
This article was updated December 17th, 2025.
By Christopher Budd, Cybersecurity Evangelist
Cybersecurity practitioners have been addressing “external threats” since the beginning of our discipline.
Look at Matthew Broderick in 1983’s film “War Games” or read Cliff Stoll’s 1989 book The Cuckoo’s Egg: Tracking a Spy Through the Maze of Computer Espionage. In both of these examples from the early days of computing, you see that external threats have been around and top of mind for defenders as long as computers have.
While the category of external threats has been around for decades, the specific nature of the threats, and what you need to do to protect against them, has evolved.
In fact, the threat environment is always evolving, and security teams must constantly adapt.
It’s not just about understanding “external threats.” It’s about understanding today’s external threats so you can counter them appropriately and defend your environment effectively.
What Are External Threats
For many years, the classic external threats in cybersecurity fell into three basic categories:
- Malware, like ransomware
- Hacking, like Distributed Denial of Service (DDoS) attacks
- Social engineering, like phishing
These are still active external threats. But the days of the “malicious-hacker-in-a-black-hoodie” lobbing phishing emails at your organization as your greatest external threat are long past. Yes, these external threats haven’t gone away, and you still need to protect against them. They can still cause you harm and, in fact, play a supporting role for today’s top external threats. But protecting against the classic threats misses today’s top external threats, in this era of threat actors “logging in” rather than “hacking in.”
External Threats in 2026
Verizon’s 2025 Data Breach Investigations Report (DBIR) shows that stolen credentials and vulnerabilities are the top two external threats seen in successful attacks in 2025.
Stolen credentials (22%) and exploitation of vulnerabilities (20%) are the top two initial access vectors for non-error, non-misuse breaches (page 21). For ransomware specifically, both tactics remain central, with approximately 42% of ransomware breaches involving compromised credentials, an exploited vulnerability, or phishing (page 40).
Let’s take a step back and dig further into stolen credentials, their link to stealer logs, and how that connects to the larger picture of external threats.
Digging into Stealer Logs
Use of stolen credentials is the most common method for web application attacks. In this era of cybercrime, stolen credentials typically equal stealer logs.
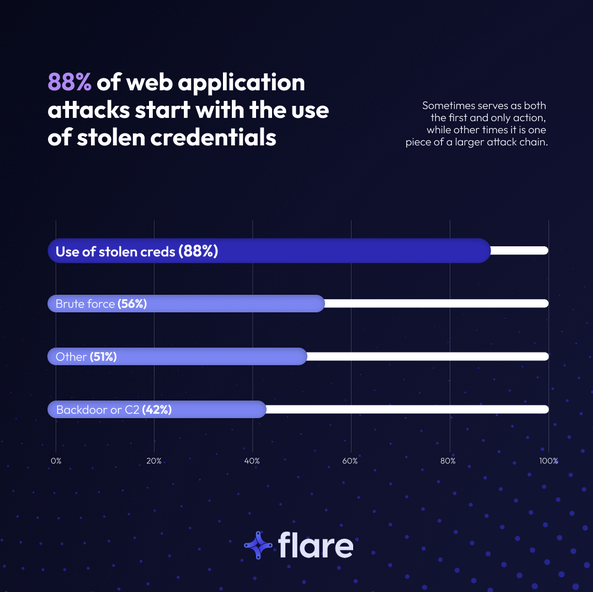
Most web application attacks start with stolen credentials (Source: Verizon DBIR)
The DBIR reveals links between stolen corporate credentials and ransomware:
- 54% of ransomware victims had their credentials found in infostealer logs
- 40% of those logs included corporate emails
- The median time between ransomware victim disclosure and the detection of related stolen credentials is 2 days, indicating that infostealers are leveraged by ransomware operators
Enter the EDR Killers
There’s one additional emerging trend from 2025 that comes into play when we talk about today’s external threats: Endpoint Detection and Response (EDR) killers.
Malware is a classic external threat: antivirus software is the classic countermeasure for it. What we used to call “antivirus” is today called EDR. EDR has more features and capabilities than antivirus did in the past, but the principle is the same: to protect the endpoint (primarily the Windows PC).
Today’s threat actors see EDR as a threat to their goals of ransomware attacks and breaching networks because EDR can counter the enabling role that malware plays in these attacks. To address that, threat actors have found their own countermeasure to the EDR countermeasure: the EDR killer.
EDR killers first started appearing in 2023, but in 2025 they achieved enough widespread use to warrant an advisory from the Singapore Cyber Security Agency (CSA) and the Cloud Security Alliance (CSA).
The Singapore CSA advisory makes clear how EDR killers work in support of ransomware attacks, but a research report from Vectra AI shows that EDR is failing against infostealers as well.
Both of these make clear that EDR alone as a countermeasure is not sufficient to fully protect against today’s external threats.
The Costs of Today’s External Threats
While it’s hard to put a price tag on the cost of today’s external threats, we can get some approximation.
According to Forrester’s Total Economic Impact Study, a sample customer organization has a 68% likelihood of experiencing one or more serious data breaches in a year, and an average potential cost of $4.4 million.
In addition, 88% of SMB breaches involve ransomware vs 39% for larger organizations, and the median ransom paid was $115,000.
Recommendations for Addressing External Threats
Staying ahead of today’s external threats that are aiming for breaches and ransomware attacks requires more than just EDR. Preventing these attacks by today’s external threats requires an additional layer of protection that can focus on these top two threats: leaked credentials and exploitation of vulnerabilities.
A Threat Exposure Management solution can automate monitoring for leaked credentials and secrets across the clear and dark web, and illicit Telegram channels. This could also help you monitor cybercrime forums for activities and chatter around newly disclosed vulnerabilities. This can enable you to identify when a malicious activity around a specific vulnerability increases, very often a precursor for active attacks, particularly by ransomware threat actors, like we saw with MoveIT in 2024.
Breaking Down Comprehensive External Threat Mitigation
Protecting your organization against external threats requires a defense-in-depth approach to security. As you mature your security posture, you should consider the following activities that mitigate external threat risks:
- Identity exposure management: With so many stolen credentials turning up in stealer logs, it’s important for organizations to be able to scan threat actor communities for stolen passwords, cookies, and session tokens.
- Dark web monitoring: Automatic scans of threat actor communities are essential to detecting exposure. These tools scan the dark web and illicit Telegram channels to identify leaked credentials and targeted threats against your organization.
- Endpoint Detection and Response (EDR): Detect abnormal endpoint activity and automate responses to mitigate risks arising from things like ransomware and malware.
- Vulnerability scanning and patch management: Monitor for known vulnerabilities across all devices connected to networks and install security updates.
- Cyber awareness training: Provide employees with training opportunities so that they can detect and report phishing attempts.
- Encryption: Encrypt data-at-rest and data-in-transit to prevent cybercriminals from using data that they steal.
External threats today are bigger, broader, more costly, and more complex. They’re focused on breaches and ransomware, relying heavily on stolen credentials and exploiting vulnerabilities.
That reality, combined with increasing attacks against EDR, means that keeping an active eye on what’s happening in the threat actors’ space is an important additional step in preventing successful attacks. As the saying goes, forewarned is forearmed. And today, another way of being forewarned is to take your security to the threat actors’ space with active, ongoing monitoring.
Mitigate External Threats Faster with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security. Check out how you can monitor for leaked credentials with Flare:
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





