
There’s so much to keep up with in the world of cybercrime…especially for security practitioners.
Leaky Weekly is a cybercrime current events podcast hosted by security researcher Nick Ascoli as he dives into the most pressing stories on data leaks, cybercrime, and the dark web in the last week or so.
On this episode of Leaky Weekly, Nick covers:
- AT&T breach
- Snowflake tenant breaches
- SiegedSec
- Disney hack
Important disclaimer: When a company is possibly the victim of a breach, that may not necessarily be the case for various reasons, such as if threat actors may not actually have the information they claim to. Security practitioners should be supportive of organizations/security teams addressing breaches and never shame them.
These are all developing stories that we covered very briefly, so check out cybersecurity news outlets to stay up-to-date. We couldn’t cover everything in the last few weeks or so, and we’ll look into new stories and developments in two weeks.
Tune in for current events on the podcast below on Spotify, on Apple Podcasts, check out the video episode on YouTube below, or keep reading this article for the highlights.
AT&T Breach
Billions of text and call records stolen
A threat actor reached out to a security researcher to share a sampling of the researcher’s call records. After the researcher confirmed that those were their call records, the threat actor reveals that they leveraged a Snowflake account that didn’t have MFA turned on, and accessed the information in that tenant.
This threat actor sent the information to a few people including a member of ShinyHunters, a threat actor group.
The original security researcher informed Mandiant, which then notified AT&T, which then filed an SEC filing and claimed that the threat actor associated with the breach has been arrested.
The original threat actor had been arrested but was actually arrested in relation to a T-Mobile breach, a few years ago.
AT&T attempted to contact ShinyHunters through the original security researcher:
- AT&T paid ShinyHunters five bitcoins to delete the data (with the security researcher also receiving a cut).
- ShinyHunters sent AT&T a video deleting the data (though it’s possible they may have other copies).
- WIRED also gets a hold of this video.
- ShinyHunters told several news outlets that the original threat actor shared the data with multiple people, including a ShinyHunters member (so it’s possible there are multiple copies of this information out there).
This is a developing story, and it’s unclear how many copies of this information may be floating around. There are many theories of how malicious actors can exploit this data as they include information such as cell tower local pings that can geolocate where a call took place.
Snowflake Tenant Breaches
Unauthorized third parties breaching major Snowflake tenants have been in the news for the past few weeks such as with Ticketmaster, Santander Bank, and more.
How these breaches have been playing out: threat actors (such as ShinyHunters) are abusing infostealer logs that contain login information to various Snowflake tenants.
How do infostealers work?
An independent contractor may have had access to a Snowflake tenant. They may have been working on a personal device, and downloaded a cracked version of design software. This design software could function, but also have brought an infostealer in the installer. This infostealer malware can steal all of the logins saved to this person’s browser, cookie sessions, browsing history, and more. This can get uploaded to a forum or illicit Telegram channel.
This is not necessarily Snowflake’s fault but rather they are issues of human error.
Mandiant and Snowflake have published a report together that can be useful to understand the scope of this problem, and best practices in moving forward.
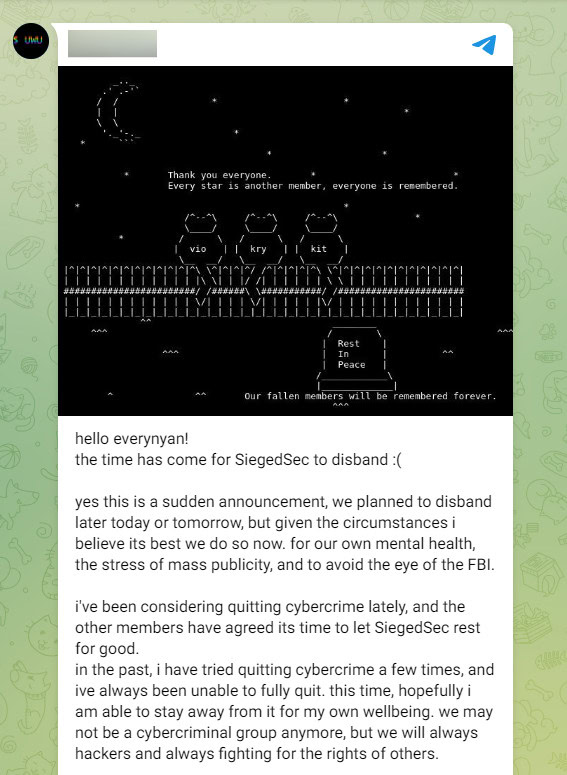
SiegedSec
SiegedSec is a hacktivist group that targeted the Heritage Foundation, a conservative American think tank, and shared stolen information in their Telegram channel. However, they disbanded shortly after, stating that there’s a lot of attention on them and they should lay low for some time.
