
In recent months, cybersecurity coverage has repeatedly highlighted the activity of Scattered Lapsus$ Hunters (SLSH), a porous and fast-evolving alliance of threat actors claiming to be associated with cybercriminal youth clusters such as The Com, Lapsus$, Scattered Spider, and ShinyHunters.
Before SLSH became publicly known, the cybercriminal activity later claimed by the group began in early to mid-2025. During that period, Google detailed a series of attacks that used voice phishing and abused OAuth-connected third-party applications to compromise Salesforce CRM environments belonging to multiple organizations. Google attributed these intrusions to UNC6040, while the later extortion phase was tracked as UNC6240, whose operators identified themselves as ShinyHunters. (In Google’s threat taxonomy, the acronym UNC refers to an unidentified cluster, meaning a group of activity that is not yet fully attributed to a known threat actor). Known victims included over 20 organizations such as Google, LVMH, or Allianz Life, whose Salesforce data was accessed to different degrees and later leveraged for extortion attempts.
Between August 8 and 18 2025, a separate wave tracked as UNC6395 abused OAuth and refresh tokens obtained from compromised Salesloft and Drift integrations to access and extract large volumes of customer data through Salesforce APIs, without breaching Salesforce itself. This activity reportedly affected more than 700 organizations, including Cloudflare, Zscaler, PagerDuty, and Tanium.
While Google attributed the initial intrusions to UNC6040 and UNC6395, responsible respectively for the vishing-based compromises and the later OAuth-token exploitation, initially only the extortion part connected these intrusion operators to ShinyHunters.
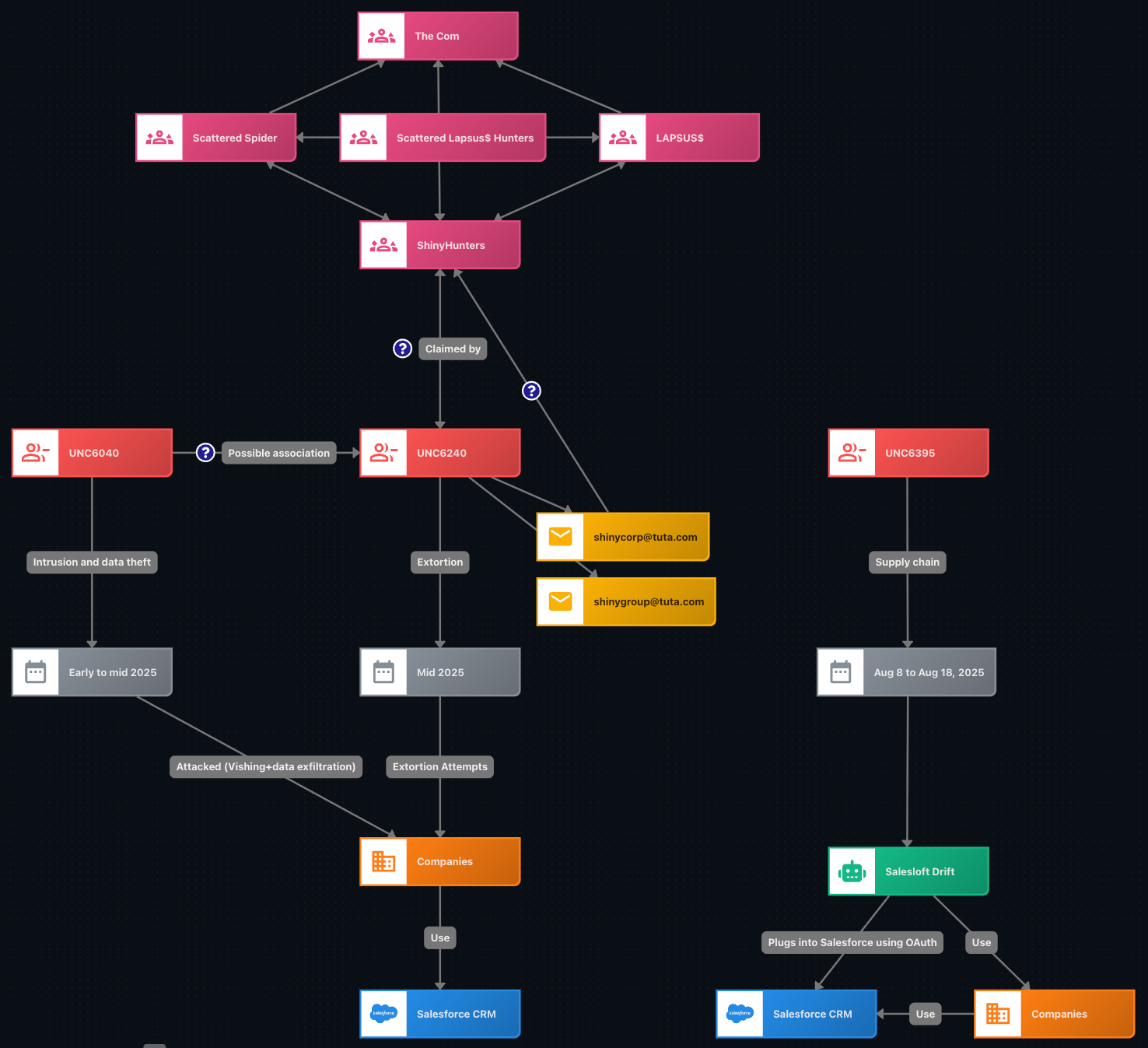
SaleForce CRM and SaleLoft campaigns, links to ShinyHunters and SLSH (Source: Flare)
Indeed, in the weeks that followed those disclosures, a wave of activity branded as “Scattered Lapsus$ Hunters” appeared across Telegram.
On the 8th of August 2025, a first among many channels surfaced claiming affiliation with the group, sharing data from alleged victims, issuing ransom demands, and amplifying threats through public leaks. This communication surge culminated in October 2025 with the launch of a dedicated ransom-shaming blog modeled after Ransomware-as-a-Service leak sites, signaling a deliberate evolution from opportunistic data theft toward organized extortion.
