
Phishing kits are credential-harvesting operations that are cleverly disguised as standard web pages from Microsoft, Instagram, PayPal, and more. They can steal information from victims, then exfiltrate it to Discord or Telegram. They are unfortunately dangerously effective and widely available, but with the right knowledge, security teams can take advantage of them as intelligence assets.
In his video Hunting Phishing Kits, ethical hacker and cybersecurity researcher John Hammond investigates phishing kits. Check out the video, and/or we’ve put together takeaways for you from the video below.
1. Phishing Kits Come Fully Assembled
Are threat actors building phishing sites from scratch? No, much like meal prep kits, and as the name implies, they are pre-built kits. Most phishing websites are actually powered by downloadable kits that include everything needed. They include zip files bundled with all the components needed to spin up a credential-harvesting operation in minutes. Typically, they contain:
- Cloned HTML pages of legitimate services like Microsoft, Google, or banking portals
- JavaScript to obfuscate client-side code and behavior
- PHP to exfiltrate stolen credentials to remote servers or email
These kits are widely sold or traded on underground forums, making phishing campaigns more accessible than ever—even to threat actors who may not have the skills to build their own kit.
2. They Look Legitimate—Down to the Last Pixel
One of the most unsettling insights? These kits often create websites that visually match the originals almost perfectly. John walks through cloned login portals that replicate brand logos, colors, fonts, and even two-factor prompts.
On mobile devices, the phishing kits’ URL is more difficult to see, so victims are even more likely to fall for the ruse.
In one example, the only way to tell the site was fake was through a subtle difference in the domain—e.g., login-microsoftverify[.]com vs login.microsoft.com.
However, some sites are not as close to their real counterparts. For example, this Instagram phishing kit has a font style that doesn’t match with the original Instagram login page, and the navigation bar at the bottom doesn’t lead to anything if clicked.
John looks up an Instagram phishing kit
Flare Research came across a sophisticated and targeted phishing attempt that mimics a recruiting email from Google. This email did not include typos, had proper branding, and was clearly well researched. This page leads to a website with a Google login, and has capabilities to capture MFA codes.
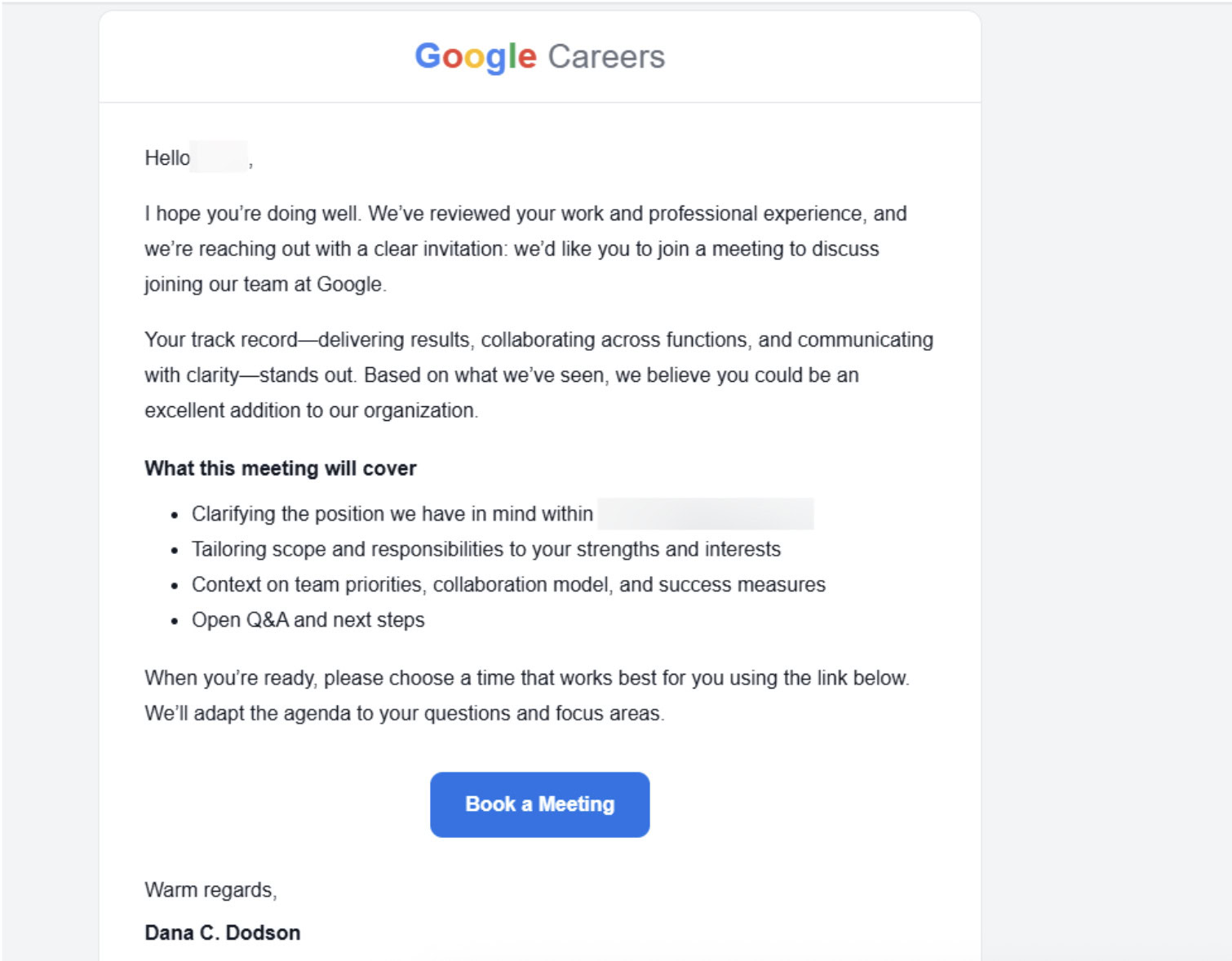
