
In 2021, CISOs will likely deal with a weakened cybersecurity infrastructure and unforeseen incidents driven by remote working conditions. The Covid-19 pandemic has painted a grim picture of what we may expect in the near future, making it harder for CISOs to stick with their original long-term strategies. One thing is certain: the past year has forced companies and organizations around the world to digitally transform and bring the office into our homes permanently.
As a result, CISOs may have to rethink their roles as they are adjusting to the new normal. Based on last year’s cybersecurity events and trends, here are some of the main cybersecurity concerns for CISOs in 2021:
1. Ransomware and extortion
In 2020, Flare Systems’ threat intelligence team confirmed a heightened security threat level: malicious actors switched tactics and introduced double extortion. This means criminals no longer encrypt stolen data, but also threaten to publish it on leak sites if victims don’t give in to their demands.
Additionally, Cloudflare detected an increase in ransom-driven DDoS attacks (RDDoS), actively used by Russian cyber espionage and hacking groups. Given these trends, CISOs will have to invest resources in several contingency and incident response plans to ensure their organizations are ready to fend off or mitigate this type of attacks.
2. Data breach fatigue
The high number of regular data breaches and cyberattacks has introduced a new type of threat: data breach fatigue. Every day we see in the news announcements about organizations falling victim to attacks. This no longer generates an immediate sense of urgency among consumers and companies, who might feel a breach is imminent and unpreventable. Obviously, this is not the best approach. In the long run, breach fatigue may expose your organization to attacks generated by insider threats and other weak links in the security strategy.
CISOs will have to overcome data breach fatigue and test out multiple incident response plans to ensure their teams and organizations can recover fast from network security issues. A coordinated security strategy which also encourages employees to take precautionary measures may, in the long run, prevent digital fraud, identity theft, and secure customer trust.
3. Supply chain attacks
By now, everyone is familiar with the SolarWinds breach which compromised a number of medical organizations, financial and government institutions, government contractors, high profile tech companies, and think tanks. It is alarming that by compromising one business partner, malicious actors can gain unauthorized access to their entire pool of partners and customers. In this case, it affected 18,000 organizations.
Moving forward, CISOs will not only have to upgrade their organization’s security, but make sure their business partners do the same. These can include implementing a strong identity and access management (IAM) policy by adding multi-factor authentication, patching all known vulnerabilities, constant penetration testing to identify source code vulnerabilities, and constantly looking into third-party/supply chain security management.
