Building an effective threat intelligence program that disseminates actionable data that results in real-world risk reduction has never been more critical. Threats to enterprise organizations ranging from geopolitical risk to sophisticated ransomware groups continue to proliferate while many security teams struggle to integrate dozens of tools together and stay on top of emerging threats. This article covers each stage of the Cyber Threat Intelligence Lifecycle and provides actionable recommendations for security teams.
What is the Threat Intelligence Lifecycle?
The threat intelligence lifecycle is the threat intelligence framework that CTI teams will use when asked to conduct a specific investigation or prepare reports on certain threats. The types of threats that organizations are concerned about vary dramatically. A large financial institution may ask a threat intelligence team to prepare reports on nation state advanced persistent threats that are known to target financial institutions. Conversely a mid-enterprise healthcare threat intelligence team may be asked to analyze ransomware group tactics, techniques, and procedures targeting healthcare organizations.
Working through each stage of the threat intelligence life cycle provides organizations with a coherent structure that can help ensure that threat intelligence results are actionable, in-line with risk management objectives, and disseminated to the correct organization stakeholders.
Executive Summary:
- The Threat Intelligence Lifecycle consists of six phases: requirements identification, collection, processing, analysis, dissemination, and feedback
- CTI teams can apply the threat intelligence lifecycle to analyze a range of threats including geopolitical risk, vulnerabilities, cybercrime groups, advanced persistent threats, and fraud threats among others
- The threat intelligence lifecycle helps ensure that CTI team output and analysis is correctly aligned with risk management and business objectives
- Ensuring that threat data is effectively disseminated is critical to providing value for risk management teams and executives
Understanding the Threat Intelligence Lifecycle
Threat intelligence doesn’t operate in a vacuum, CTI teams are typically assigned to specific tasks and investigations based on business requirements. Threat intelligence teams then progress through a lifecycle of activities that enables them to clarify requirements, collect and process data, analyze structured information, and disseminate actionable intelligence to relevant business units.
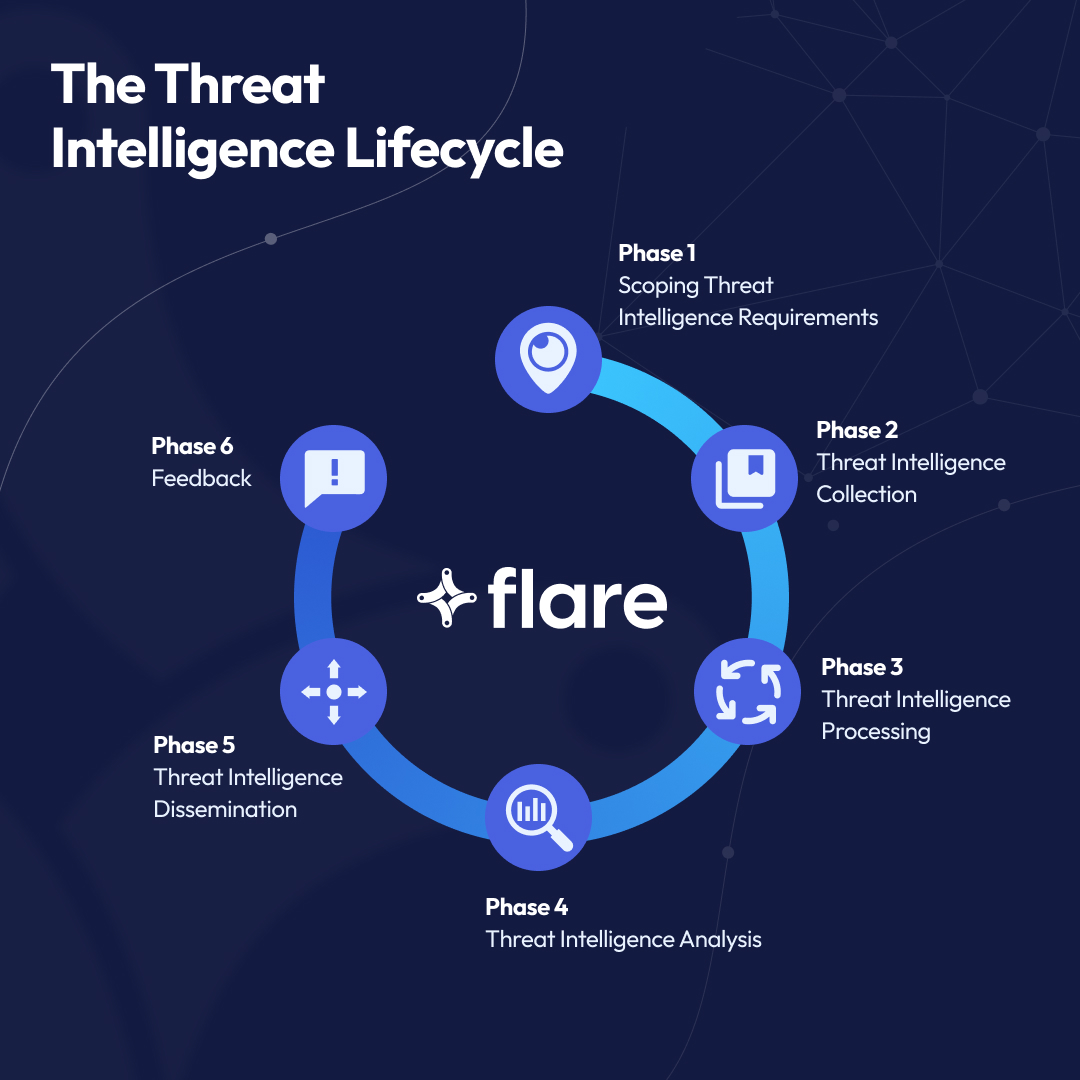
Phase 1 of the CTI Lifecycle: Scoping Threat Intelligence Requirements
Besides routine day to day threat intelligence work, such as monitoring dark web markets and forums for company mentions, most threat intelligence projects start with requirements identification. During this phase the CTI team or those responsible for intelligence collection will interface directly with other business units or executives to determine what type of intelligence needs to be collected and what the goal of the project is. Requirements identification is critical for ensuring that CTI processes correctly align with business and risk management objectives, and provide intelligence that can be actioned by relevant stakeholders.