Phishing email that looks like it is recruiting someone for a job at Google
3. They Include Built-In Defenses Against Security Researchers
Phishing kits don’t just fool end users—they try to evade detection by security practitioners too. John reveals that many kits include:
- IP filtering to block traffic from known cloud providers or government ranges
- User-agent detection to filter out bots and crawlers
- Referrer checks to ensure the site only works when linked from specific sources
- Obfuscated code to obscure the behaviour of the website, making it harder to analyze
Some kits even destroy themselves if opened in an environment they suspect is being used for research.
4. Simple Tools Can Analyze a Phishing Kit
John demonstrates how basic tools like VS Code, terminal utilities (grep, strings), and curl can go a long way in understanding a kit’s functionality.
He uses static analysis to look at how credentials are harvested—whether they’re emailed to a burner address, uploaded to a server, or sent to a Telegram bot.
Then he walks through dynamic analysis by spinning up a local environment to see the live behavior of a phishing site and the kinds of data it captures.
This hybrid approach of static and dynamic analysis reveals:
- How stolen data is exfiltrated (ex. email, PHP mailer, Telegram)
- Hidden backdoors that may also compromise the phisher (yes—phishing the phishers!)
- Clues about the creator or reuse of kits
He even shows how to trace exfiltration endpoints and backtrack to the operator’s infrastructure.
5. Phishing Kits Are Valuable Sources of Threat Intel
John states that phishing kits aren’t just threats—they’re also opportunities. If security teams can collect and analyze kits, they can:
- Build detections for indicators of compromise (IOCs) like domain patterns or email exfil endpoints
- Identify campaign infrastructure
- Track campaign reuse as many kits get passed around and rebranded while sharing code across different kits
- Map attacker TTPs (tactics, techniques, and procedures) and sometimes even identify the attackers, especially when poor opsec leaves real names or emails in config files
- Find reused “phishing logs” or stolen credential dumps
- Learn about the creator’s intentions or targets by finding metadata like usernames or site-specific variables
- Track down phishing domains or catch kits before they’re widely deployed with OSINT
John looks into Telegram channels that sell phishing kits
Monitor for Phishing Kits with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Check out what may be on the dark web about your organization with a free trial.

