
Threat Intelligence provides organizations with timely, relevant information about threats to their business. Threat intelligence can come in many different forms and includes four primary layers, strategic threat intelligence, tactical threat intelligence, operational threat intelligence, and technical threat intelligence. Organizations with mature threat intelligence functions in place are able to effectively collect intelligence from hundreds of sources, effectively integrate technical indicators of compromise into security operations workflows, and incorporate strategic threat intelligence into decisions about enterprise risk management.
This article will outline how threat intelligence is used by organizations, cover the threat intelligence lifecycle, and provide detailed guidance on where organizations can find specific sources of threat intelligence.
How is Threat Intelligence Used by Organizations?
Many different units within an organization can make effective use of threat intelligence from the board level down to security operations centers and red teams. The significance of the role that threat intelligence plays in specific organizations’ security programs is typically highly dependent on the organization’s security maturity. It’s worth noting that threat intelligence can be integrated at all levels of a company from ingesting technical feeds into SIEM tools to informing board-level decision making about cybersecurity funding and direction. Here are a few common use-cases:
- Organizations employing open source information about vulnerabilities that affects enterprise software systems that they use such as CISA’s known exploited vulnerabilities catalog
- Organizations bringing in threat intelligence specialists to advise decision makers and boards on key strategic threats facing their organization in relation to geopolitics, cybercrime, and supply chain risk
- Threat Intelligence being used to inform patch prioritization for enterprise systems based on cybercriminal exploitation activity
- Threat intelligence from monitoring illicit communities on the dark web to identify targeted attacks and indicators of compromise
- Organizations can base security policies, procedures, and training to build the most effective defense based on threat information specific to their sector and known cybercriminal tactics, techniques, and procedures
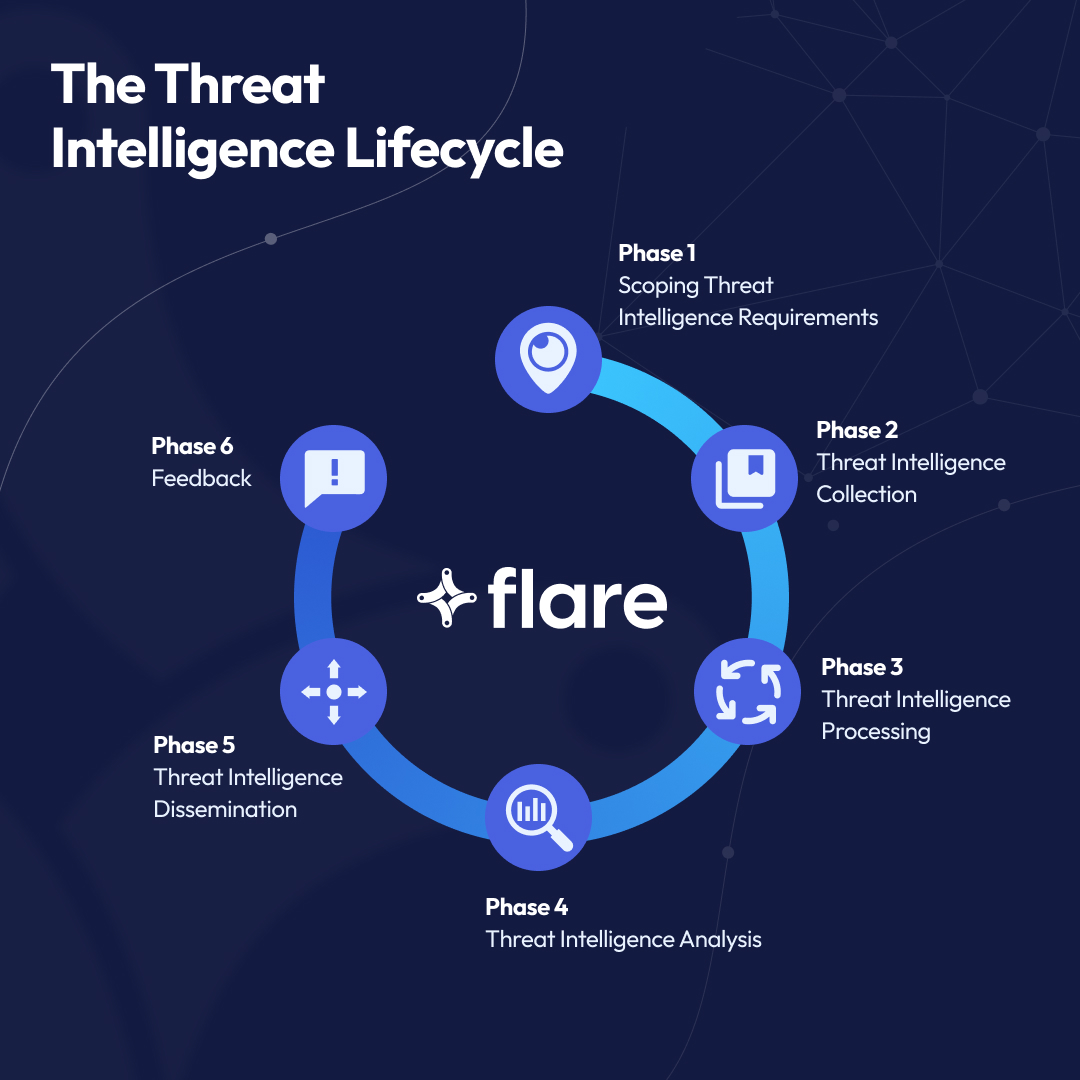
Understanding the Threat Intelligence Lifecycle
Threat intelligence doesn’t operate in a vacuum, CTI teams are typically assigned to specific tasks and investigations based on business requirements. CTI teams then progress through a lifecycle of activities that enables them to clarify requirements, collect and process data, analyze structured information, and disseminate actionable intelligence to relevant business units.
The CTI Lifecycle for most organizations consists of six distinct stages that CTI teams complete when tasked with a specific task or investigation. These include:
- Scoping Requirements: During this stage the CTI team takes the time to understand business requirements. In many cases CTI teams will receive specific questions which they will seek to answer, these questions should translate into actionable data that can be used to reduce risk or inform strategic decision making.