In the last few years, SiegedSec selects a cause to rally behind and hits target companies relevant to that campaign. These target organizations include companies that have donated to a certain political cause, or stand in firm political opposition to the hacktivist group’s values.
SiegedSec’s leader posted in their Telegram channel (screenshot below) that they disbanded due to, “[their] own mental health, the stress of mass publicity, and to avoid the eye of the FBI.”
This is a major shakeup in the hacktivist realm.
Disney Hack
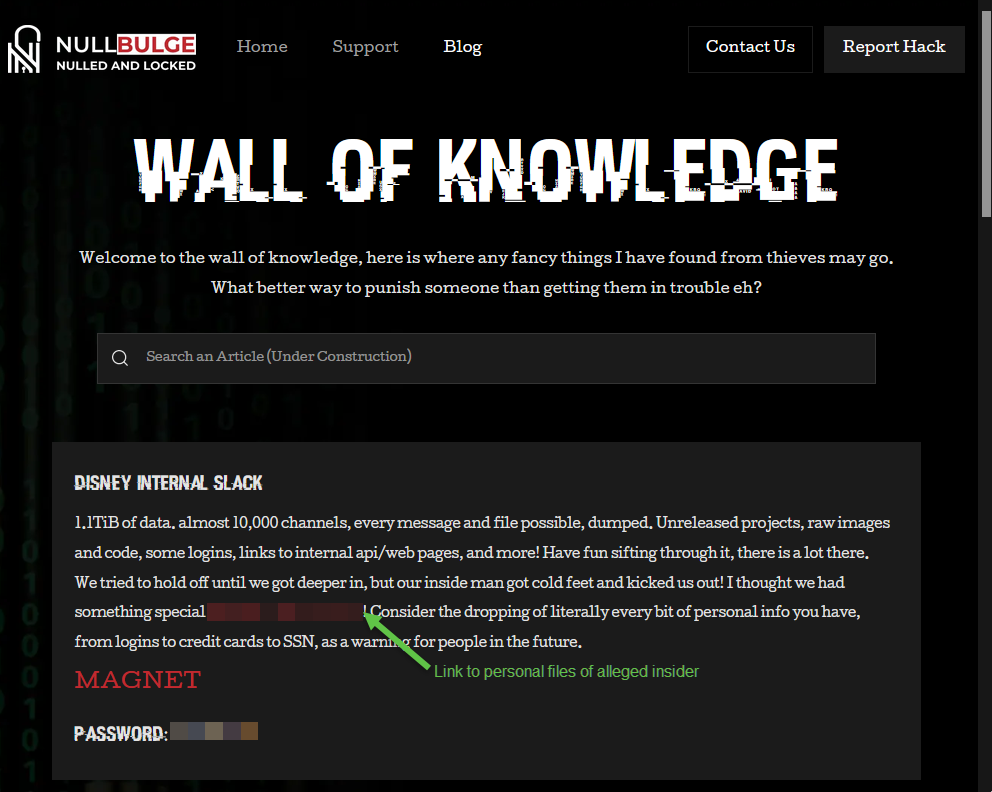
The hacktivist group NullBulge, which claims to protect artists’ rights, hacked into Disney’s internal Slack messages in a protest over AI-generated art.
NullBulge claimed there were two prominent methods of hacking:
- An insider supposedly gave the group access to Disney’s internal Slack. However, this insider cut off NullBulge’s access, and the group responded by doxxing this individual.
- The WIRED article mentions infostealers may have been involved.
The leak revealed 1.1 terabytes of messages, unreleased projects, code, documentation, and more across 10,000 Slack channels. NullBulge posted this information on their blog.
Leaky Weekly and Flare Academy
Leaky Weekly is brought to you by Flare, the world’s easiest to use and most comprehensive cybercrime database that integrates into your security program in 30 minutes.
Flare now offers Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick!), and more.