Lately, SLSH’s growing visibility also drew opportunistic actors who began exploiting its notoriety by falsely claiming membership, leading to an uncontrolled proliferation of Telegram channels and transforming SLSH into a sort of cybercriminal brand.
This investigation traces the origins and communication strategy of SLSH, showing how a single extortion campaign evolved into a viral online brand that fused marketing, imitation, and spectacle into one of the most confusing threat phenomena of 2025.
Although law enforcement operations have successfully led to the arrests over the years of many members of cybercriminal clusters related to SLSH, the continued reuse of the same usernames and PGP private keys used to sign and authenticate activity sustains the illusion of an enduring and invincible threat. The PGP key observed in these communications is the same one linked to the ShinyHunters account on RaidForums, dating back to at least 2023, indicating that it was either transferred or recovered after the arrests of the other members.
A Chaotic but Persistent Communication Campaign
Without counting Telegram chats, at least 25 Telegram channels claiming to be linked to SLSH have been created between August 8th and October 17th 2025. Among them, our research estimates that only 12 were tied to the genuine SLSH cluster, while others were run by impersonators.
Both genuine and impersonator channels were regularly banned which forced threat actors to recreate new Telegram channels with their lifespan greatly varied from a single day to a few weeks for the most resilient ones.
Since the detention of Telegram CEO Pavel Durov’s in France on 24th August 2024, the platform has started to ban Telegram channels and accounts involved in cybercriminal activity faster. The constant banning added even more to the already chaotic nature of communication of SLSH but also demonstrated their will to continue to spread their message and highlighted their persistence.
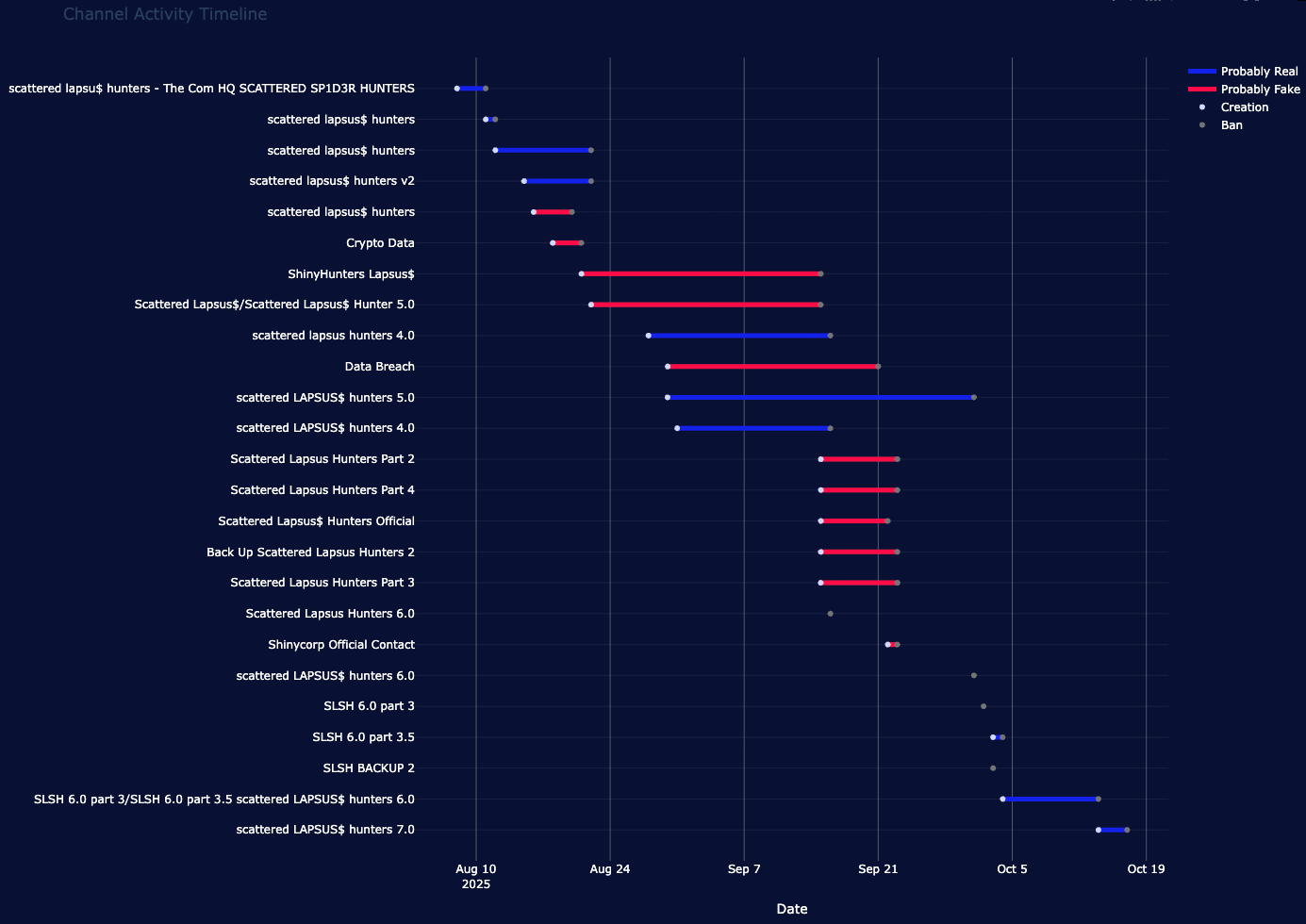
Telegram channels associated with SLSH or impersonating them, August-October 2025 (Source: Flare)
Inside the “real” SLSH Telegram channels, the communication style was often juvenile and openly mocked both law enforcement and the cybersecurity community. For example, on August 11th, 2025, the threat actors themselves referred to their own discussions as “retarded shit,” expressing derisive pity for what they believed was a law enforcement officer forced to monitor their activity.
