There’s so much to keep up with in the world of cybercrime…especially for security practitioners.
Leaky Weekly is a bi-weekly podcast hosted by security researcher Nick Ascoli as he dives into the most pressing stories on data leaks, cybercrime, and the dark web in the last week or so.
On this episode of Leaky Weekly, Nick covers:
- National Public data breach, and what does “2.9 billion personal records leaked” mean
- FBI “repossessing” the Dispossessor ransomware operation
- A threat actor posting information of Leakbase users to BreachForums
- Two arrests of threat actors who both go by the name “J.P. Morgan”
When a company is possibly the victim of a breach, that may not necessarily be the case for various reasons, such as if threat actors may not actually have the information they claim to. Security practitioners should be supportive of organizations/security teams addressing breaches and never shame them.
Tune in for current events on the podcast on Spotify, on Apple Podcasts, check out the video episode on YouTube below, or keep reading this article for the highlights.
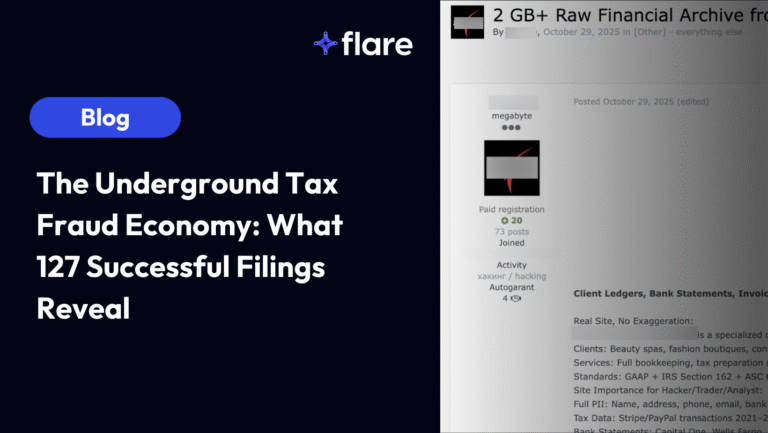
National Public Data Breach
National Public Data (NPD) is a data aggregator that sells background checks, and a threat actor stole 2.9 billion personal records including personal information such as Social Security numbers and home addresses.
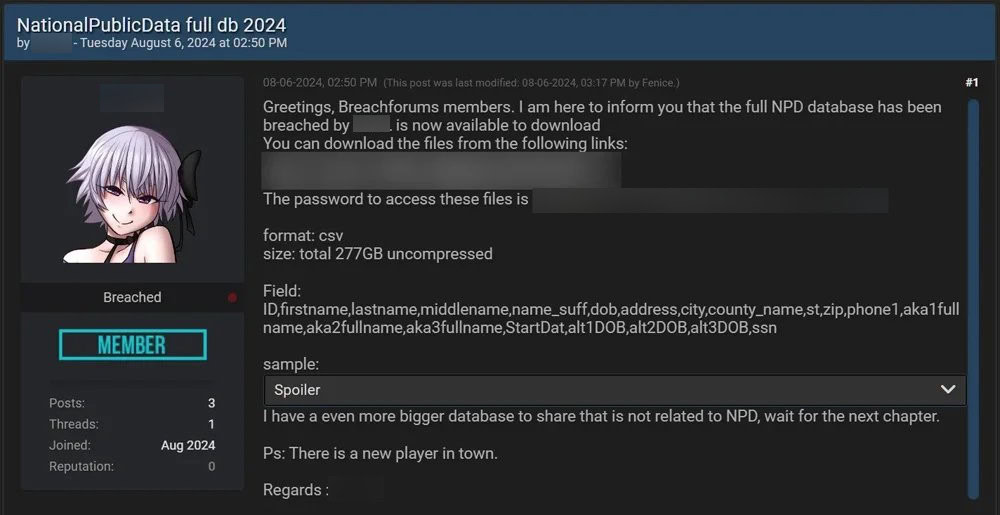
Threat actor on BreachForums posted the NPD leak for free
Your first reaction may be: does this mean personal records of 2.9 billion people across Canada, the U.K., and the U.S.? No. The combined populations of those countries is about 450 million.
