“Even in the initial proof of concept for our pharmaceutical customer, we increased visibility of scale with several escalated alerts and gained knowledge of systems that showed significant risk.”
-MSSP
Challenge: Multinational Pharmaceutical Company Needs Holistic View of their Exposure
A multinational pharmaceutical company had an information security program that lacked a comprehensive view of their exposure on the clear & dark web. Their goal was to get a better understanding of how an exposure monitoring solution can provide value and security to enforce the organization’s control objectives, as well as how clear & dark web monitoring can provide ongoing visibility into the organizations’ data security objectives. They reached out to our customer who partnered with Flare for the engagement.
To help manage their goal and better understand the unique needs of the organization, the MSSP’s team utilized Flare to conduct an exposure monitoring proof of value. This proof of value included a feature demonstration and a high level assessment of the organization’s external exposure. When the customer uncovered results indicative of risk using the Flare platform, they used that data to improve monitoring for similar types of risk on a continuous basis.
With interesting results in hand, the MSSP put on their red-teaming hats to analyze findings as an adversary would to illustrate potential impact and recommendations to resolve or mitigate the risk.
Implementation: MSSP Offers Comprehensive Proof of Value to Client
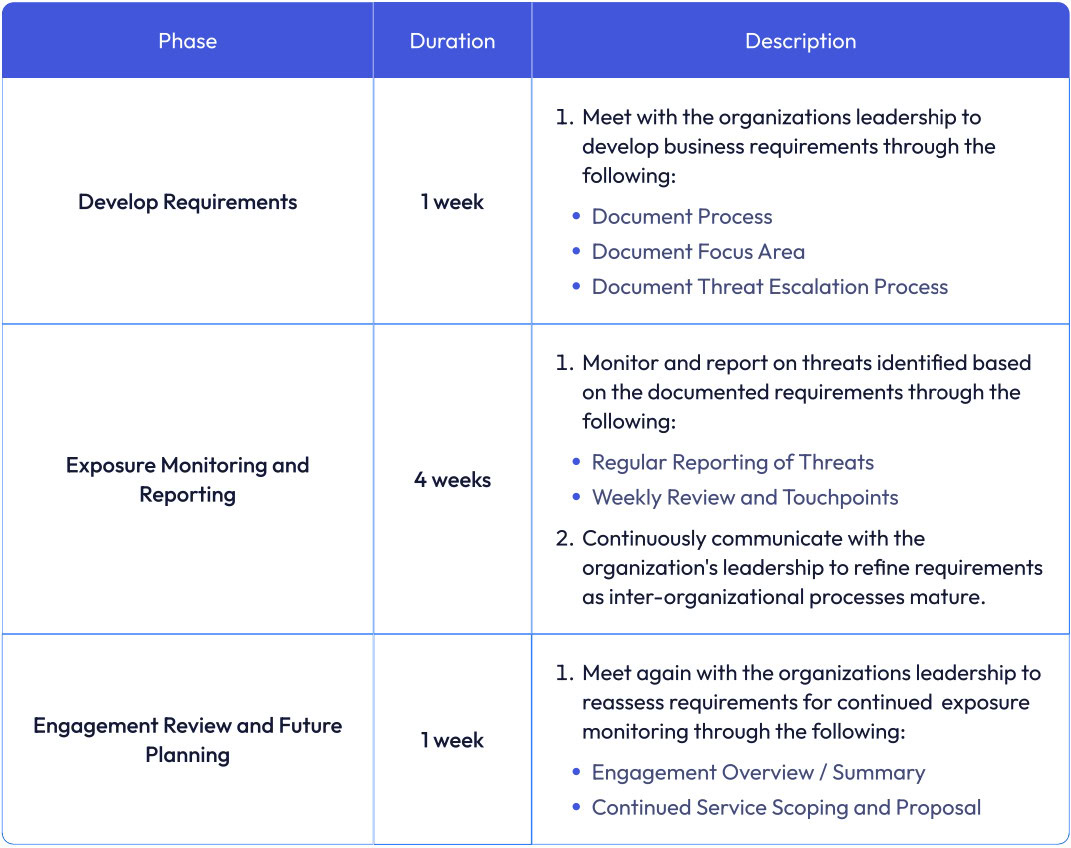
The Secure Coders team conducted the following efforts.
