This article was updated on July 18th, 2025.
Telegram has become one of the most important outlets for cybercriminals in recent years. There are more than 50,000 cybercrime focused groups and channels on Telegram offering almost any type of criminal service you can imagine. In recent years threat actors have even begun using Telegram’s API to leverage it as the backend for cybercrime.
Monitor Telegram Threats in Real Time
Cybercriminals use Telegram to trade stolen credentials and coordinate attacks. Flare monitors thousands of illicit channels—so you can detect threats before they impact your organization.
Telegram Monitoring for Cybersecurity: Brief Overview
What types of Cybercrime occur on Telegram?
Telegram has become a popular platform for many different flavors of criminals. In fact the ecosystem is so vast that threat actors often engage in custom branding of Telegram channels in order to differentiate. Telegram originally rose to prominence as a result of extraordinarily lax moderation for illicit activities, claims of E2E encryption, and the ability to share significant files on free plans, allowing cyber criminals to easily distribute data. Here are a few of the most common types of illicit activity we see on Telegram:
Telegram Refunding Channels
Refunding has become a popular low-stakes way for threat actors to make small to moderate sums of money by scamming major ecommerce companies. The scheme typically works by purchasing high-value items legitimately, then contacting customer support with fabricated claims—such as packages never arriving, items being damaged, or boxes containing the wrong product—to obtain refunds while keeping the merchandise. Some threat actors offer “refunding as a service,” charging customers a percentage of the item’s value to execute the scam on their behalf using social engineering scripts and insider knowledge of retailer policies.

Telegram Stealer Log Channels
Perhaps the most significant threat to enterprises, stealer log channels distribute credentials harvested by infostealer malware like RedLine, Raccoon, and Vidar. These channels often operate on a freemium model—posting free samples to attract buyers while selling premium “private” logs through separate paid channels or bot shops. A single stealer log can contain dozens of saved passwords, session cookies, and autofill data from a compromised device.
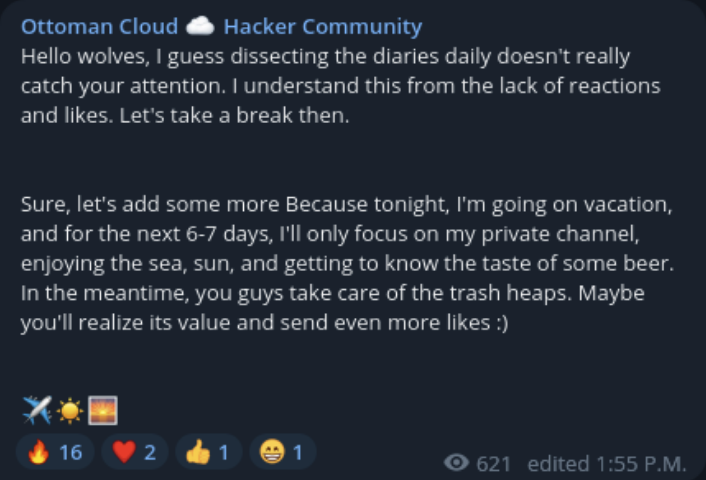
Telegram carding Channels
Credit card fraud remains a staple of the Telegram criminal economy. Carding channels sell stolen payment card data, often organized by bank, country, or card type. Some channels specialize in “fullz”, complete identity packages that include not just card numbers but also billing addresses, SSNs, and other PII needed to bypass fraud controls.
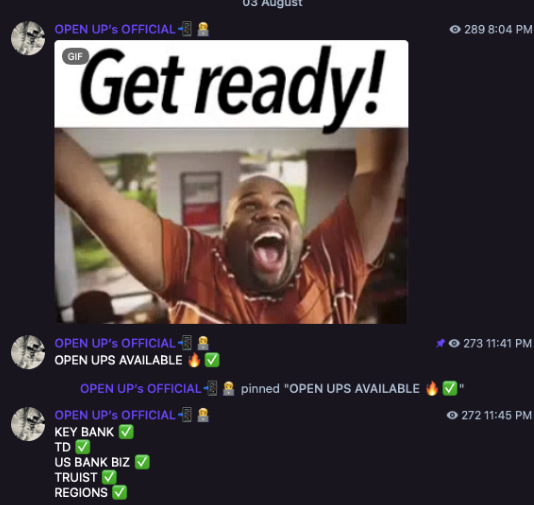
Telegram Account Shops
These channels sell access to compromised accounts across streaming services, gaming platforms, food delivery apps, and more. While individually low-value, account shops operate at massive scale and often serve as entry points for newer cybercriminals looking to learn the trade.
