This article was updated on August 4th, 2025.
One-time password (OTP) systems, often used in two-factor authentication (2FA), are considered a strong security measure, but they are not foolproof.
Cybercriminals are using OTP bots to bypass these protections. We’ve put together this guide about OTP bots, their impact, and mitigation methods.
Understanding OTP Bots: Their Function and Operation
What are OTPs?
One-time passwords create a unique and temporary code. Along with their regular password, a user will need to input the code to gain access to an account.
The code is delivered via different mediums, such as text messages, emails, or authentication apps. The idea behind OTP is to add an extra layer of security. Even if a threat actor obtains a user’s password, they still need the OTP to access the account.
OTPs are regarded as one of the safest methods of protecting digital identities. However, malicious actors adapt to new technologies. They have created OTP bots to circumvent this additional security layer.
What is an OTP Bot?
OTP bots can steal the temporary codes to gain access to an account. OTP bots vary based on their design and the vulnerabilities they are built to exploit.
For instance, some OTP bots target vulnerabilities in the software used to generate or transmit the OTPs. Others focus on user behavior and leverage social engineering techniques to trick users into providing their OTPs.
The programmed bots are crafty and scalable, and they exploit various tactics. Some common tactics include:
- Social engineering: Bots may impersonate a trusted source (like your boss or bank) to ask for OTPs.
- Automated calls: Robocalls can also use social engineering to convince a victim to share their OTPs.
- MFA fatigue: Bots may send repeated push notifications until a victim confirms the request.
- Brute force and phishing: Brute force attacks can find weak passwords, but OTPs can still block access. OTP bots may set up a phishing campaign to get the user to share their OTP.
How Do OTP Bots Work?
Understanding what OTP bots do and how they work is the first step in grasping the scale of the threat they pose.
Here is how threat actors use OTP bots:
- Threat actors purchase stolen login credentials on the dark web or use hacking methods to discover passwords.
- If an account has 2FA enabled, threat actors may purchase OTP bots to steal the temporary code. Depending on the account targeted, it could be a text asking for a code, a robocall, or repeated push notifications on the user’s phone.
- The threat actor contacts the user and uses the OTP bot to trick the user into sharing their 2FA code.
- A user with no awareness of OTP bots may fall victim to the scam and grant access to hackers.
The Impact of OTP Bots on the Cybersecurity Landscape
Why are OTP Bots Rising in Popularity?
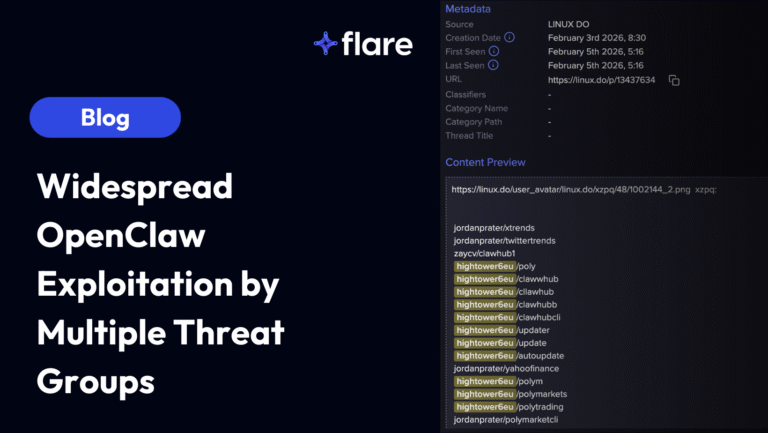
Flare conducted a search on Telegram in 2022 for the terms “OTP bot” and “2FA bot”. There were 1,700 results. In 2025, the same terms have almost 3,000 times the results. OTP bots have seen a huge rise in demand.
The growing popularity of OTP bots stems from their widespread availability in cybercrime communities. Many bad actors offer OTP bots as a service and sell them to other cybercriminals through platforms like illicit Telegram groups – as shown in this screenshot below.