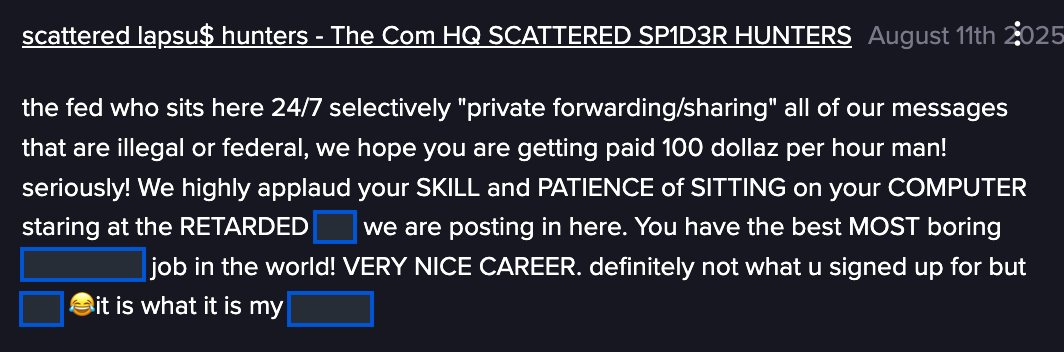
SLSH mocking law enforcement (Source: Flare)
Beyond the many unverified claims that should be treated with caution, one probable impersonator SLSH channel asserted responsibility for the Jaguar Land Rover intrusion.
In contrast, a genuine SLSH channel shared information that appears to come from the initial Salesforce CRM attacks that Google attributed to UNC6040. This suggests that the threat actors operating the SLSH Telegram group either had access to data taken from those victims or were at least collaborating with the actual perpetrators. This supports the claim made by UNC6240, the cluster responsible for the extortion phase that followed the social engineering campaign, of being linked to ShinyHunters and, as we will see, directly connects the origins of SLSH to that group.
SLSH claimed that they possess an internal database belonging to Victoria’s Secret (Source: Flare)
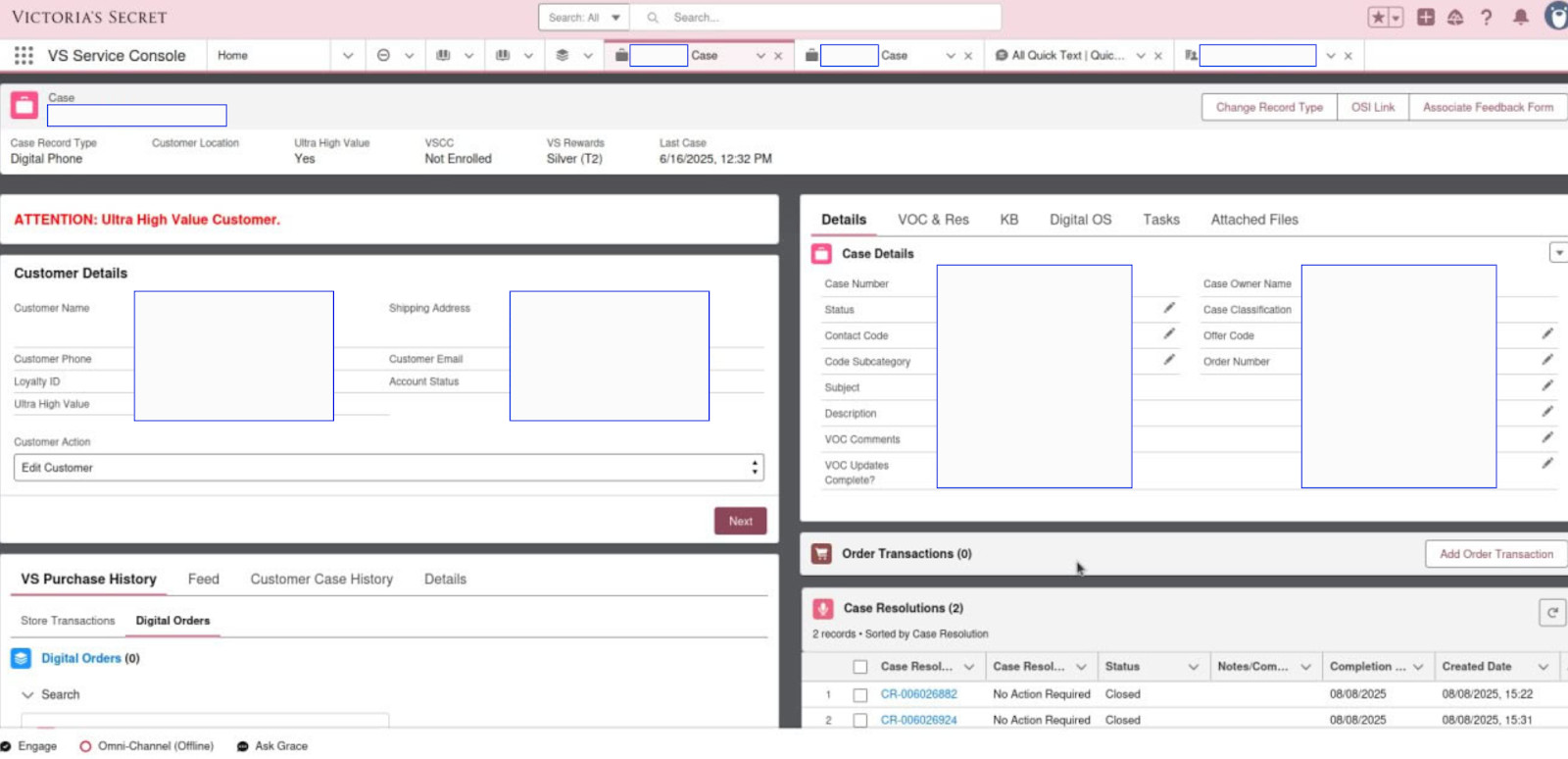
Screenshot shared by SLSH to prove they had access to Victoria’s Secret’s Salesforce CRM (Source: Flare)
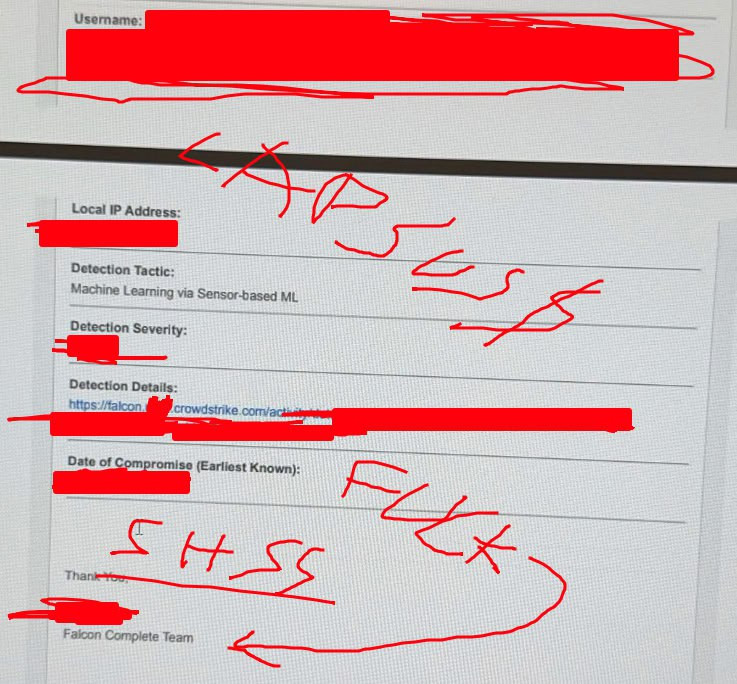
SLSH claimed to have access to the Crowdstrike Falcon solution (Source: Flare)
The goal for SLSH was clearly to display that their extortion and shaming tactic was successful and that engaging them and paying the ransom was the best way to limit reputational impacts.