Telegram Credentials & Combolist Channels
Threat actors share and sell large compilations of username/password pairs aggregated from multiple breaches. These combolists fuel credential stuffing attacks and are often tailored to specific platforms or industries.
Telegram Fraud and Scam Guides
Many channels function as informal training grounds, offering step-by-step guides on everything from phishing kit deployment to money laundering through cryptocurrency. These “methods” channels help lower the barrier to entry for aspiring cybercriminals.
Telegram Monitoring Best Practices
Essential capabilities for comprehensive coverage of illicit Telegram activity
Essential Monitoring Capabilities
Real-time ingestion of messages across thousands of illicit channels
Automated parsing of stealer logs for credential extraction
Domain monitoring to detect when your assets appear in threat channels
Historical search across archived channel data and messages
Threat actor tracking across channels and aliases
Actionable alerts with context for rapid remediation
Illicit channels monitored
Continuous monitoring
Average detection time
Why Telegram Monitoring Matters
Telegram has become a primary distribution channel for stolen credentials and cybercrime services. Without visibility into these channels, security teams are blind to threats until they materialize as breaches.
Has Telegram’s policy changes affected cybercriminal activity?
After CEO Pavel Durov’s arrest, Telegram announced it would increase cooperation with law enforcement regarding cybercriminal activity on its platform. In January 2025, Telegram updated its privacy policy regarding law enforcement activities. If Telegram received a valid order, it would share a user’s IP address and telephone number.
Some cybercriminals discussed leaving Telegram after this privacy policy update. However, it’s hard to find a different platform that is widely available like Telegram. Our research shows that platforms like qTOX remain niche messaging apps.
Signal is the only messaging platform that had a slight uptick after Telegram’s policy changes. It remains a marginal messenger though. Discord and Session have more usage as they are the second and third most popular platforms. But Telegram still reigns supreme as the most used messaging platform for cybercriminals.
Telegram’s policy changes didn’t have a huge impact on cybercriminal usage. It’s still the most popular messenger by a long shot.
Why are cybercriminals still using Telegram?
If law enforcement investigates Telegram channels, the platform can only share limited information about someone’s identity since it never collected information on it. Telegram doesn’t require a name, gender, age, or other personally identifiable information (PII) when one registers.
The only identity-based data Telegram collects are IP addresses and phone numbers. Cybercriminals can circumvent this by using blockchain-purchased phone numbers to sign up for Telegram. The anonymous phone numbers can make it hard for law enforcement to track.
In addition, Telegram is highly popular with over 1 billion monthly active users. It’s accessible and free. Cybercriminals like using Telegram because there’s no need to use the dark web to connect to their peers.
The platform also has Secret Chats for enhanced privacy that include features like:
- No forwarding of messages.
- Anyone can delete messages.
- A “self-destruct” timer that deletes messages after they are seen.
- Outsiders can’t see content.
Secret Chats are also not stored in the Telegram cloud. Messages are stored locally on devices with end-to-end encryption. Telegram claims that it doesn’t have the ability to see content or share it with authorities. Even logs are unavailable after a short period of time.
Telegram’s focus on privacy and secrecy makes it attractive to cybercriminals. The platform claims all chats are private and only visible to participants. Since Telegram has no visibility into these chats, cybercriminals can still hide their identities and activities.
Why Telegram Monitoring for Cybersecurity Is Especially Relevant Now
Why do you need Telegram monitoring in today’s cybersecurity landscape?
