
Stolen credentials fuel a big portion of the cybercrime ecosystem. So how are threat actors stealing them? Infostealer malware has exploded in growth in the last few years, and they can steal information saved on computer browsers such as:
- Discord tokens
- Passwords
- Cookies and sessions
- Screenshots
- IP address
- Geolocation
- Phone number
- Address
- And more!
Stealer logs are the results of infostealer malware taking data from computers. Threat actors buy and sell stealer logs, which then contain stolen credentials, amongst other information.
In his video Tracking Cybercrime on Telegram, ethical hacker and cybersecurity researcher John Hammond explores the relationship between infostealer malware and Telegram. Check out the video, and/or we’ve put together takeaways for you from the video below.
1. Telegram is a Hub for Cybercrime
Telegram’s messaging and channel features have made it a favored platform for cybercriminals. The platform’s structure allows for rapid dissemination of information while maintaining a degree of anonymity. It remains a dominant messaging platform for cybercrime despite the arrest of the app’s founder and the platform’s announcement of increased cooperation with law enforcement last year.
John shows how threat actors can use Telegram to distribute malware, share stolen data, and coordinate attacks.
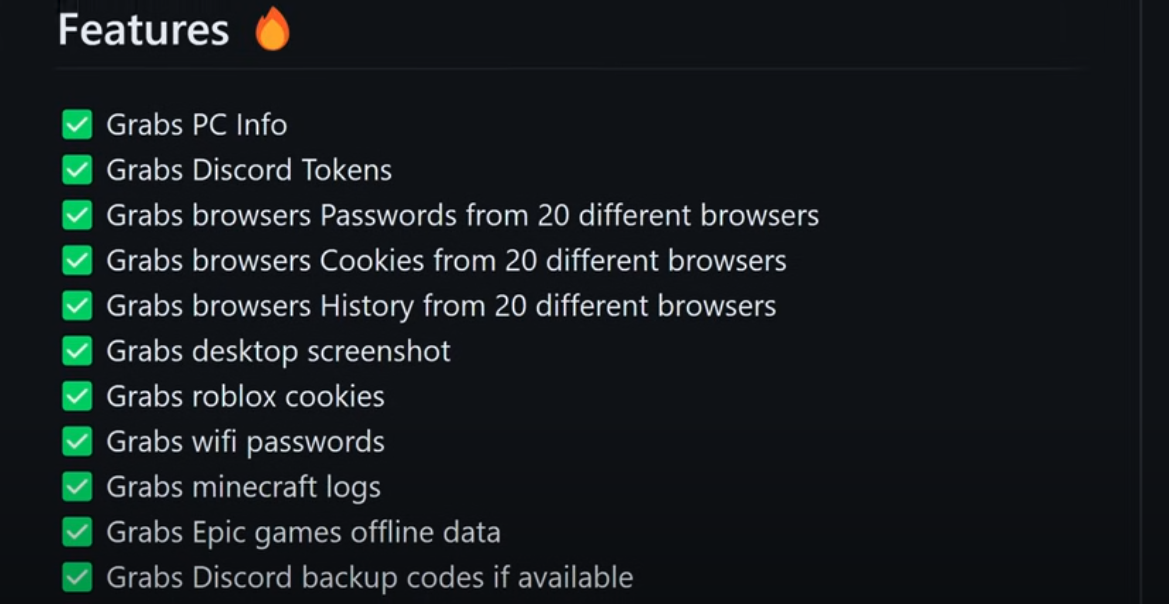
This is part of an advertisement for infostealer malware on Telegram, and explains what information it can steal from a computer browser
2. Security Teams Can Monitor Telegram with a Threat Intelligence Solution
Security teams can monitor Telegram, amongst other sources, as a source for leaked credentials with a cyber threat intelligence platform. By inputting specific search terms, users can uncover discussions and data leaks related to their organization. This proactive approach aids in identifying potential threats before they escalate.
John pokes around Telegram with Flare and searches terms like “discord stealer” to see threat actor chatter about infostealer malware that targets Discord accounts.
