Threat actors are not a monolith in their approach to cybercrime. The popular perception is that threat actors steal information for the sake of it, while knowing and accepting that they are doing something wrong. However, some threat actors also justify their actions by promoting an image that their activity ethically advances the cause of cybersecurity. At Flare we regularly see threat groups state that they are “(reverse) pen testers”. Security researchers are very familiar with ransomware groups referring to their actions as “pentesting after the fact.”
One such entity is the malicious group AlphaLock. The Flare Research team reviewed their Telegram channel, and combed through to identify the ways the group describes itself.
AlphaLock is a Russian hacking group that describes itself as a “pentesting training organization.” The group has a two-part business model designed to both educate cyber criminals, then weaponize them for profit against organizations.:
- Training: referred to as the Bazooka Code Pentest Training. This training covers the basics of offensive security and is designed to take non-technical users and teach social engineering and technical offensive security skills.
- Affiliate program: ALPentest Hacking Marketplace, which monetizes the services of the hackers trained through the training program
Threat Actors as Pentesters: AlphaLock Edition
The psychology of justifying cybercrime is fascinating. Going through AlphaLock’s recent Telegram messages, there are generally three areas where we can see that on full display:
- The language of “pentesting”
- Donating items and funding to an orphanage and animal shelters
- Description of training program as supporting cybersecurity
Pentest Messaging
The language of “pentesting” is sprinkled through the Telegram channel, starting with the name of the channel.
There were several graphics shared to announce opening up enrollment for training programs with different languages for soon-to-be threat actors. The logo includes the word “pentest.”

In addition, when referring to members of the AlphaLock community, they use terms such as:
- Pentesters from the AlphaLock Pentest community
- Freelance pentester
- Pentest partnership program
Program Language
The pentesting terminology is most prominently featured in descriptions of Alphalock’s training program. If you read only what they have published, it can be easy to mistake this for an ethical hacking program.
‼️ Over 250 people have gone through us and many of them stay with us and become cool specialists in the field of Pentesting.
Course Program:
Introduction to Linux and the basics of the command line
- Introduction to pentesting: basic concepts, methodologies, goals, and the fundamentals of ethical hacking.
- Understanding the concept and role of network security.
- Network scanning tools: introduction to Nmap and Masscan, their capabilities, command syntax, and examples of use.
- Finding open ports, identifying services, identifying vulnerabilities using scanners.
- Advanced use of Nmap: a wide range of parameters, security assessment using Nmap, determining the operating system and vulnerabilities.
- Advanced scanning tools: introduction to additional tools such as Zenmap, Unicornscan, and Hping.
- Protection from scanning: means of detection and protection against passive and active scanning, bypassing firewalls and control tools.
Password cracking, protocol analysis, and web application
- Password cracking: introduction to Hydra and its capabilities for cracking passwords for SSH, FTP, web forms, and other types of authentication.
- Password protection methods and strong authentication measures.
- Vulnerability analysis in web applications: introduction to the OWASP Top 10 and tools for detecting and exploiting vulnerabilities, such as ZAP Proxy and Burp Suite.
Our team is looking for outstanding specialists in the first pentest affiliate program in the world, AL PENTEST.
Charitable Giving
Donating to good causes is also a part of AlphaLock’s self-image as ethical hackers.
Around the holiday season in December, AlphaLock published a poll on charitable giving. The message stated that the group would send “50% of the entrance fees to charitable organizations.”
The group then allocated about $1000 USD to an orphanage in Russia, and the group announced that, “we will create a New Year’s miracle for the children 😍.” Apparently other members of the group advocated to donate to an animal shelter as well.
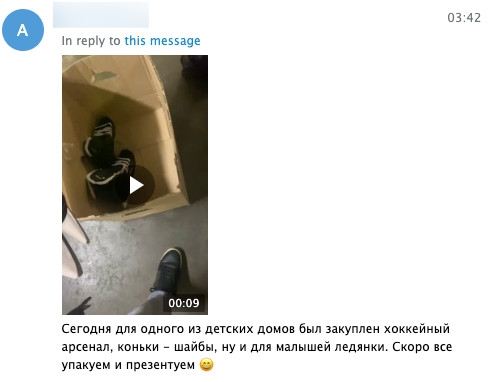
AlphaLock purchased a “hockey arsenal” for one Russian orphanage, and the gift package included ice skates, pucks, and sleds. The group shared a video in the channel in which an unshown person distributed the items. The video displayed the ice skates with logos: “AL PENTEST.”

What Does This Mean?
Understanding the Impact of AlphaLock in Cybersecurity
AlphaLock’s activity on Telegram offers valuable insights.
- Branding: It’s become evident that cybercriminal groups are increasingly emphasizing their branding and identity. This shift towards building a recognizable brand is vividly exemplified by AlphaLock, which has dedicated considerable efforts towards crafting a distinct image and reputation, both within and outside of its direct sphere of influence.
- Shifting Arena of Cyber Threats: Threat actor activity on Telegram challenges the traditional belief that cyber threats predominantly lurk reside on the dark web. Today, the distinction between the dark web and more accessible platforms is becoming increasingly opaque. Applications like Telegram and clear web sites are merging into a unified space where threat actors can easily network and orchestrate their plans. Modern cybersecurity calls for Continuous Threat Exposure Management across various avenues to most effectively counter threats.
Monitoring Telegram and Other Sources with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and illicit Telegram channels 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.