Telegram remains a hub for cybercriminal communication. As cybercriminals adopt modern, subscription-based business models, Telegram makes sharing data and files anonymously easier for the different parties involved, like:
- Ransomware groups: Organized criminal groups that create and distribute ransomware (Telegram has
- Stealer log channels that sell access to logs containing all of a victims information & credentials harvested from their web browser
- Initial access brokers (IABs): Threat actors selling stolen credentials or other ways of gaining access to target systems
Even though Telegram remains the top messaging app for cybercriminals, it’s important to note that many of them use multiple messaging apps. Accessibility is key for buying and selling subscriptions and compromised credentials. Bad actors are often spread out on multiple messaging platforms to reach more people.
Telegram monitoring is crucial. Organizations will benefit from having comprehensive monitoring of all dark web forums, marketplaces, and messaging channels.
How does Telegram monitoring fit into your threat intelligence program?
Threat intelligence continuously monitors and provides real-time insights into an organization’s threat landscape. It leverages open-source intelligence (OSINT) to improve security procedures and validate security controls. Many channels are publicly available, and security teams can perform Telegram OSINT investigations.
Security analysts can gain valuable insights about their cyber threat exposure by monitoring Telegram and other cybercrime communities. They could learn about:
- Geopolitical context that impacts their cyber risk profile (like hacktivists targeting specific geographic regions).
- Zero-day exploits and new vulnerabilities.
- Targeted companies or industry verticals.
Why does automating Telegram monitoring improve security?
Manually monitoring illicit Telegram channels is time-consuming. Flare tracks over thousands of cybercrime communities and more groups are created all the time. Manual monitoring is too resource-intensive for many security teams.
By automating the Telegram monitoring process, security analysts:
- Reduce the time spent reading posts and chats.
- Gain context by aggregating clear, deep, and dark web intelligence with Telegram posts.
- Translate posts into English, including languages like Russian, Arabic, Spanish, and French.
- Create curated, focused intelligence based on their objectives.
- Reduce noise with high-fidelity, actionable intelligence that improves key security metrics like mean time to detect (MTTD).
- Integrate insights into daily activities and other security risk management technologies like security information and event management (SIEM) tools or ticketing systems.
Security teams should particularly focus on stealer log channels. A single stealer log can enable a threat actor to directly access critical enterprise systems and even bypass 2FA controls.
Flare and Telegram Monitoring for Cybersecurity
How does Flare enable Telegram monitoring?
Flare actively monitors Telegram and searches for new illicit channels as they appear. Our analysts track these channels to understand how they contribute to and accelerate the evolving cybercrime landscape. Flare’s platform monitors thousands of cybercrime-related Telegram channels, including those dedicated to combo lists, stealer logs, frauds and scams, and hacking.
How does Flare answer Telegram monitoring use cases?
Flare AI translates languages like Russian, Arabic, Spanish, and French and creates English summaries. By eliminating the language barrier, Flare enables analysts of all experience levels to understand critical risks and take appropriate actions. With these AI capabilities, Flare can “translate” threat actor jargon and technical cybersecurity intelligence for more business-oriented audiences.
What are the key benefits of Flare’s telegram monitoring?
- Automates monitoring and archiving for thousands of Telegram channels, creating a robust historic database of cybercrime activity.
- Translates foreign languages and contextualizes events so analysts spend less time monitoring and can effectively leverage intelligence.
- Explains complex technical exposure so security professionals can work faster and junior security professionals can understand risk impact.
Telegram Monitoring for Cybersecurity and Flare
Flare provides the leading Threat Exposure Management (TEM) solution for organizations. Our technology constantly scans the online world, including the clear & dark web, to discover unknown events, automatically prioritize risks, and deliver actionable intelligence you can use instantly to improve security. Flare monitors and archives thousands of Telegram channels, enabling your security team to boost your company’s security posture by automating these processes.
Our solution integrates into your security program in 30 minutes to provide your team with actionable intelligence and automated remediation for high-risk exposure. See what external threats on Telegram are exposed for your organization by signing up for our free trial.