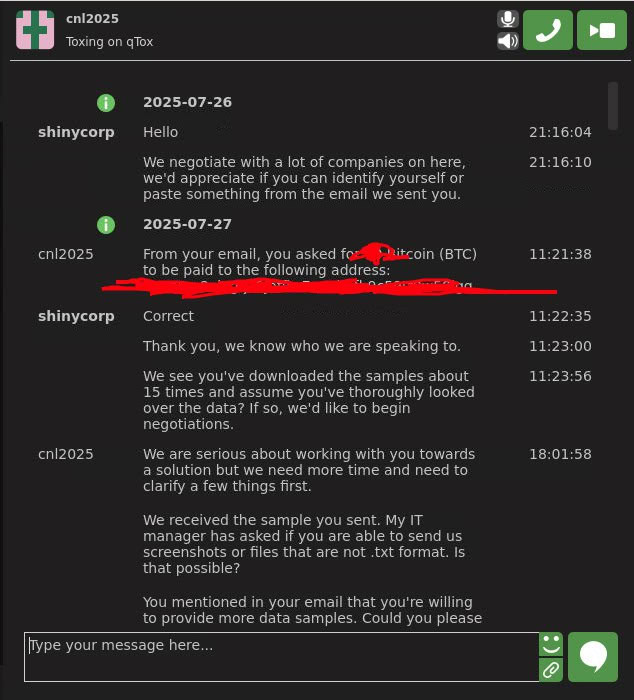
SLSH shared a screenshot supposedly displaying their negotiation through qTOX messenger with a potential victim (Source: Flare)
Between August and October 2025, members of SLSH repeatedly threatened Australian government institutions and companies. A key driver appears to be Australia’s regime that requires organizations to report any ransomware or cyber extortion payment within 72 hours, combined with the risk that some payments may breach sanctions law. Together, these measures limit the leverage and payout prospects for clusters like SLSH.
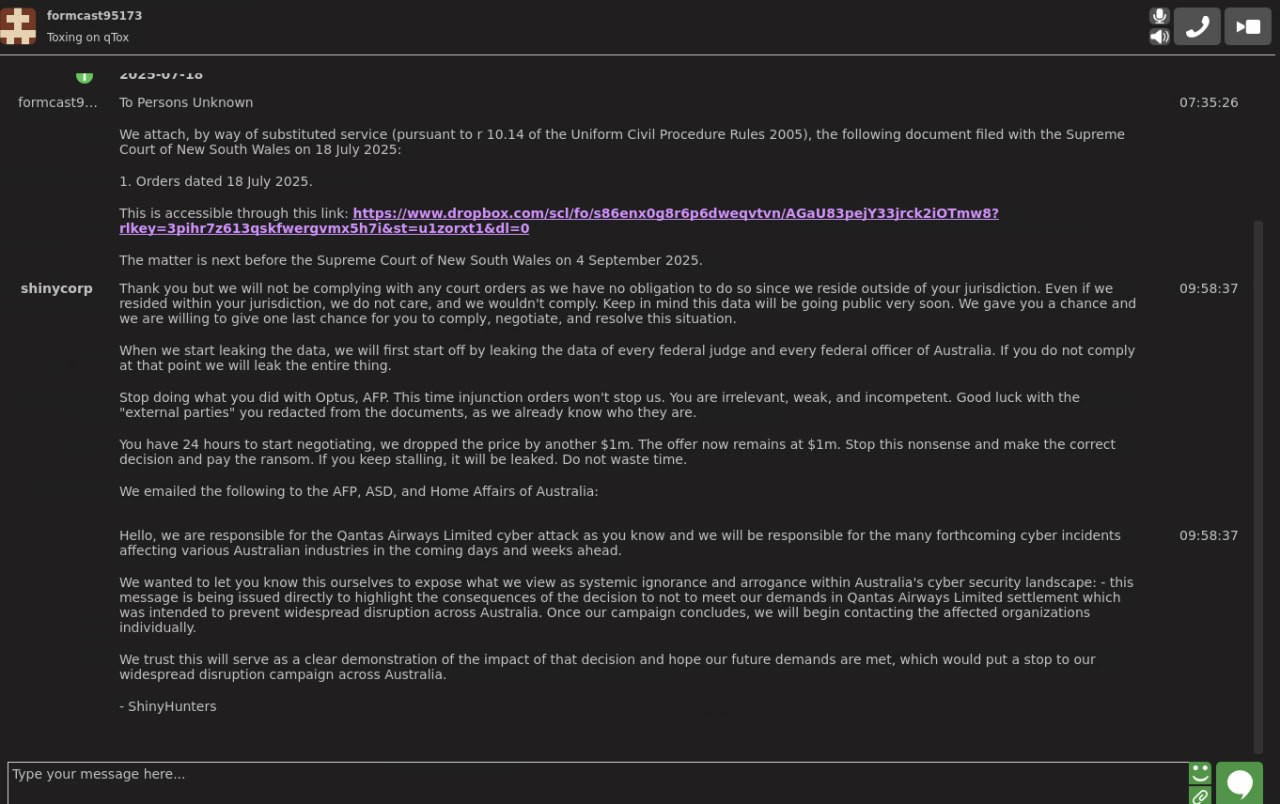
SLSH shared a screenshot supposedly displaying their negotiation with an Australian company (Source: Flare)
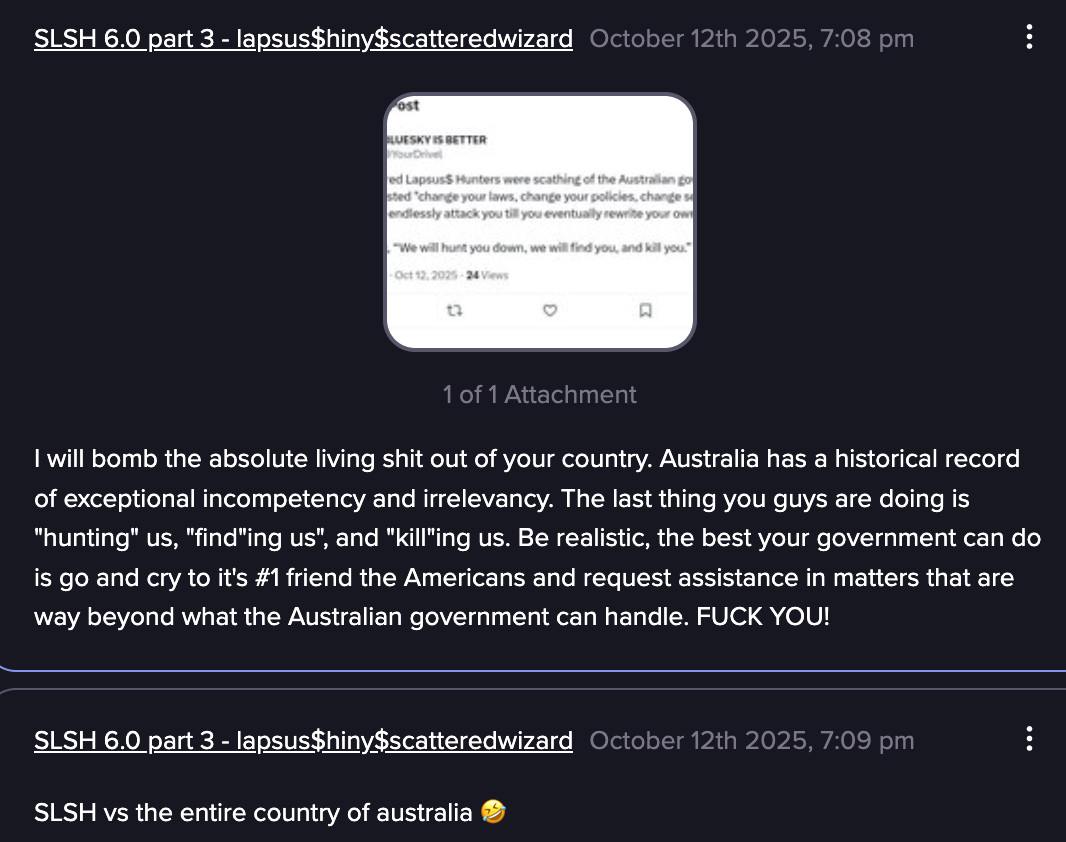
SLSH members expressed frustration in their negotiations with Australian companies (Source: Flare)
The culmination of over two months of activity characterized by victim shaming, chaotic posting, and open provocation of law enforcement and major cybersecurity firms was the launch of an extortion website on October 3rd, 2025. Clearly inspired by ransomware-as-a-service operations, the shaming blog was made accessible both through an onion address and on the clear web, hosted on a domain previously associated with BreachForums.
Before launching this extortion campaign, members of ShinyHunters were among the administrators of BreachForums, a prominent English-language cybercrime forum known for publishing data breaches. Since spring 2025, international law enforcement agencies have carried out several operations against the forum, disrupting it on multiple occasions by seizing domains and backend infrastructure.
On October 10, 2025, members of SLSH stated on the “SLSH 6.0 part 3 lapsus$hiny$scatteredwizard” Telegram channel that BreachForums had been taken over by police and that they did not intend to revive the platform.
