are active on multiple platforms and share different types of information.
Connecting the dots has the potential to vastly improve digital risk intelligence quality. By indexing one platform, a tool could provide some of the answers to fend off digital risks. However, indexing a vast number of platforms ensures a superior threat intelligence level and enhances defense output.
Why Authentication Is Vital in Digital Risk Protection Coverage
No matter the platform, the question of authentication is crucial to understand coverage. Authentication means entering a username and a password to access a platform. Over 90% of all online content is allegedly protected by authentication. This means coverage with no authentication has limited value for intelligence. Manual labor, often too costly for quite a few DRP providers, is necessary to develop authentication crawlers.
Even with authenticated systems, there are differences that impact DRP solutions.
- Open authentication. These platforms protect their content behind an authentication wall, but allow anyone to register an account.
- Paid authentication. These platforms require a payment (usually between $10 and $100) to register an account.
- Peer authentication. These platforms require a reference, often an invitation code, which can only be generated by an existing member.
Similar to platform coverage, different types of malicious actors are likely to be active on different authentication levels. As a result, DRP platform coverage varies, depending on providers’ willingness to pay for authentication and engage with malicious actors to obtain invitation codes.
Conclusion
Transparency is at the core of all DRP solutions. Customers who understand the three axes of coverage can make more informed decisions about DRP solutions.
There will always be trade-offs concerning where solution providers situate themselves on the graph. While some may invest in covering a larger number of websites, they may fall short in authentication. Others could cover a wide range of platforms, but only a limited number of websites or resources. No vendor can rank high on all three axes.
DRP customers should make sure that their solution providers are transparent and can answer this simple question: where are they located on the axes of coverage?