For the purpose of this example of a threat intelligence lifecycle, we are going to assume that the CTI team has been tasked with collecting information about initial access brokers on dark web markets. Specifically we will assume that the CTI team has been asked to:
- Identify initial access brokers (cybercriminals who hack into corporate IT environments and then sell their access to other criminals on specialized dark web forums) targeting healthcare companies
- Create a list of personas that the initial access brokers use, along with relevant data about the size of organizations that they attack
- Gather relevant information around any identifiable tactics, techniques, and procedures (TTPs) that the threat actors use to gain access or escalate privileges
- Provide recommendations to the organization about how they can reduce the risk associated with being compromised by an initial access broker
Phase 2 of the CTI Lifecycle: Threat Intelligence Collection
During this phase sources of threat intelligence are identified and collection of raw data begins. If the organization is using a dedicated threat intelligence platform, data may be collected directly from the platform, if not data may be collected from relevant sources.
In this case the team would likely examine specialized dark web forums that are used by initial access brokers to auction off access to corporate IT environments. If they were using a threat intelligence platform, this data might come in a structured format, if not it’s likely they would manually scrape data off of specific web pages on TOR.
Phase 3 of the CTI Lifecycle: Threat Intelligence Processing
Once relevant data has been collected during the threat intelligence collection phase, the team would set about processing it. This involves filtering out irrelevant data that was collected incidentally, structuring data to make the analysis phase easier, and grouping similar data together that can be used during the analysis phase. This step could involve:
- Creating spreadsheets and linking disparate data elements together to create context for events and assets
- Uploading vendor supplied IOCs to a SIEM or SOAR tool to compare against real traffic
- In our example, the CTI team would likely create a matrix to show relationships between initial access brokers, identifiable TTP data discovered during collection, along with the specific forums and marketplaces they operate on
Phase 4 of the CTI Lifecycle: Threat Intelligence Analysis
The analysis phase is pivotal for providing the business with actionable, relevant data that can be used to reduce risk or inform corporate information security decisions. During the analysis phase threat intelligence analysts will work to create meaningful context and actionable intelligence out of the data that has been formatted and structured during the processing phase. CTI analyst teams should work to ensure that:
- Analysis effectively and clearly communicates to the right audience. Analysis focused on commonly exploited vulnerabilities that is destined for the vulnerability management team can be highly technical, but reports destined for the board and other executives should be focused around actionable recommendations and risk
- Analysis should be only as verbose as necessary to clearly explain the results and provide recommendations
- In our example, the CTI team would likely provide context around IABs discovered on the dark web, identify those that pose the greatest threat to the organization, and provide additional information about identifiable TTPs and countermeasures
Phase 5 of the CTI Lifecycle : Threat Intelligence Dissemination
During dissemination, relevant threat intelligence is sent out to various business units that could derive value from it and that were identified during the “identify requirements” phase. Despite seemingly being one of the most simple phases, many organizations fail to effectively ensure that actionable threat data arrives to the right stakeholders at an organization. Here are a few best practices you can use to improve threat intelligence dissemination:
- Consider creating different versions of “finished” threat intelligence at varying levels of technicality to provide value to stakeholders in technical teams, risk management teams, and at the executive level
- As your team progresses through the threat intelligence lifecycle, take the time to identify additional business units that may benefit from finished intelligence
Phase 6 of the CTI Lifecycle: Feedback
Once intelligence has been sent to relevant business units and individuals, it is time to collect feedback from the organization to determine whether the intelligence analysis was timely, relevant, and actionable. Below are some good leading questions you can ask to receive feedback that can be used to improve future intelligence gathering & analysis.
- Did the finished intelligence product result in actions that reduced risk for one or more business units?
- Was the finished intelligence at the right level of technical detail for various teams to be able to easily understand and action it?
- Were there any business units that could have benefited from the work that didn’t receive it?
Accelerate the Threat Intelligence Lifecycle with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.