- Threat Intelligence Collection: During threat intelligence collection the CTI team will identify and begin collecting raw data from various sources. The nature of collection depends specifically on the requirements outlined during the scoping requirements phase. Sources could include cybersecurity OSINT sources such as dark web markets, forums, cybersecurity news sites, or even geopolitical analysis.
- Threat Intelligence Processing: During this stage threat intelligence collected during the collection stage is processed. This may include data structuring, correlation, and contextualization with the primary focus being to prepare the data for more rigorous analysis.
- Threat Intelligence Analysis: During this phase data is analyzed based on business objectives in order to drive actionable intelligence that can be used for risk reduction and strategic decision making.
- Threat Intelligence Dissemination: During this phase finished threat intelligence is sent or presented to key business units or individuals based on business objectives defined during the scoping phase. Dissemination can take the form of alerts, briefings, or written reports.
- Threat Intelligence Feedback: During this phase of the threat intelligence lifecycle feedback is gathered from key stakeholders to identify whether the finished intelligence provided met business and risk objectives, and areas where the CTI team can improve in the future.
Types of Threat Intelligence
Threat intelligence can broadly be broken down into four categories which we will cover in turn.
Strategic Threat Intelligence
Strategic threat intelligence is focused on collecting, processing, analyzing and disseminating intelligence that can be used to inform decision making. Here are a few examples of how organizations can use strategic threat intelligence to shape their information security and risk management postures.
Examples of Strategic Threat Intelligence
- An enterprise financial institution tasks a CTI team with researching cyber risks stemming from the Russia-Ukraine conflict. The CTI team conducts extensive research on Russian APTs, Ukrainian APTs, cyber supply chain risk, and presents a report to the board of directors and key executives. This information is used to make decisions about how to do business with entities that may come under sanction, and how much to invest in advanced cybersecurity solutions to reduce risk from APT groups.
- A large hospital chain tasks a CTI team with providing guidance related to ransomware groups targeting healthcare organizations. The findings are presented to the CISO and risk management teams which are then used to guide decision making on purchasing backup and recovery solutions and enhancing incident response plans.
- An enterprise computer hardware threat intelligence team is tasked with building a risk report on how geopolitical risks from increasing tensions between the United States and China could affect supply chains. The team builds a report showing third-party vendors that are reliant on supply chains based in China which helps inform the organization’s third-party risk management and business continuity planning.
Strategic threat intelligence is critical for organizations to guide investments into the right types of people, processes, and technologies that effectively mitigate risk across the enterprise. CTI teams need to be careful to provide adequate context and ensure that information presented is actionable for the stakeholders it is presented to.
