
The ransomware ecosystem entered a volatile phase in 2025, marked by the disappearance of major players such as BlackCat, the emergence of ambitious new groups, and a flurry of underground activity. This is a transition period as ransomware groups try to fill the void after RansomHub’s collapse. We’ve put together our predictions for the rest of the year based on what we know.
The Collapse of the Ransomware “Old Guard”
A year ago, names like LockBit, RansomHub, Akira, and Hunters dominated headlines. Today, the landscape has shifted dramatically.
- RansomHub has vanished from the scene entirely, allegedly taken down by law enforcement or a rival threat actor. Their infrastructure is offline, leaving affiliates scrambling for new groups. Many are moving to DragonForce.
- Akira remains active, but under the radar—operating quietly, successfully, and avoiding attention on public forums.
- Qilin and SafePay continue to post at high volumes, maintaining visibility.
- Play and Medusa are still in operation but with reduced impact.
- BianLian hasn’t been around for months.
- Cactus and Black Basta have gone silent. Black Basta’s downfall, in particular, was dramatic—following the leak of internal chat logs, possibly by an insider.
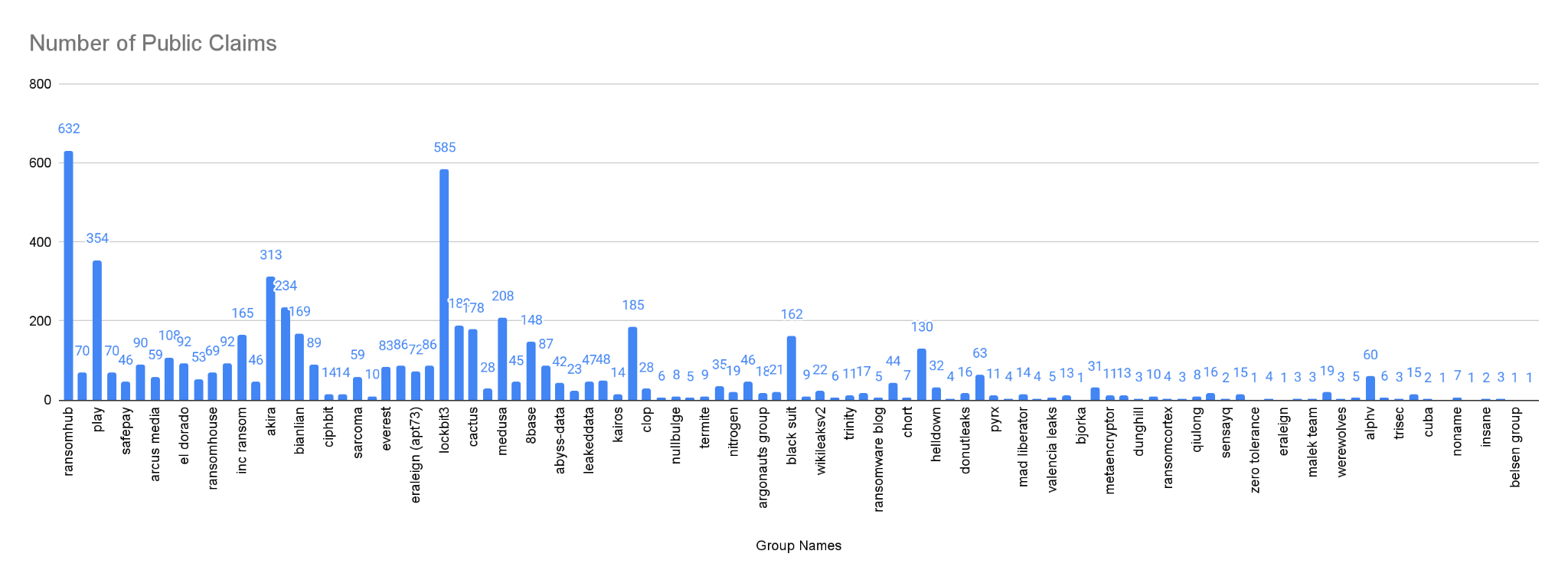
Number of public ransomware attack claims by ransomware group in 2024 (Source: RansomLook)
2025 Shakeup
The changes in 2025 are unique compared to the ransomware trends of previous years.
