
We’re breaking down three cybercrime stories:
- Neon app
- Discord user data leak
- Oracle EBS Breach by Cl0p
Leaky Weekly is taking a break from a podcast episode this week, but stay tuned for our recap on covering the 2025 Microsoft Digital Defense report soon.
Neon App
Neon is a new viral app that pays people to record their phone calls, which the company sells to AI firms to train and test large models. The homepage has the quote: “It’s your data, and it’s time you got paid for it.”
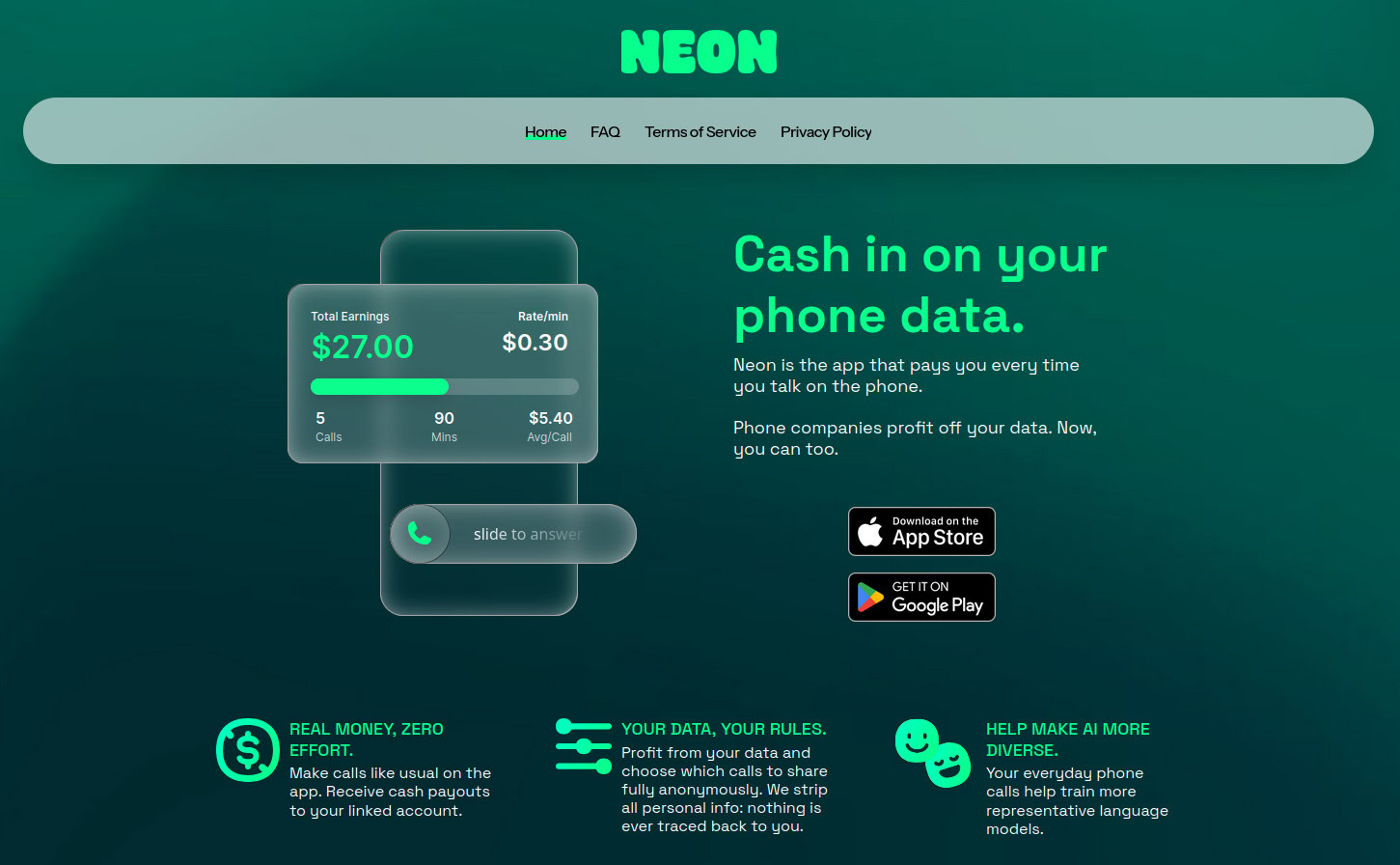
Home page of Neon (Source: Neon)
The app launched just in September, and shortly climbed to the top five free iPhone apps. The premise is: users place calls through the Neon app. For every minute recorded, Neon pays $0.30 if both callers use the app, or $0.15 if only one does. Payments are capped at thirty dollars per day.
The company states that data is anonymized before it is sold. However, the idea of recording real-world conversations for money raised immediate privacy concerns.