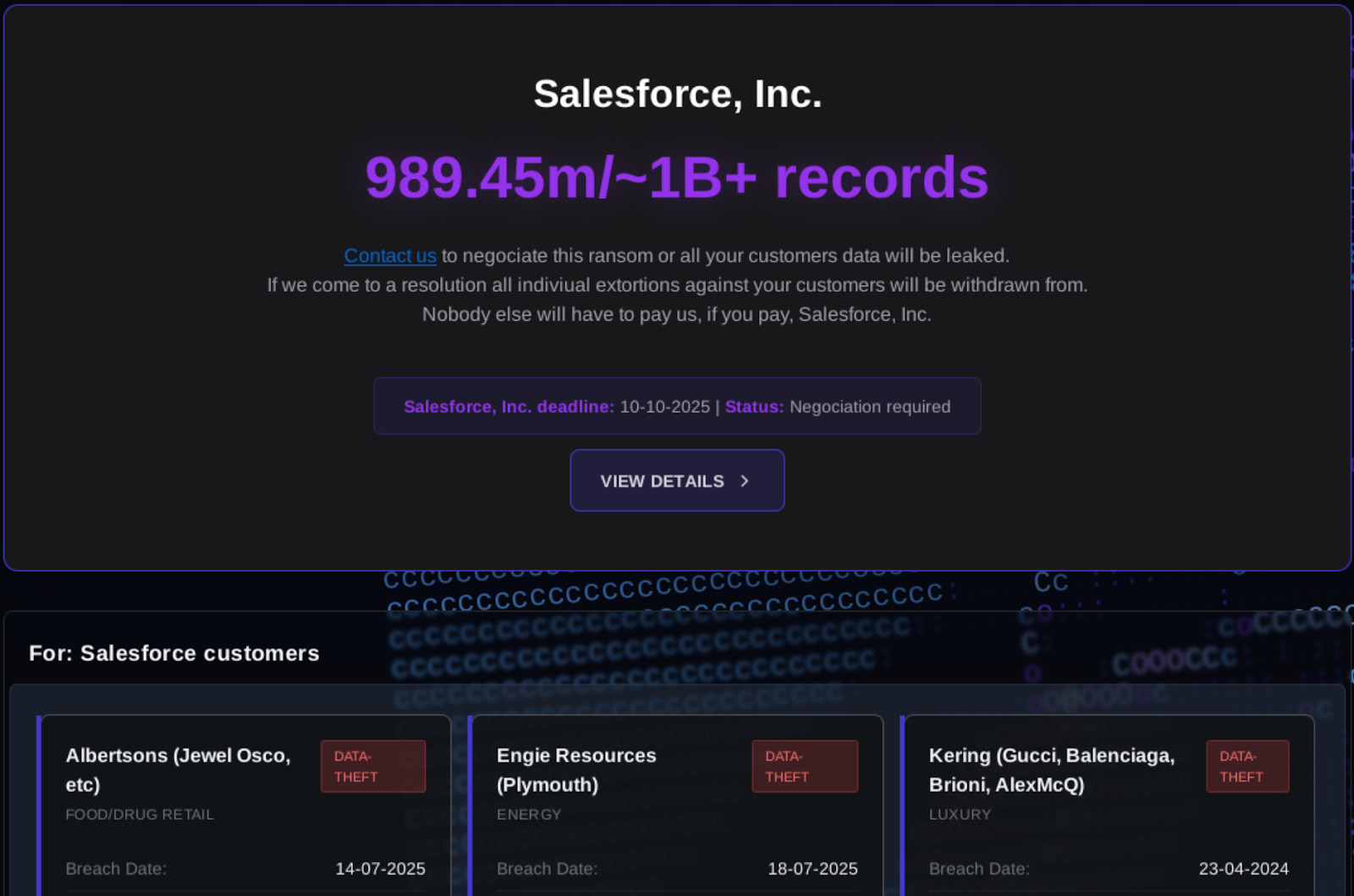
SLSH shaming blog, was accessible on shinyhunte[.]rs, breachforums[.]hn, and shinypogk4jjniry5qi7247tznop6mxdrdte2k6pdu5cyo43vdzmrwid[.]onion.
In its final posts, SLSH claimed to be seeking cooperation with Mexican drug cartels to sell personal data belonging to FBI members. Shortly after, on October 19th, 2025, “sevy”, an actor linked to the cluster, posted on X alleging that “Shiny,” one of the key figures, had been arrested by the police. While this claim needs to be considered with caution, as of today, the group’s communication has gone silent, yet its method of communication and extortion is likely to persist.
SLSH members have threatened to deanonymize US federal employees and sell their personnel data to Mexican drug cartels (Source: Flare)
Inside the SLSH–ShinyHunters Convergence: Structure, Links, and Law Enforcement Fallout
Interestingly, the earliest reference to a Telegram channel combining the names of Scattered Spider, Lapsu$, and ShinyHunters in Flare’s data lake predated this year’s events and dates back to October 2024. At that time, several threat actors were active on a channel named “lapsus$hiny$catteredwizard$pider”, including a user known as “Judische” or “Waifu”, later allegedly identified as Connor Moucka following his arrest in Canada for his involvement in the Snowflake breach.
A closer review of posts from both “lapsus$hiny$catteredwizard$pider” and the genuine SLSH Telegram channels from 2025 shows that they frequently served as the first outlet for PGP-signed messages announcing the end of BreachForums’ operations or commenting on ongoing SLSH and ShinyHunters activities. Verification of these PGP-signed messages suggests that members of the SLSH group were either core members of ShinyHunters themselves or had obtained access to the group’s private PGP key, while the corresponding public key had been originally shared on RaidForums around 2021 on the user profile of the threat actor “ShinyHunters.”