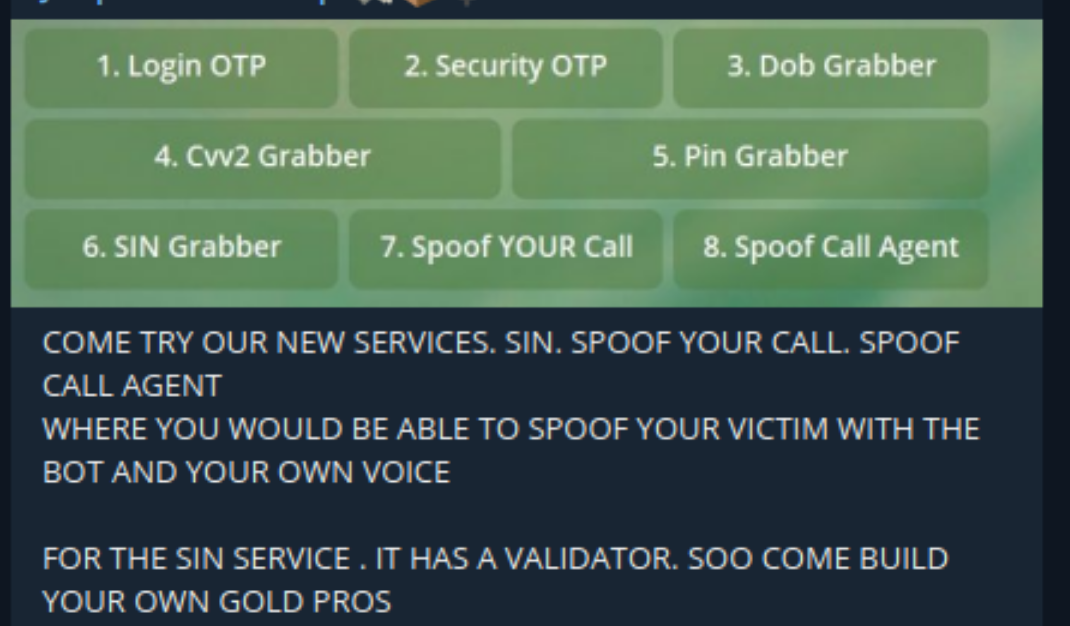
Another reason why OTP bots are in demand is that they are accessible to any technical level. Bad actors don’t need technical expertise to deploy OTP bots.
Strategies for Detecting and Mitigating OTP Bots
Use Compromised Password Detection
OTP bots only work if the threat actor has the correct password. Organizations should have a strong password policy in place. It’s also helpful to have compromised password detection.
Tools can monitor the dark web and cybercrime communities and look for relevant threats that mention your organization. It can raise an early red flag to detect if an employee’s account is at risk.
Deploy Advanced Threat Detection
Conventional antivirus software may fail to detect OTP bots. Organizations should invest in threat detection systems powered by artificial intelligence (AI) and machine learning (ML).
These systems can analyze patterns and detect anomalies. They can also provide real-time alerts to potential threats. Advanced threat detection ensures a quicker and more effective response to any security breach.
Conduct Regular Security Audits
Regular security audits can help identify vulnerabilities that OTP bots could exploit. These audits should encompass all aspects of your cybersecurity infrastructure, including:
- Software
- Hardware
- Network protocols
- User behavior
Address weaknesses promptly to prevent possible attacks.
Secure OTP Transmission Channels
Some bots intercept one-time passwords during transmission. It’s essential for organizations to secure these channels. Encrypting communication channels or moving to more secure OTP delivery methods, such as hardware tokens or dedicated authenticator apps, can help.
Train Employees on Threats
A significant proportion of OTP bot attacks succeed because of human error. OTP bots work because of social engineering tactics and a lack of knowledge about potential threats.
Organizations need to provide comprehensive security training for all employees. Regular training sessions can turn employees into your first line of defense against cyberattacks.
Some topics that employees should know include:
- Threats posed by OTP bots
- Phishing attempts
- Dangers of downloading unverified apps
- Importance of regularly updating and patching their software
Monitoring the Dark Web with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.