So, 2.9 billion people were not affected, but millions of people are still impacted. Security consultant and founder of HaveIBeenPwned Troy Hunt found that one person may be represented multiple times due to repeat addresses. Many of the data points were:
- from deceased people
- repeats with small variations
- incorrect
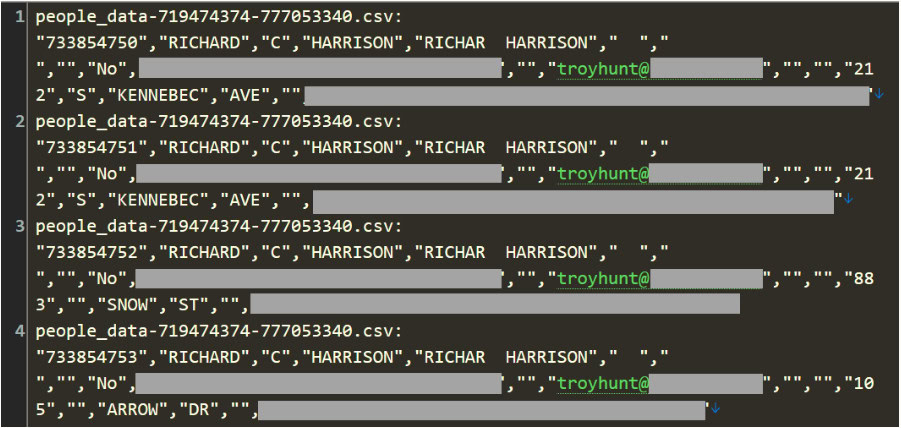
Troy Hunt’s research shows repeated addresses associated with his email
This dataset has been listed before–a threat actor named USDoD posted this in April for $3.5 million, and this past week a different threat actor listed this for free. The threat actor clarified to security researcher Brian Krebs that they didn’t originate the dataset, and it had actually been making the rounds already in smaller cybercrime circles.
There was actually a class action lawsuit forming after the initial leak in April.
People are just now starting to parse through and analyze the information, so it will take some time to fully understand how many people are officially implicated after accounting for inaccurate records, repeat information, and deceased people.
Disposessor Ransomware Operation Repossessed
The FBI “repossessed” the Dispossessor ransomware operation and seized all of its domains.
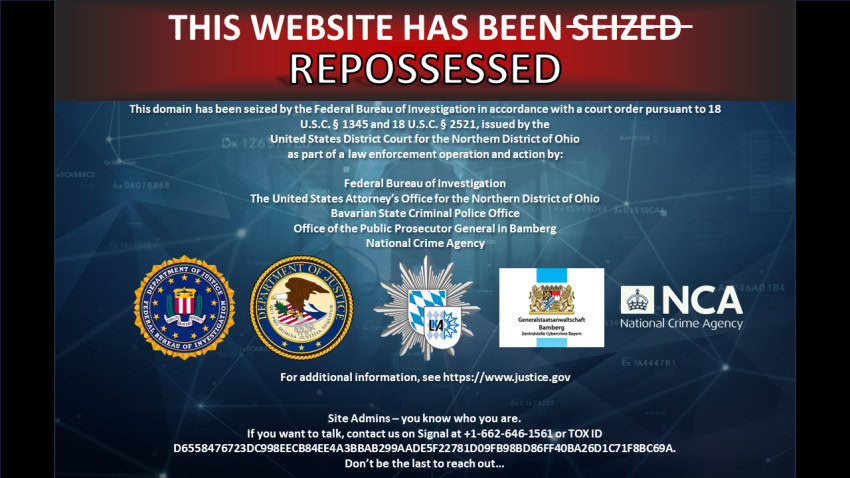
The FBI repossessed the Dispossessor ransomware operation
The site had hundreds of leaks, but the FBI noted in their press release that they found 43 victims of the gang. This means that a majority of the victims posted to the site were reposts from LockBit’s blog and other data leak sites.
What does this mean? Dispossessor was initially an extortion group or even an aggregator, in that they had data listed on their servers, which they could claim was useful since it was no longer subject to the “availability” restrictions of LockBit.
Allegedly, an angry LockBit developer leaked their encryptor, which Dispossessor picked up and started using.
One of the domains seized in the operation was RedHotCypher.com, and an eerily similar domain, RedHotCyber.com, is still online. The website hosts an interview transcript with Dispossessor that seems to be AI-generated.
Fighting Forums
A threat actor posted information on 78,540 members of the forum Leakbase to BreachForums. This information includes their username and some basic metadata.
Threat actor posted LeakBase users’ information to BreachForums
This is a common occurrence, as forums constantly hack each others’ member databases then post them. There doesn’t seem to be any public fight currently between Leakbase and BreachForums.
In our first story about the National Public Data breach, a subsection of the data was posted for sale by the threat actor USDoD on Leakbase.
Double “J.P. Morgan” Arrest
The National Crime Agency in the U.K. arrested two threat actors who both go by the name “J.P. Morgan.” The law enforcement agency identified them as culprits behind the Reveton Ransomware Group.
They not only operated the Reveton Ransomware Group, but also Ransomware Cartel, and the Angler Exploit Kit.
Collectively, these threat actors have extorted millions of dollars from a wide variety of victims.
Law enforcement arrested four other members of their group, specifically those who are suspected of being involved in the Angler Exploit Kit, and 15 of their employees. Their office that they operate in Ukraine was raided as well.
Cisco’s 2015 mid-year report states that Angler accounted for 40% of user penetration in cyber attacks observed so far (at the time). A lot of early ransomware used Angler such as CryptoWall, Teslacrypt, Torrentlocker, and old banking trojans like Tinba.
This is a major arrest in the realm of malware history. This is a developing story in that law enforcement has not publicly identified the identity of one of the J.P. Morgans.
Leaky Weekly and Flare Academy
Leaky Weekly is brought to you by Flare, the world’s easiest to use and most comprehensive cybercrime database that integrates into your security program in 30 minutes.
Flare now offers Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick!), and more.