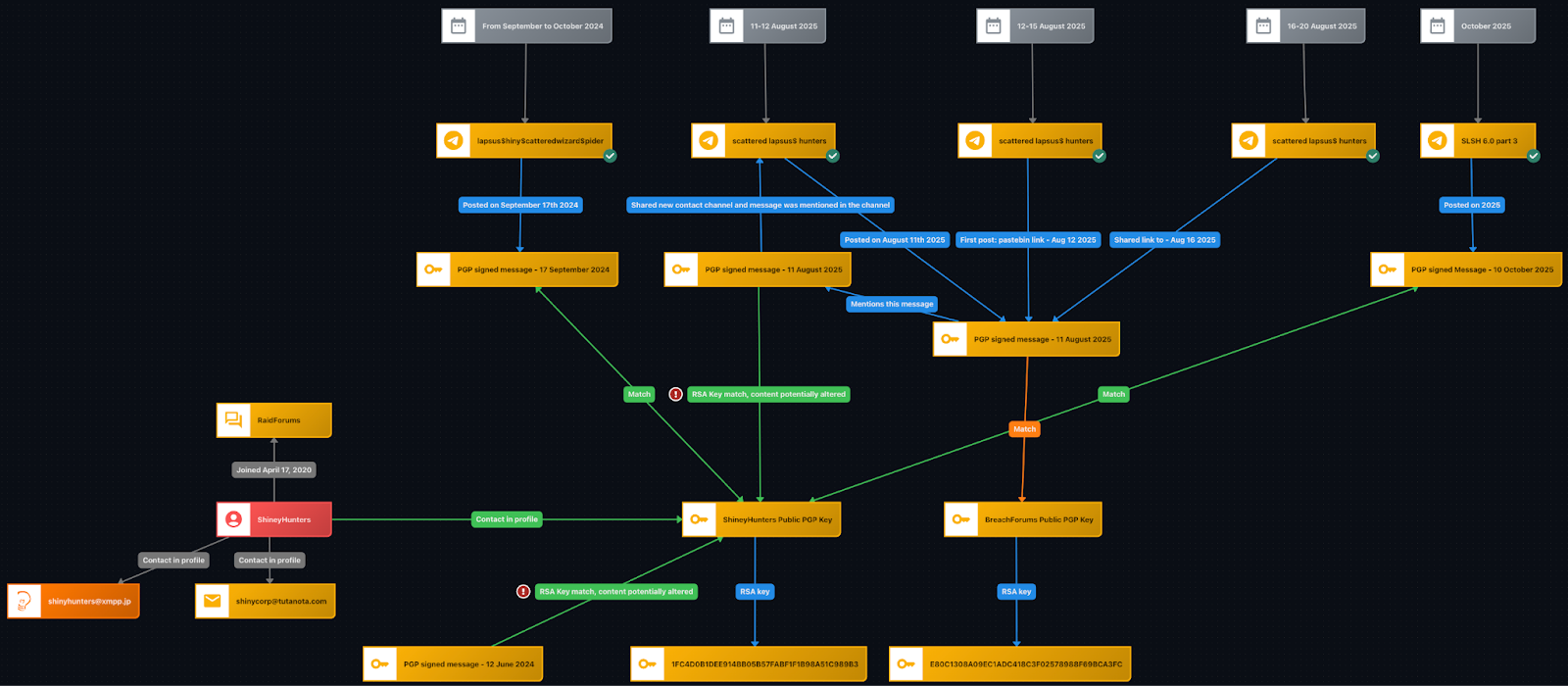
Connections between SLSH channels and ShinyHunters and BreachForums PGP signing keys (Source: Flare)
A key question that naturally arises is how the ShinyHunters group managed to continue its activities despite the numerous arrests that have affected the cluster and associated threat actors in recent years. According to law enforcement, several individuals using the handles “ShinyHunters”, “IntelBroker”, “Hollow”, “Noct”, “g0re”, “Depressed”, and “Sezyo Kaizen”, all in their twenties and associated to different extent with the ShinyHunters group, have been arrested.
Despite these arrests, the law enforcement actions likely disrupted only certain members or specific functions, while others remained active probably because they were outside Western law enforcement jurisdictions. This could be, for instance, the case of the threat actor “rey”, who probably has been deanonymized after infecting himself with an infostealer malware back in 2023. Furthermore, the continued use of shared communication channels and PGP keys supports the idea that operational continuity was ensured through common resources, enabling the brand to persist even after key arrests.
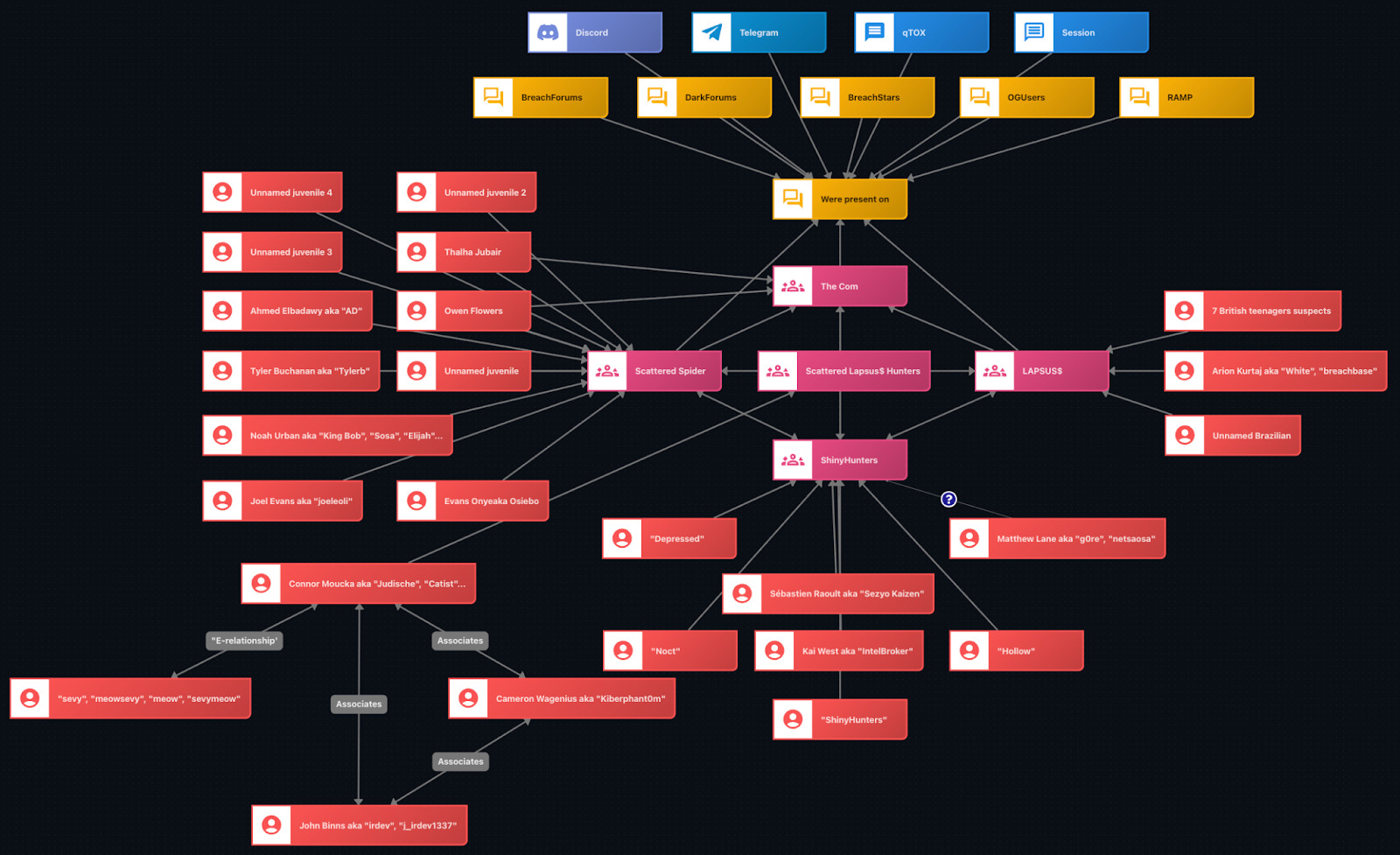
Known arrested members of ShinyHunters, Lapsu$, Scattered Spider and The Com, note that multiple affiliations were not displayed for clarity (Source: Flare)
Scattered Lapsus$ Hunters Copycats?