Tactical Threat Intelligence
Tactical threat intelligence provides security operations teams and executives with key insights on how the tactics, techniques, and procedures used by threat actors can launch attacks, escalate privileges, and compromise valuable data and systems. Correctly collecting, processing, analyzing, and disseminating tactical threat intelligence data is a core component of an effective cyber threat intelligence program. Here are some examples of how tactical threat intelligence can be used to disrupt cyber adversaries and improve organizational security:
Examples of Tactical Threat Intelligence
- A healthcare CTI team is tasked with investigating TTPs used by a specific ransomware group targeting the healthcare sector. The CTI team identifies that initial compromise is typically accomplished through spear phishing emails. This leads the CISO to mandate additional training for key executives on spear phishing while also investing additional money in simulated phishing campaigns and email filtering.
- The CTI team at a large political party is tasked with identifying the TTPs that nation state actors have used in the past to compromise sensitive information. The team is able to identify several variants of malware that have been used in the past to compromise networks and computers. This data is used to increase the sensitivity of network anomaly detection.
Tactical threat intelligence can prove invaluable for helping drive cybersecurity spend to reduce specific risks based on how your organization is most likely to be targeted.
Operational Threat Intelligence
Operational threat intelligence is related to threats that are specific to an organization based on their specific infrastructure, assets, data exposure and vulnerabilities. Operational CTI is typically considered to be highly actionable and is highly relevant to an individual organization. For example, here are some examples of operational intelligence:
Examples of Operational Threat Intelligence
- A CTI team is tasked with identifying software applications that the organization uses that may have unpatched vulnerabilities. The CTI team compiles a report of the most at-risk applications and presents them to the vulnerability management team.
- A CTI team consistently monitors infected device markets such as Russian & Genesis markets for devices for sale with internal subdomains which could indicate a company computer infected with stealer malware.
- The CISO of an organization requests that corporate leaked credentials be identified on the dark web. The CTI team uses a platform to identify leaked credentials and reach out to specific employees to change their passwords.
Operational threat intelligence often results in rapid risk identification & reduction and is generally focused on providing security operations teams with highly actionable information on specific risks or events that need to be actioned. Operational threat intelligence should be tightly integrated with security operations and vulnerability management teams.
Technical Threat Intelligence
Technical threat intelligence involves the collection, processing, and analysis of highly technical data that can be used to reduce risk. There are dozens of types of technical threat intelligence that an organization could ingest including stealer logs, IOC feeds (lists of specific high-risk IPs and domains), CVE data, and other specific technical data. Here are a few examples of how technical threat intelligence is commonly used:
Examples of Operational Technical Threat Intelligence
- A threat intelligence team ingests IOC feeds from dozens of different government and private sector sources in concert with security operations. These feeds are then fed into the firewall to automate blocking rules.
- A CTI team ingests thousands of stealer logs from illicit Telegram channels to identify IOC’s related to infected devices to provide to the incident response team.
- A CTI team ingests CVE vulnerabilities to compare against corporate applications to provide the vulnerability management team with a list of priorities.
Technical CTI data can often provide supporting information for operational, tactical, and strategic threat intelligence initiatives while also helping to detect and reduce specific risks.
Threat Intelligence Sources
There are innumerable sources of threat intelligence for organizations. The specific sources chosen will likely depend on the type of threat intelligence being gathered and the specific scope of the project or process. Here are a few of the primary sources:
Dark Web Sources of Threat Intelligence
The dark web is a network available through TOR (The Onion Router) and is used by groups around the world ranging from political dissidents in authoritarian countries to ransomware groups. TOR provides a high degree of anonymity making it perfect for cybercriminals to congregate, plan, and act together. The dark web hosts a vast underground supply chain that facilitates cybercrime, as such it is an incredible source of threat intelligence. Here are a few main areas of the dark web that are good for collection threat intelligence:
- Infected Device Markets such as Russian & Genesis markets that sell access to computers infected with stealer malware. These listings often contain browser fingerprints which can be used to bypass 2FA and MFA as part of a session replay attack.
- Stolen Credentials: Credentials stolen from organizations often appear in named leaks, combolists, and are given out for free to build threat actor reputation. Identifying employees that have been listed as part of a combolist can be a way to rapidly identify a potential high-risk targeted attack.