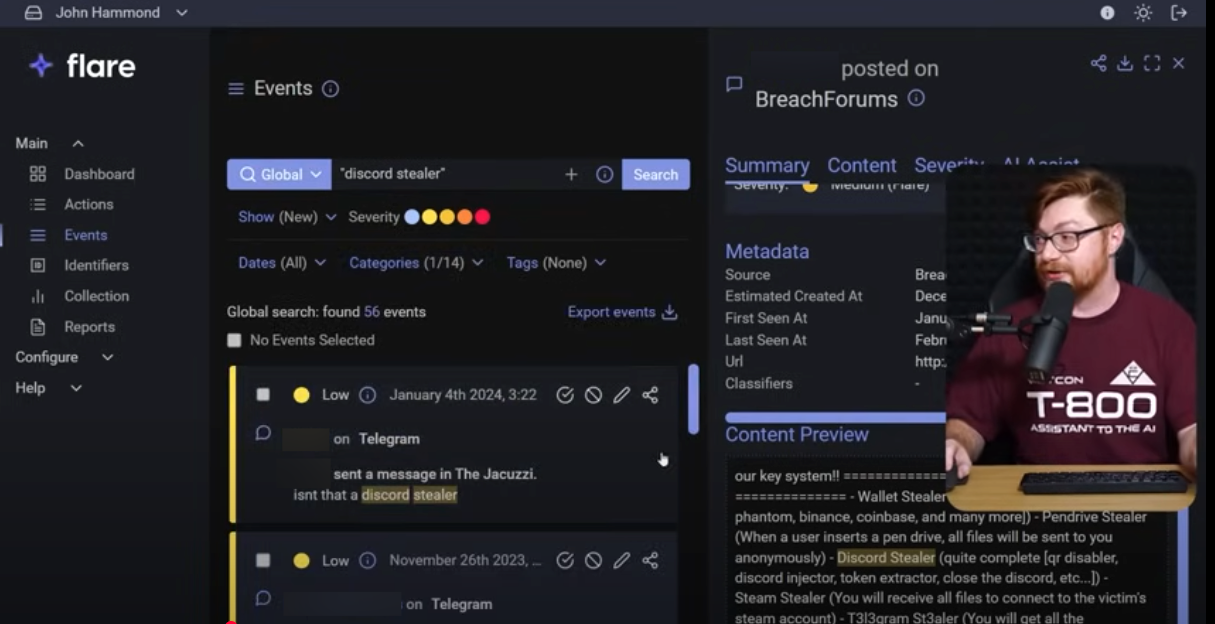
John looks up “discord stealer” on Telegram with Flare
3. Security Teams Can Uncover Telegram Bots
Threat actors employ Telegram bots to automate the distribution of stolen information. Depending on the strain, infostealer malware can upload and push all the information it takes to Discord or Telegram. Threat actors then have a central location to retrieve and see this stolen information.
John demonstrates looking into Telegram bots with open-source software and tracing the underlying infrastructure of these operations. This provides insights into the scale and coordination of cybercriminal networks.
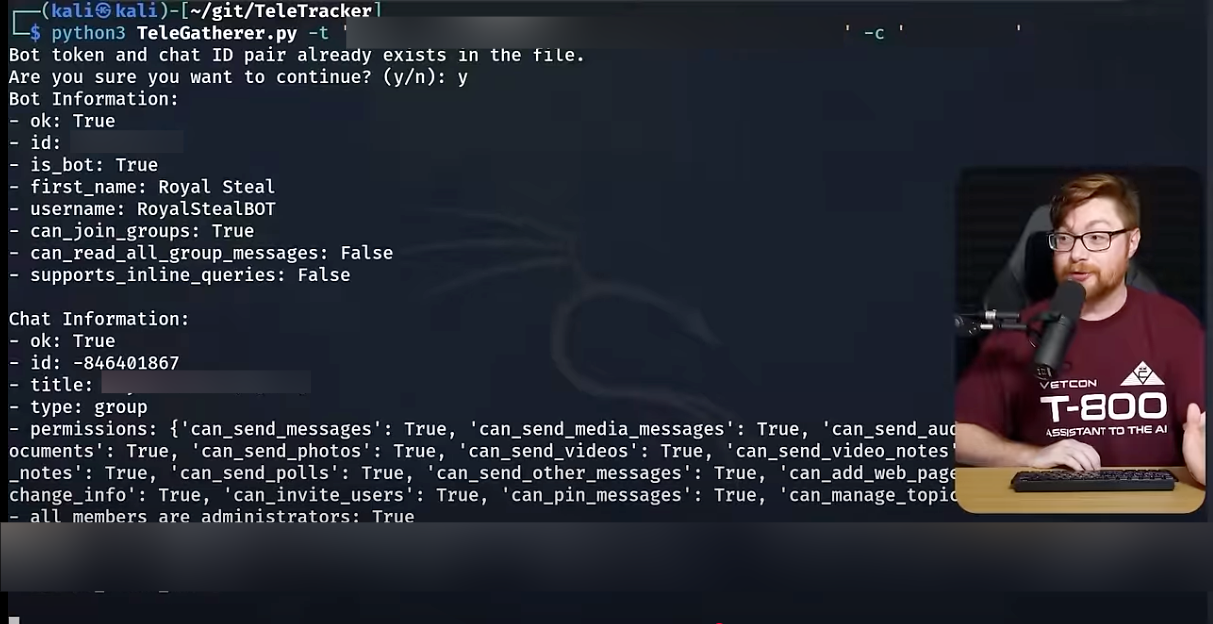
John pulls up the name of the chatbot, the title of the chat it shares leaked credentials to, and other data
4. Automation is Accelerating Cybercrime
John emphasizes the increasing use of automation in cybercriminal activities. From deploying bots to managing stolen data, automation enhances the efficiency and reach of these operations. Understanding these automated processes is crucial for developing effective countermeasures.
Also, automation can accelerate security teams to get ahead of these external threats.
Monitor Telegram with Flare
The Flare threat intelligence solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Check out what may be on Telegram about your organization with a free trial.





