Negotiators manage complex communication and pressure to minimize damage to organizations. Different ransomware groups can have different communication styles, and being aware of these can help organizations be prepared.
Security teams can equip themselves for ransomware scenarios using threat intelligence on several cybercriminal groups we’ll cover here.
Why Do Organizations Engage in Ransomware Negotiations?
Organizations participate in ransomware negotiations for two reasons:
- To buy time for recovery or
- To reduce the ransom demands.
Cybercriminals use various tactics to put pressure on paying the ransom. Understanding ransomware groups and their tactics prepares negotiations for their communication styles.
Ransomware Negotiation Chat Simulators
Ransomware incidents are high-stakes communications, and fortunately there are tools for security teams to better train to be in these negotiations.
Ransomware negotiation chat simulators, like Ransom Chat, use real messages to analyze behavior patterns and mimic cybercriminal groups. The simulation helps negotiators train for realistic communication scenarios and understand attacker tactics.
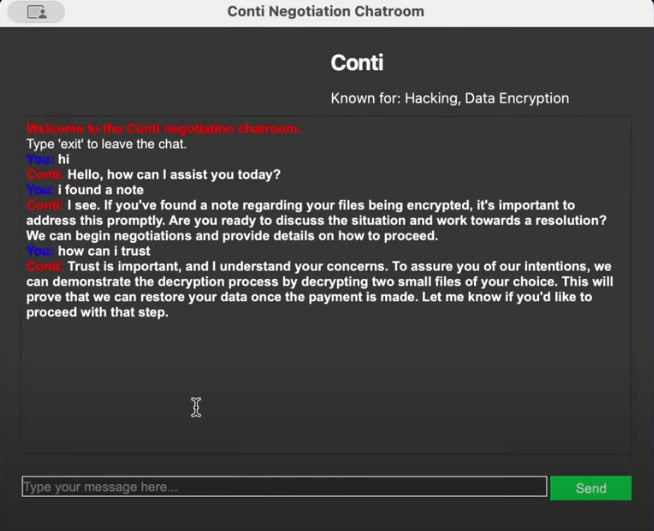
Example of a ransomware negotiation through Ransom Chat with the ransomware group Conti
Ransomchat Project
Another valuable resource is the Ransomchat Project, which collects real-life negotiations with ransomware groups. You can view the conversations and gain insights into ransomware negotiation patterns, tactics, and communication strategies from different cybercriminal groups.
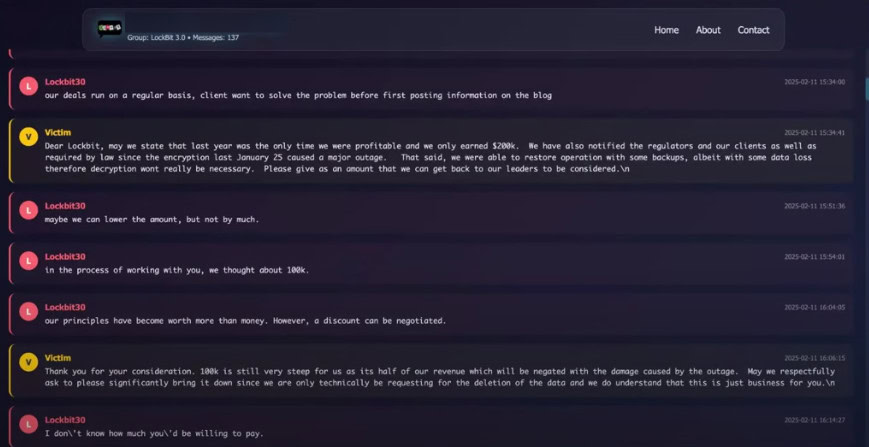
Messages from LockBit with a victim during ransomware negotiations
Understanding Different Negotiation Styles: Conti vs LockBit
By analyzing past ransomware negotiations, security teams can build an effective ransomware response plan.
Flare Research analyzed conversations from cybercriminal groups Conti and LockBit to uncover their negotiation styles. Using stylometric, tone, and pattern analysis, we determined how each group communicates with their victims.
Here’s what we learned and examples from their ransomware negotiations:
Conti
Negotiations with Conti are handled by its core team. Each ransomware victim interacts with the same people. Their negotiation style is formal and businesslike.