- In 2023, LockBit was the main player.
- In 2024, the “old guard” as mentioned above was there but there were newer players too.
- In 2025, many of the groups present have changed. The top groups such as Alphv, BlackBasta, and Lockbit were targeted by law enforcement and Cactus retired. Clop is still around but had one big campaign at the beginning of the year, rather than a continuous stream of attacks.
This is different from the collapse of Conti and REvil a few years earlier. To briefly recap their collapses:
- Conti: Conti collapsed after the group announced supporting Russia in its invasion of Ukraine in 2022, as Ukrainian members of the group leaked source code and internal communications in response. Conti split into three teams that spawned the next generation of ransomware groups including Royal, Akira, BlackSuit, Quantum, Zeon, and Karakut.
- REvil: REvil’s operations were disrupted and rebranded.
Currently, big players that are no longer active haven’t rebranded (yet?).
Enter DragonForce: From Forum to Front Runner
Their approach is novel: offering a white-label ransomware-as-a-service (RaaS) platform, where affiliates can deploy DragonForce tools and infrastructure under their own brand. This turnkey solution mirrors SaaS business models—complete with revenue splits (reportedly 80/20) and scalable payload delivery.
However, DragonForce actually wasn’t the first group to attempt white-labeling their RaaS. A few years ago, there was a group called Ransom Cartel that tried to unify REvil, LockBit, and some other groups. It imploded after a short period of time. It hasn’t been done with success because their white-label RansomBay is still under construction.
Early signs point to DragonForce building a cartel-style structure that could unify disparate actors under a shared toolkit. Their operations are sophisticated, targeted, and consistently high in quality. If enough affiliates adopt their platform, DragonForce could become the dominant player in 2025. Recently, there were some high-profile attacks on the retail sector in the UK, which has been attributed to DragonForce.
Qilin has also been posting constantly, and this indicates that DragonForce and Qilin are the most active groups.
Lessons from the Past: Trust and Code Quality Matter
Past takedowns, such as Conti and REvil, taught the cybersecurity industry an important lesson: when groups implode, researchers and defenders gain insight into their tooling, techniques, and negotiation strategies. Groups like Akira—who trace their lineage back to Conti—may benefit from this inherited sophistication, especially when it comes to building “trust” with victims. That trust, ironically, is about predictability: paying for a decryptor that works reliably, especially for large systems like ESXi.
Many smaller or newer groups lack this reliability, making negotiations riskier and complicating response efforts for victims and incident response teams alike.
Predictions for the Remainder of 2025
The ransomware ecosystem could rally around one or two major players by the end of the year. Top contenders include:
- DragonForce: If their white-label RaaS program gains traction, they could dominate.
- Qilin: A high-volume operation with a growing footprint, though lacking a white-label model (for now).
- Akira: Quiet but consistent, with strong roots and proven tech.
A breakout newcomer most likely won’t steal the spotlight—most of the “new” groups from earlier in the year (like Invader X and Van Helsing) failed to gain traction or even make their leak sites public. The new leaders will likely emerge from the current crop of active groups.
Ransomware Ecosystem: Own the Narrative, Own the Ecosystem
The ransomware ecosystem is undergoing a foundational transformation in 2025. The high-profile disappearances of legacy groups have created a power vacuum, and the coming months will determine who steps in to fill it. Whether through affiliate recruitment, innovation in business models, or sheer operational volume, a new generation of ransomware threat actors is vying for control.
This is a transition period and whoever controls the narrative by the end of the year might own the ecosystem.
Cybercrime Monitoring with Flare
The Flare threat intelligence solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.

