
Recent events at the Capitol in Washington D.C. were condemned for their impact on the democracy of the United States. What was much less discussed, however, is their impact on the integrity of U.S. government networks and databases.
Data Breach Today reported this week that:
Computers in [Speaker of the House] Nancy Pelosi’s office were left on and were unlocked [during the riots]. That is an incredibly poor security practice. While the apparent amateurism of the visible protestors might lead us to conclude they are unsophisticated, we know that our enemies are willing to use any opportunity to launch cyberattacks […]. PCs left unattended and logged in, as shown in photos, could allow for malware to be installed or data to be removed.
In essence, politicians and their staff fled the Capitol when rioters poured in through the windows and doors, leaving behind their workstations. In some cases, the computers were even powered on, and logged in, while rioters went from office to office. No public account of stolen hardware has been published so far, nor the result of any incident investigation.
It is probably too soon to fully understand if someone took advantage of the riots to infiltrate the Capitol’s computer networks, but the event provides us with an opportunity to talk about the need to physically protect computers, at least as much as their authentication software and credentials.
If a malicious actor gains physical access to a server or computer, they can install physical dongles between the computer and its peripherals such as screen, router and even keyboard and mouse. The screenshot below from the Hak5 Penetration Testing Store shows some devices that can be surreptitiously plugged into machines. These machines are small and discrete, and unlikely to be noticed, especially on projectors anchored to ceilings, or to computers under a desk. They are in many cases equipped with antennas to exfiltrate the information wirelessly.
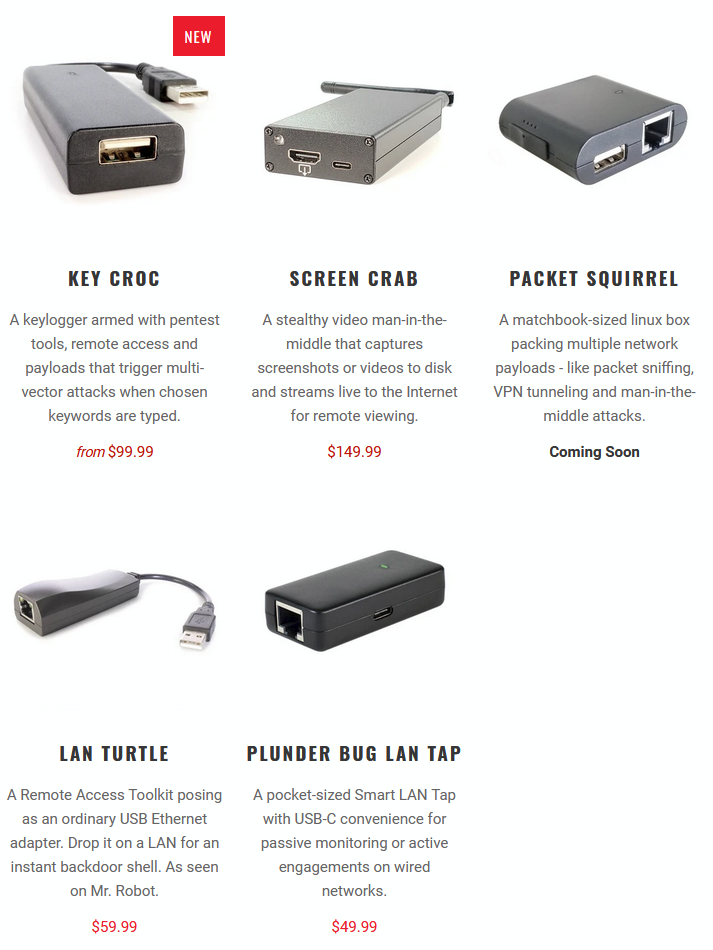
Physical access to a machine can also mean installing pieces of malware, especially if the computer or server is already powered on and logged in. This video was shot with a small USB key that masquerades as a keyboard. It demonstrates that in less than 3 seconds, the USB key can open a connection to a remote computer to provide access to its resources and documents. This attack would probably not survive a server or computer reboot, but would still provide a significant opportunity for malicious actors to steal confidential information.

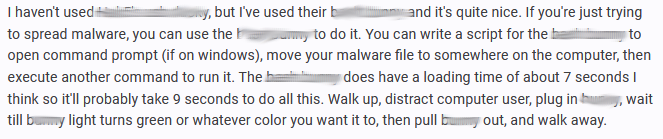
The demonstration in the video is by no means far fetched. Such attacks are openly discussed in criminal underground forums, with one user explaining:
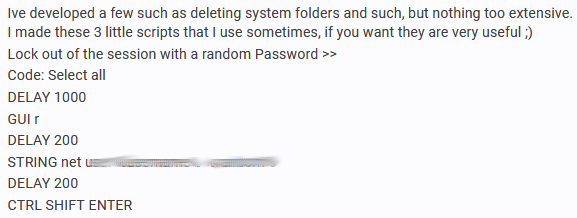
Unfortunately, malicious actors are also sharing and distributing scripts that delete your files, or, as the code below demonstrates, lock your computer using a random username and password that will stop you from using your machine until you reboot it.
Conclusion
A locked computer, or even a turned off computer, may seem at first as a low security risk if its integrity is compromised. Much emphasis in cybersecurity is placed on the software end of security. This opens a gap for malicious actors to target hardware computers that may not be as secured as central servers.
A junior member who lets an unknown person close to their computer, even for a number of seconds, may be creating a security risk for the company. Fortunately, malicious actors are always in need of each other to develop their tactics and methods, and openly share many of their secrets on the criminal underground.
The events at the Capitol may not lead to any significant cybersecurity incident. The close access, without supervision, of so many computers, however, raises serious questions about the integrity of the U.S. Government’s network that hopefully will be studied in the coming weeks. This demonstrates the need for clear policies for emergency situations, and to ensure that employees have enough training to remember to protect the physical access to their computers. Three seconds are apparently all that is needed for a malicious actor to remotely take control of a computer.