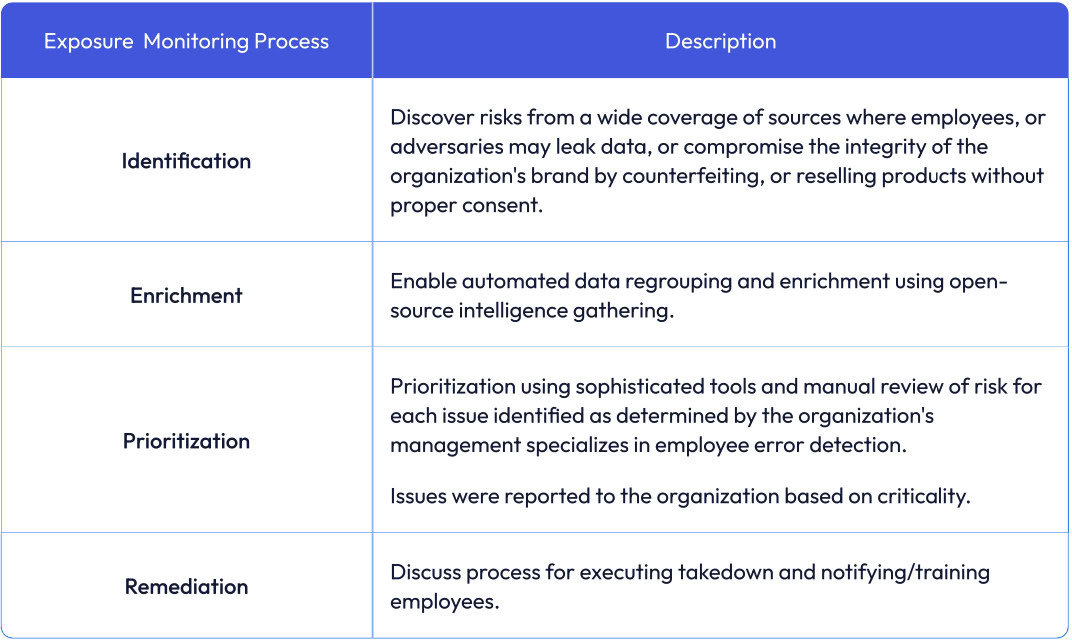
The table below outlines the process employed by Secure Coders to identify, enrich, prioritize, and remediate threats.
Using its expertise and the Flare platform, the MSSP made the following capabilities available.
- Criminal underground monitoring
- Access Brokers – Provide actionable intelligence that saves time spent to detect and remediate attacks or compromised systems for sale on dark web marketplaces.
- Forum Chatter – Classify and report on conversations occurring on dark web communication channels relating to brand, product, and operations.
- Intellectual property monitoring
- Publicly Posted Source Code – Review publicly available source code posted by both internal and external entities to the organization. Source code is analyzed and reported on by experienced software developers.
- Public Dumps – Review content posted on channels such as Pastebin that pertains to the organization’s brand.
- Public Forum Disclosures – Monitor public forums for discussions which disclose sensitive internal information.
- Monitor external attack surface
- Monitor GitHub for Source Code and Secrets leakage – Monitor online code repositories for accidentally leaked information. Run custom regexes and queries that cross public code repositories such as GitHub, BitBucket, and GitLabGit-environments.
- Detect Technical Data Leakage – Detect mistakes and secrets being committed about the organization’s environment and send alerts to the security team on accidental commits.
- Identify Misconfigured Servers – Enable real time notification of S3 storage, Shodan, and other cloud data that could put the organization at risk.
- Monitor Anonymous Sharing websites – Monitor password dumps, sensitive technical data, and PII that is posted on Pastebin and other anonymous sharing sites (bin sites).
- Preventing Account Takeover
- Real-time Credential Monitoring – Collection of leaked credentials from the dark, deep and clear web, ensuring they can’t be abused the minute they are discovered
- Automated Workforce Account Monitoring – Integrated credential dump feeds with the organization’s existing processes.
- Brand Protection
- Drug Marketplace Monitoring – Continuously monitor product and service postings on dark web marketplaces relating to product sales and counterfeiting.
- Dump Monitoring – Monitor dumps advertised pertaining to the organization’s business.
- Detecting Phishing Attacks
- Subdomain Monitoring – Identify phishing domain names and SSL certificates and detect the registration of new domain names similar to the organization’s domains.
- Preventing Financial Fraud
- Workforce Protection – Search directory of financial fraud victims, based on leaks on the dark, deep and clear web, as well as on identities for sale on illicit markets. Enable the organization to check if their workforce have been victims of fraud, while ensuring information privacy protection.
Benefit: Escalated Alerts from Exposure Monitoring Provide Valuable Knowledge on Significant Risk
Through the proof of value, we were able to demonstrate the benefits and value of implementing an exposure monitoring solution. With Flare, our customer successfully increased visibility of the organization’s external exposure on the clear & dark web. The following were delivered through the course of the proof of value:
- 1,590 Flare identifiers were created
- Monitor External Attack Surface report with 1 escalated alert
- Intellectual Property report with 9 escalated alerts
- Leaked Credential report with 1 escalated alert
- Monitor External Attack Surface report with 6 escalated alerts
- Preventing Financial Fraud report with 5 escalated alerts
Several of the escalated alerts resulted in the organization gaining knowledge of a system that presented significant risk. The MSSP’s customer requested a follow-on engagement for an advanced persistent threat (APT) style pentest targeting the system, which was performed by the MSSP, utilizing their team of experts, heavily leveraging the Flare system.