- Ransomware Dumps: Recently ransomware groups have begun exfiltrating stolen data as part of triple extortion ransomware schemes. They then dump this data on dedicated dark web pages where anyone can download it. In many cases the data will contain sensitive intellectual property, financial statements, and other high-risk data.
- Bonus Tip: Flare is one of the only threat intelligence platforms that automatically monitors ransomware dumps for company domains and brand names, and can even enable seamless downloading of specific files containing high-risk exposure.
- IAB Forums: Certain threat actors called “initial access brokers” sell access they have gained to corporate IT environments on dedicated forums, in many cases using an auction format. Monitoring these sources can provide an excellent source of operational threat intelligence and potentially even IOC’s.
The dark web represents an excellent source of potential threat intelligence, however many markets and forums require validation or payment. In addition, the TOR network is known to be extremely slow, making dark web threat intelligence collection arduously slow.
Bonus Tip: Flare’s threat intelligence platform has archived the dark web going back five years to make it easy for CTI teams to search and alert on structured, actionable dark web data from thousands of posts, marketplaces, and forums. Try it yourself with our Free Trial (no sales call required).
Government Sources of Threat Intelligence
The U.S. and international governments regularly publish threat intelligence ranging from strategic intelligence to tactical and technical. Below are a few common sources for organizations to collect threat intelligence directly from government bodies:
- Cybersecurity and Infrastructure Security Agency (CISA): CISA is a U.S. government agency that works to protect the nation’s critical infrastructure from cyber threats. It provides a variety of threat intelligence products and services, including alerts on cyber threats, guidance on mitigating vulnerabilities, and reports on cyber incidents. CISA’s analysis reports provide an excellent source of tactical and strategic threat intelligence for enterprise security teams.
- CISA Automated Indicator Sharing: CISA (U.S. government’s Cybersecurity & Infrastructure Security Agency) runs a program called Automated Indicator Sharing which provides organizations with intelligence sharing using the STIX format to empower collaborative cybersecurity.
- U.S. Computer Emergency Readiness Team (US-CERT): US-CERT is a division of CISA that provides several threat intelligence feeds to include alerts, advisories, and announcements.
- National Institute of Standards and Technology (NIST): NIST is a U.S. government agency that develops and promotes cybersecurity standards, guidelines, and best practices. It provides numerous publications on threat intelligence that can provide value to CTI teams and enterprise risk management including: NIST SP 800-150 Guide to Cyber Threat Information Sharing, NIST Cybersecurity Framework, and NIST 800-53.
- Federal Bureau of Investigation (FBI): The FBI provides bulletins related to cyber threats including APTs, ransomware groups, and other risks. The FBI’s official statements and alerts can be found here.
IOC Feeds & Private Threat Intelligence
- Cyber Threat Alliance (CTA): The Cyber Threat Alliance is a nonprofit organization that promotes cyber threat sharing and information between companies in the cybersecurity field.
- Open Threat Exchange (OTX): OTX is a community-driven platform for sharing and collaborating on cyber threat intelligence. More than 100,000 members across threat intelligence, security operations, and security research participate.
- SANS Internet Storm Center (ISC): The SANS internet storm center monitors internet security broadly, with a particular focus on large scale infrastructure events.
- OPENIOC: A free to use platform developed by Mandiant and currently managed by FireEye for sharing and distributing indicators of compromise.
Open Source Threat Intelligence
- Open Source Intelligence (OSINT) frameworks: OSINT frameworks can provide invaluable guidance for security teams on collection and analysis methodologies for open source intelligence.
- Cybersecurity news and blogs: Cybersecurity news and blogs are a good source of information on current and emerging threats. Some examples of sites we like at Flare are Bleepingcomputer, Darkreading, and Krebs on Security.
- Government and industry reports: Government agencies and industry organizations often publish reports on cyber threats and trends. For example, the Verizon Data Breach report is an excellent source of information about current TTP’s being used by malicious actors, and how threat actor tactics are changing over time.
- Vulnerability databases: Vulnerability databases, such as the National Vulnerability Database (NVD) and the Common Vulnerabilities and Exposures (CVE) database, provide information on known vulnerabilities and can be a source of open source threat intelligence.
Simplify Threat Intelligence with Flare
Flare’s platform automates threat intelligence collection across the dark & clear web, and cuts down noise by about 40% with high-quality structured data. Flare sets up in minutes and can start providing actionable data to reduce risk in the first hour. Request a demo or start your free trial today.