Then, late September, those concerns became real.
Researchers at TechCrunch discovered a flaw in Neon’s servers. Any logged-in user could access the phone numbers, call transcripts, audio files, and metadata of other users.
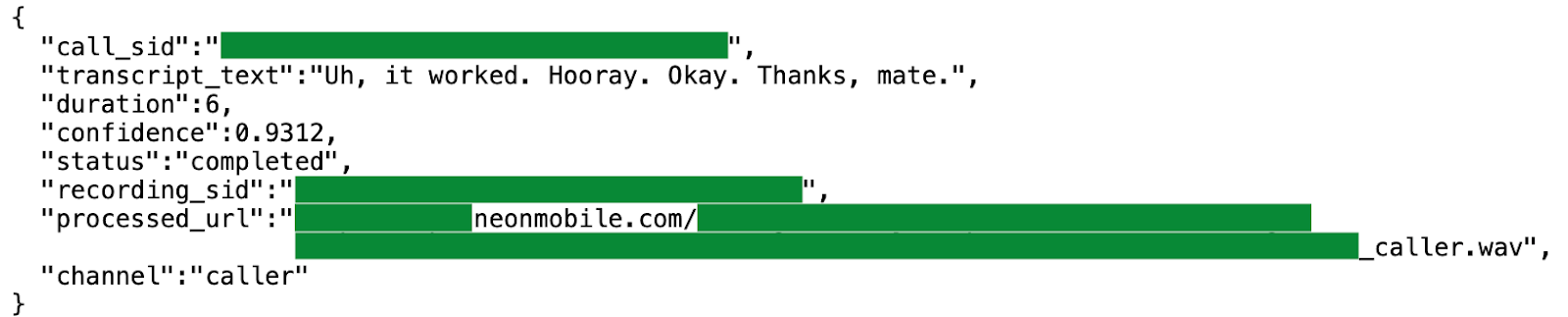
Leaked call transcript (Source: TechCrunch)
This revealed that the servers were wide open. Test accounts revealed:
- Transcripts
- Links to raw audio recordings
- Call details including numbers dialed
- Duration
- Payouts
Soon after being notified, founder Alex Kiam shut down the app. In emails to customers, he cited “extra layers of security,” but made no mention of the data exposure.
The app remains offline, pending a security audit. Kiam has promised new safeguards, but did not confirm whether data had already been stolen.
For now, Neon’s future remains uncertain. What was pitched as a way for users to profit from their own data has instead become another example of how fragile privacy can be.
Discord User Data Leaked
Discord has confirmed a data breach on their third-party customer service platform (Zendesk).
The attackers gained access to information from a limited number of users who had contacted Discord’s Customer Support or Trust & Safety teams. In a statement, Discord said the breach occurred on September 20th, and that the goal of the threat actors was to extort a ransom from the company.
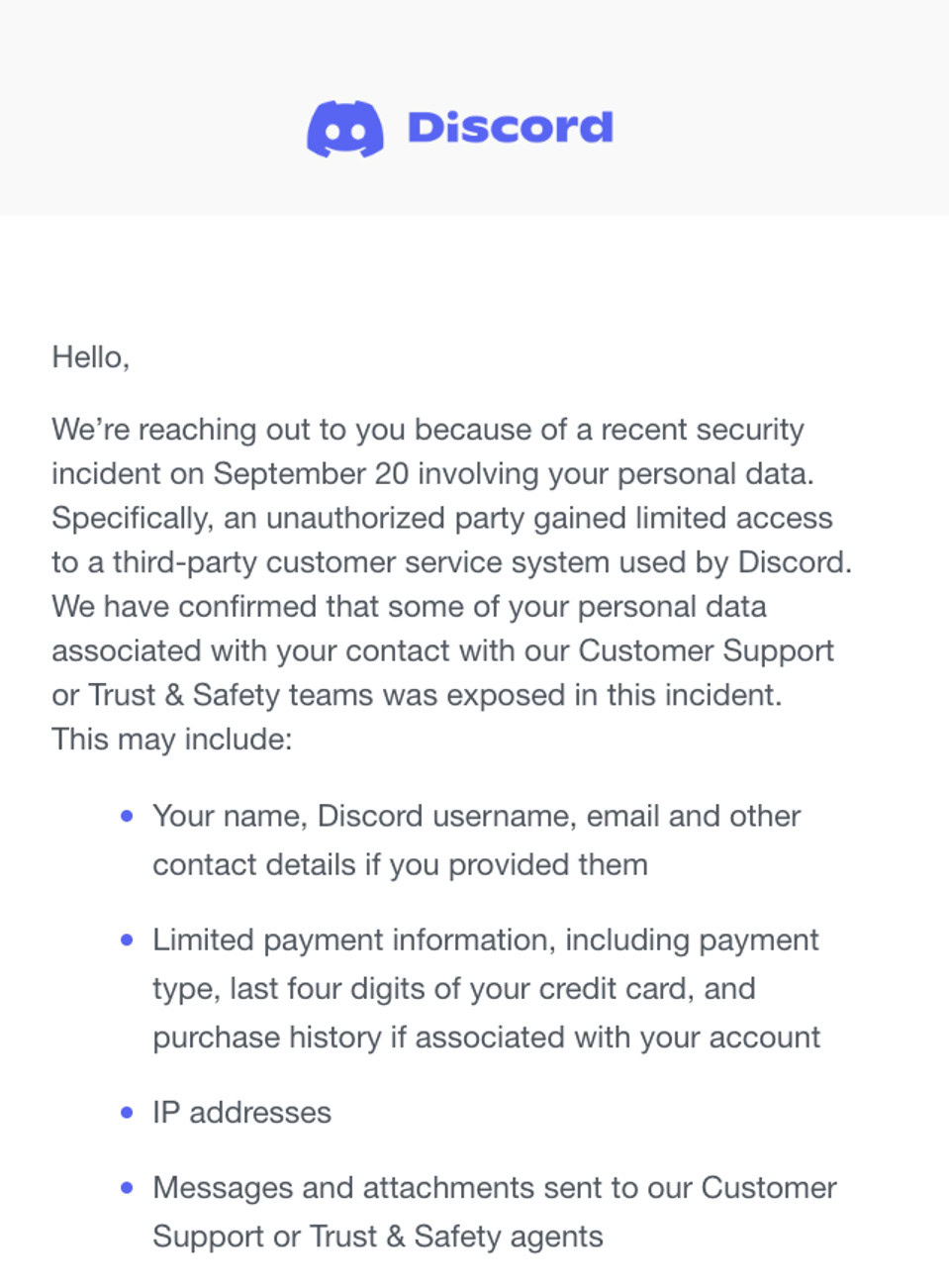