Although Scattered Lapsus$ Hunters have stopped their public communication, this likely represents a pause rather than a termination of activity. Their operations demonstrated how publicity, intimidation, and selective data leaks can be used to amplify extortion pressure far beyond the technical scope of an intrusion. The model proved effective, simple to replicate, and attractive to other groups seeking visibility.
In September 2025, a newly emerged group calling itself Coinbase Cartel began promoting a data extortion service focused solely on data exfiltration and public exposure, without any encryption component. Their positioning echoed the communication-first strategy pioneered by SLSH: visibility, public shaming, and selective leaks as the main leverage. In October 2025, another group, Crimson Collective, claimed on Telegram responsibility for a breach of Red Hat, shortly before the company confirmed a security incident involving one of its GitLab instances. Once again, the core tactic relied on publicity to maintain pressure on the victim and demonstrate credibility.
Taken together, these developments show that the SLSH approach has already begun to spread and will likely reappear in future attacks under new names and brands, with different levels of technical sophistication but the same underlying strategy: steal data, create panic, maintain visibility, and weaponize public exposure.
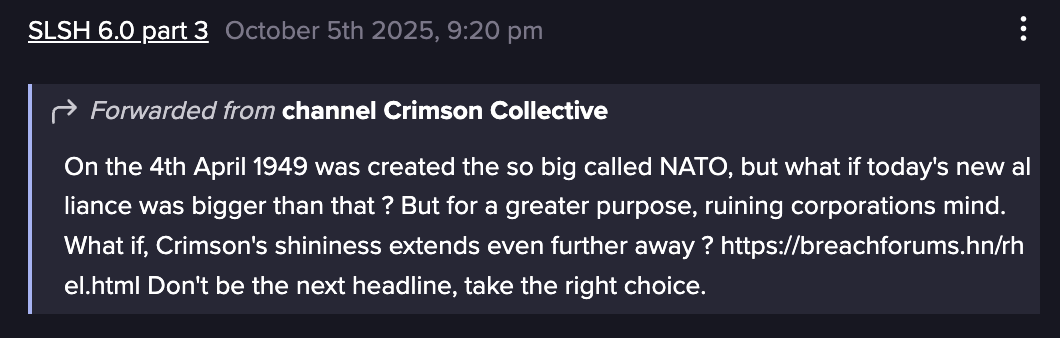
Message from SLSH 6.0 part 3 channel forwarding a post from Crimson Collective proposing a collaboration (Source: Flare)
Observed TTPs
UNC6040 – Initial Intrusion (Salesforce Connected Apps):
- Conducted voice-phishing (vishing) calls impersonating internal IT staff.
- Tricked victims into authorizing a malicious Salesforce Connected App (Data Loader-like) granting OAuth access.
- Used the resulting OAuth tokens to query and extract CRM data.
UNC6395 – OAuth Token Abuse (Salesloft / Drift Integrations):
- Leveraged stolen third-party OAuth tokens from integrations such as Salesloft and Drift.
- Accessed corporate Salesforce instances via API calls without breaching Salesforce itself.
- Performed bulk SOQL queries on key objects (Accounts, Users, Cases) and exfiltrated datasets.
- Cleaned traces by deleting query jobs after export.
UNC6240 – Extortion Phase / Public Claims (“ShinyHunters”):
- Operated weeks to months after data theft.
- Issued extortion messages and leak threats, often signed or branded as ShinyHunters to add pressure.
- Focused on publicity, intimidation, and selective data leaks rather than encryption.
Common Traits Across Clusters
- OAuth abuse instead of malware or encryption:
- Threat actors consistently relied on social engineering and OAuth token abuse to gain API-level access to Salesforce data.
- No file encryption or ransomware payloads were reported in UNC6040 or UNC6395 operations, the model was pure data theft followed by extortion.
- Tor and commodity cloud infrastructure:
- Both UNC6040 and UNC6395 used Tor exit nodes, VPN services (e.g., Mullvad), and cloud providers such as AWS or DigitalOcean to conceal their origins and stage exfiltrated data.
- Credential and API key hunting inside stolen data:
- After exporting large Salesforce datasets, UNC6395 actors searched for embedded secrets such as AWS access keys and Snowflake tokens to enable further access or resale.
MITRE ATT&CK Techniques
- Spearphishing Voice — T1566.004
- Steal Application Access Token — T1528
- Use Alternate Authentication Material: Application Access Token — T1550.001
- Access Token Manipulation — T1134
- Multi-hop Proxy (Tor) — T1090.003
- External Remote Services / Tor hidden services — T1133 (and related software listings)
- Exfiltration Over Web Service / Exfiltration to Cloud Storage — T1567, T1567.002
- Automated Exfiltration — T1020
- Credentials in Files — T1552.001
- Valid Accounts — T1078