Tone
Conti maintains a professional tone in their conversational style. They invited collaboration to work out a deal. Conti frames the extortion as a business transaction with formal deliverables.
Conversation example: “We always keep the terms of our contract.”
Pricing
Conti seems more flexible in terms of payments. They tend to set a high ransom demand but can negotiate down. Conti shows controlled concession and uses discounts to portray reasonableness. Their priority is to get paid, so they are more willing to lower their demand.
Conversation example: “$500,000…We are ready to accept $256k.”
Deadlines
Conti uses business-like countdowns for companies to respond to their ransom demand. They use soft clock management like a law firm on retainer. Victims are told they have until the end of the week or X number of business days to pay the ransom.
Conversation example: “2 business days left before we start uploading your private data.”
Intelligence
Conti claims to have access to financial, insurance, and client databases. They use intelligence as a pressure tool and a reason to dismiss counteroffers.
Conversation example: “We studied your financial documents and bank statements.”
Deliverables
Conti treats the ransom exchange as a productized service. They discuss what you will receive in exchange for paying the ransom. Conti also has a post-penetration mentality and shares how they got into your system and what they did.
Conversation example: “You will be provided with…full file tree…deletion log…security report.”
Escalations
Conti leverages legal and reputational doom to escalate negotiations. They mention publishing data with the fallout leading to bankruptcy.
Conversation example: “The publication…will bring your company to bankruptcy.”
LockBit
Unlike Conti, the core team isn’t always the negotiators. LockBit uses affiliates, and ransomware victims may negotiate with them instead. The overall negotiation style is a bit chaotic and emotionally charged.
Tone
LockBit is more inclined to lash out and disparage the victims. Affiliates tend to act this way if they weren’t as popular or desperate for money. LockBit uses intimidation tactics and ego games to provoke fear and submission.
Conversation example: “You think I’m a fool? I have your files and I know how much money you have.”
Pricing
LockBit ties its ransom demand to the victim’s revenue. They look at the company’s financial statements and other information to maximize the amount of money they can demand. LockBit negotiations tend to start with extremely high ransom demands and ridicule alternative offers from the company.
Conversation example: “Don’t offer me 1-2-3m$, it’s ridiculous for your company size.”
Deadlines
LockBit uses a timer to create psychological pressure of impending doom. The timer pushes victims into panic and makes them want to take action.
Conversation example: “You see the timer. Nobody going to wait for you.”
Intelligence
Like Conti, LockBit also claims to know the victim’s internal company finances. LockBit implies omniscience and uses intelligence to bolster threats.
Conversation example: “I know who you are and what work you need to do.”
Deliverables
LockBit is interested in the blackmail aspect of ransomware negotiations. They tend to make people afraid, so they’ll pay the ransom demand. LockBit uses evidence as blackmail. The “proofs” they send are bait.
Conversation example: “You can choose up to 5 random files from file tree and we’ll send it like a proof.”
Escalations
LockBit uses shock-value tactics to escalate negotiations. They mention working with the press, law, and unions to bring down the company if they don’t pay the ransom demand.
Conversation example: “We will start working with media…tax departments…and unions.”
Conti vs. LockBit: Negotiation style comparisons
Conti and LockBit demonstrate two polar opposites of negotiation styles. Conti was professional and focused on delivering a package. Meanwhile, LockBit was intimidating and aggressive about receiving a ransom payment.
Despite differing styles, each group had similar outcomes of receiving a ransom payment. For organizations to counter ransomware negotiations, they need to have a strong understanding of the negotiating group to get the desired results.
| Tactic | Conti | LockBit |
| Tone | Calm, businesslike | Emotional, bullying |
| Pricing | Structured, negotiable | Anchored high, ridicules counters |
| Timers | Framed as professionalism | Framed as threat |
| Intelligence | Used as leverage | Used for coercion |
| Deliverables | Packaged service | Intimidation props |
| Escalation | Reputational and legal ruin | Media spectacle, direct pressure |
Preparing for Ransomware Attacks
Building in training for ransomware attacks into your team’s security operations can help minimize the potential impact if an attack occurs. By better understanding these ransomware negotiations, security teams can address them more effectively to protect their organizations.
To learn more about ransomware, join the Flare Academy Discord Community to access training materials from Introduction to the Ransomware Ecosystem, which features the information covered in this article.
Ransomware Readiness and Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.