Announcement email of breach (Source: Discord)
The compromised data includes:
- Names
- Usernames
- Email addresses
- Last four digits of credit card numbers
In some cases, images of government IDs were also exposed. These images came from users who had appealed age verification decisions, a new safety measure required when Discord flags a user as underage.
Discord has revoked the vendor’s access to its internal ticketing system and launched an investigation with both internal and external forensics teams shortly after the attack took place. Data protection authorities and law enforcement agencies are now involved.
Since then, Discord has begun notifying affected users by email. Those whose IDs may have been accessed are being told directly.
Reported by multiple researchers and journalists, Scattered Lapsus$ Spider Hunters (SLSH) has claimed involvement in the attack. A screenshot circulating online appears to show them with access to internal Discord support data.
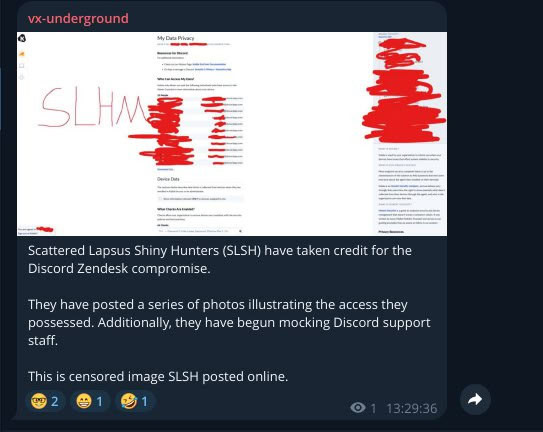
Initial reporting of SLSH being responsible for Discord Zendesk breach (Source: vx-underground)
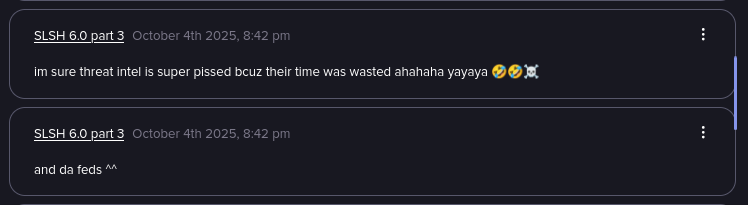
SLSH spreads misinformation about the Discord breach (Source: Flare)
Later claims by SLSH indicate that they only compromised their Okta instance, and published the screenshot at the same time as the unrelated Zendesk compromise, to stir up misinformation and confuse researchers or law enforcement.