4. Nation-state and cyber espionage attacks
The list of companies affected by the SolarWinds hack is growing. Not only was this a major supply chain attack, but news reports and investigations have linked it to Russian intelligence. It appears malicious actors took advantage of this breach to gain unauthorized access to nuclear facilities in the U.S. This is not the first cyber espionage operation targeting key national assets.
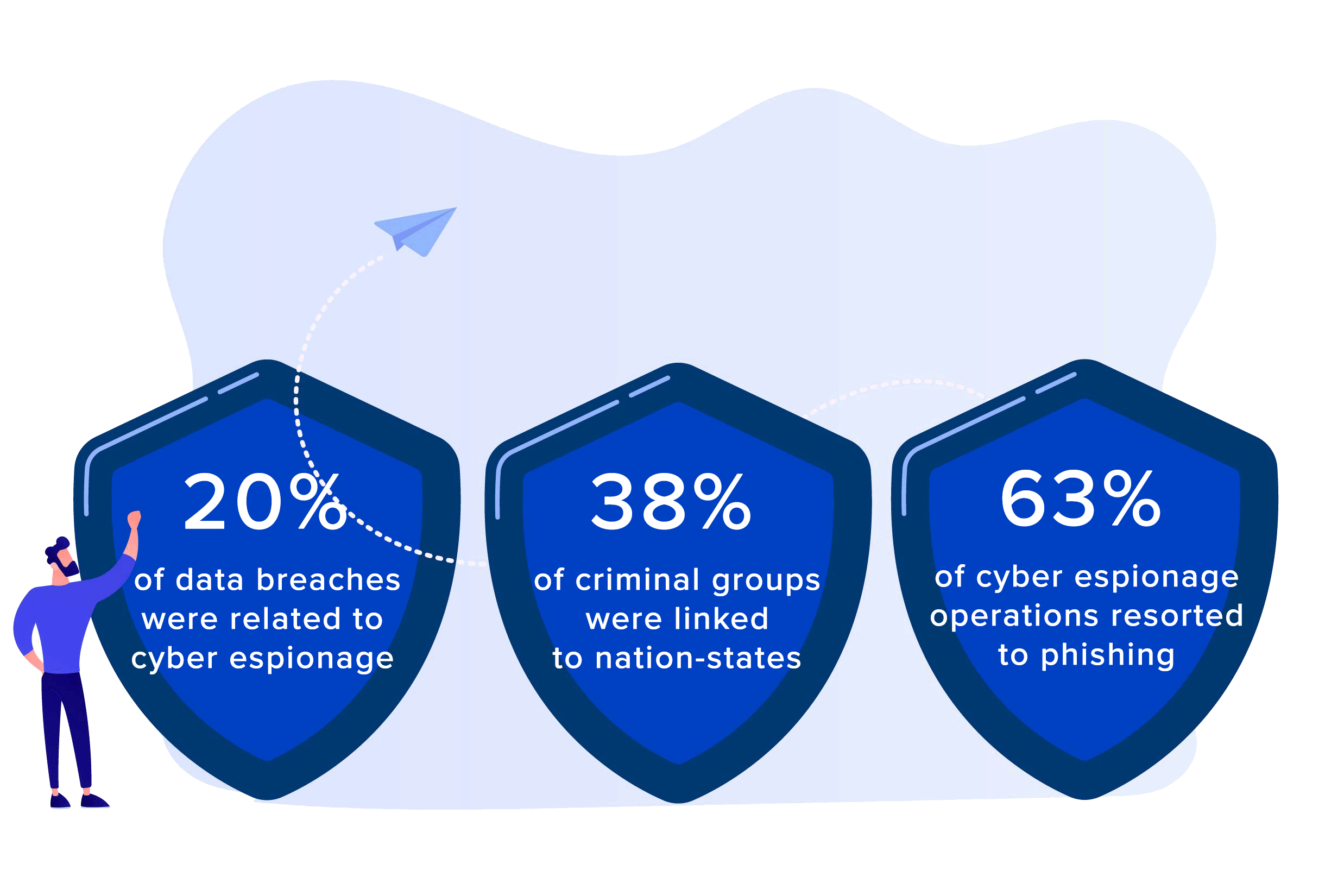
According to ENISA (The European Union Agency for Cybersecurity), “cyber espionage adversaries have slowly shifted their attack patterns to exploiting third- and fourth-party supply chain partners.” Between January 2019 and April 2020, the agency found that 20% of data breaches were related to cyber espionage, 38% of criminal groups were linked to nation-states, and 63% of cyber espionage operations resorted to phishing.
Given the COVID-19 pandemic and multiple countries’ struggle to purchase vaccines, CISOs working in local government, healthcare, technology, and pharmaceuticals may experience more pressure in their roles.
5. Security budgets
When it comes to increasing security budgets, it is never an easy conversation to have with the Board of Directors and upper management. In its latest report, research agency Gartner estimates that IT spending will increase by 6.2% in 2021, a major improvement from last year’s 3.2% decrease. As a result, the COVID-19 pandemic will generate a global spending of some USD$3.9 trillion.
Now that employees have fully transitioned from an office environment to a long-term work from home environment, CISOs may have to take on a more substantial role. A remote work network increases the threat landscape, so CISOs may feel under a lot more pressure. Not only will they have to react quicker and implement remote endpoint protection, but they will have to adjust to new data protection and data privacy regulations.
This year’s security budgets should also include hiring security talent to help overcome obstacles faster, however the higher the demand, the less likely it will be to find suitable candidates. Unfortunately, the latest reports show that the global cybersecurity skills shortage is worsening.
It will be up to CISOs this year to take on a more holistic role, outside of the traditional cyber defense approach. Even though, in the worst case scenario, cybersecurity budgets stay the same in some organizations, CISOs will still have to tackle daily issues such as integrations, network monitoring, and data control, among others. CISOs may have to partner up with other departments to ensure cybersecurity becomes a critical component of their enterprise strategy and that all expectations are aligned.