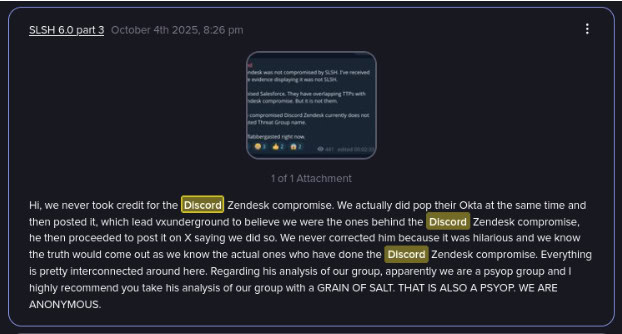
SLSH spreads misinformation about the Discord breach (Source: Flare)
There is currently no indication that SLSH had involvement with the Discord Zendesk breach, and it appears that the image was only posted for misinformation, which has been a recurring trend for this group.
For now, Discord maintains that its own systems remain uncompromised, but time will tell if any additional information has been accessed by the attackers.
Oracle E-Business Suite Breach by Cl0p
The Cl0p extortion group, also responsible for the MOVEit attacks, has sent high volumes of emails to company executives, alleging they had stolen sensitive data from Oracle E-Business Suite environments. The emails used hundreds of unrelated, compromised third-party email accounts suspected to be from infostealer malware.
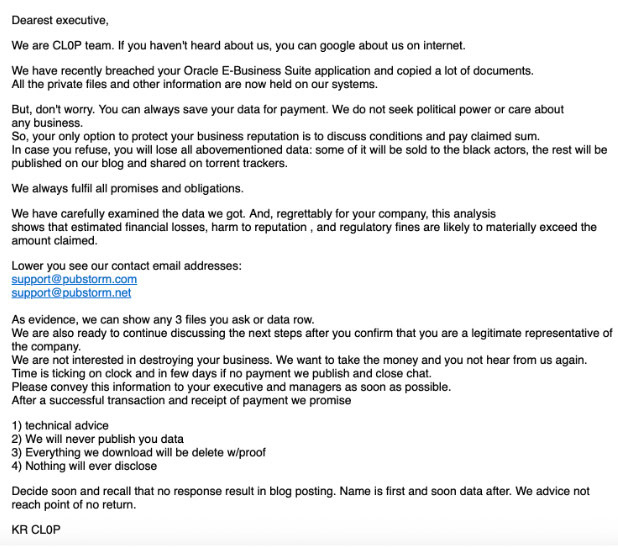
The extortion email from Cl0p sent to executives of impacted companies, sent by compromised email accounts (Source: Google Threat Intelligence Group, Mandiant)
The campaign began on September 29th and targeted Oracle’s enterprise software used by large organizations to manage business operations. The attackers claimed to have breached EBS systems and stolen internal documents from victims.
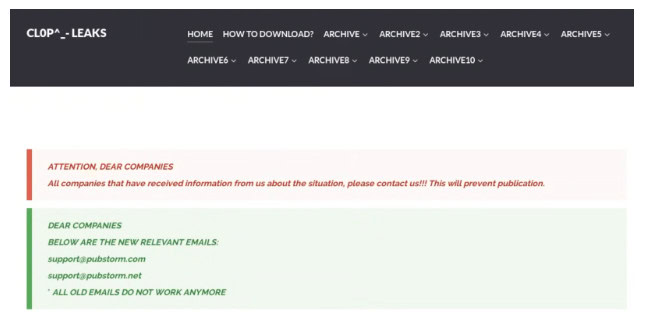
DLS of Cl0p, emails on DLS also match the email sent to executives (Source: Google threat intelligence team mandiant)
The activity may have started months earlier. Here is their timeline:
- August 9th: The group is believed to have exploited a zero-day vulnerability as early as August 9th, weeks before Oracle released a patch.
- October 4th: Oracle issued an emergency update on October 4th, after confirming that affected systems were vulnerable until July’s Critical Patch Update.
Researchers said the threat actors conducted reconnaissance throughout the summer, gaining access to Oracle EBS environments and exfiltrating data from multiple organizations.
The campaign follows Cl0p’s usual strategy of exploiting enterprise and third-party software to steal data at scale, as seen in attacks against MOVEit, GoAnywhere, and Accellion systems.
This story is still very fresh and more information is to come. At the time of writing, Oracle is yet to provide further information.
Leaky Weekly and Flare Academy
Brought to you by Flare, Threat Exposure Management solution and industry-leading dataset on cybercrime that integrates into your security program in 30 minutes. Check out what’s on the dark web (and more) about your organization with a free trial.
Check out Flare Academy:
- Our free training series led by experts on critical topics such as threat intelligence, operational security, and advanced investigation techniques (earn CPE credits towards cybersecurity certifications)
- Our Discord community is a space to learn from and with cybersecurity professionals and students, check out previous training resources, and keep up with upcoming training

