Stay Ahead of Threats Related to Your Business Leaders
Supply Chain Ransomware Exposure Monitoring
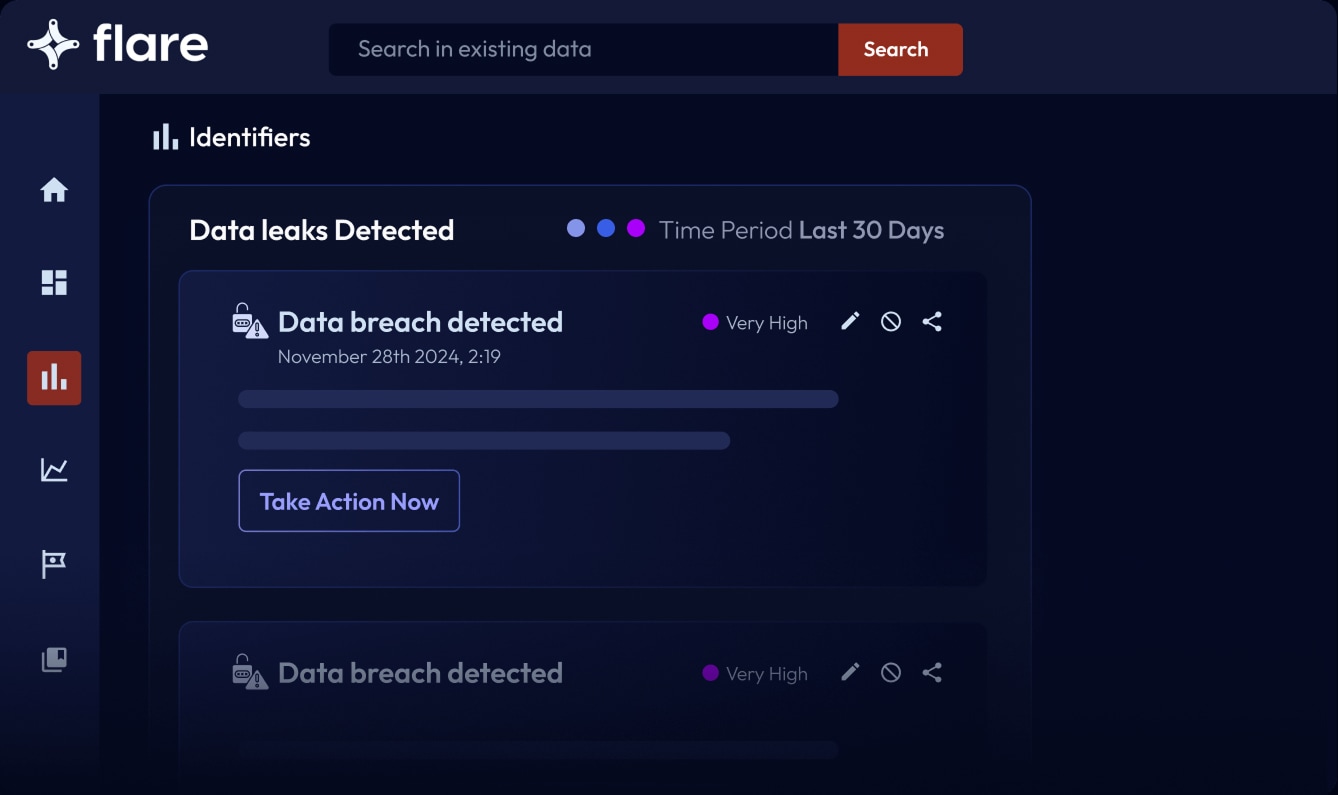
Strengthen Your Supply Chain by Proactively Managing Ransomware Risks
Start a Free Trial



Strengthen Your Digital Defenses
Manage Ransomware-Related Risks
The illicit economy of ransomware has never been healthier posing a major concern for senior leadership at businesses of all sizes and industry verticals. Additionally, third-party and supply chain risks are increasingly common attack vectors, attracting regulatory scrutiny and raising the stakes for security teams.
Flare Supply Chain Ransomware Exposure Monitoring delivers unique visibility and proactive security across your extended supply chain so you can effectively manage and mitigate threat exposures that exist within ransomware data leaks.
Start a Free TrialFlare Supply Chain Ransomware Exposure Monitoring delivers unique visibility and proactive security across your extended supply chain so you can effectively manage and mitigate threat exposures that exist within ransomware data leaks.
The Ultimate Security tool for Your Team
What Your Security Team Will Love about Flare
Versatility
Flare unifies the core elements of threat intelligence, digital risk protection, and attack surface management into a simple, flexible, and powerful Threat Exposure Management solution.
Accessibility
You don’t need to be a threat hunting master to use Flare. The platform is genuinely easy to use and typically set up in 30 minutes, making it accessible to GRC professionals.
Collaboration
Unlimited seat count means anyone at your organization can use Flare, presenting a unique collaboration opportunity for GRC and SecOps teams, leading to an improved overall security posture.
Robust Integrations
Easily integrate with SIEM, SOAR, Ticketing, and other core systems for alignment with existing security workflows.

“After a ransomware attack, Flare was the last piece of the puzzle of boosting our cybersecurity approach. Instead of manually scouring the dark web and other sources for hours, I can save up to 500 hours per year and have peace of mind with this Threat Exposure Management solution.”
President and General Manager, Manufacturing Company
Empower Your Defense with Flare's AI Security
How Flare Complements Your Ransomware Security Posture
Even with a strong ransomware prevention posture, it's highly likely that a member of your supply chain will be a victim at some point in the near future.
By leveraging AI-powered analytics and world-class threat intelligence of ransomware groups, Flare empowers businesses to identify and respond to threat exposures within minutes of their appearance.
Book a DemoProactive Risk Management
Allows you to take a proactive approach to ransomware-related supply chain risks.
Rapid Threat Identification
Faster identification of serious threat exposures found in ransomware leaks.
Effortless Investigation
Save time and resources compared to manual investigation methods.
Cutting-Edge Intelligence
Ensures your team is using the latest intelligence from the evolving ransomware cybercrime ecosystem.

Real-Time Detection for Continuous Protection
What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is an emerging strategic security program that integrates cyber threat intelligence (CTI), digital risk protection (DRP), external attack surface management (EASM), and other functions.
This convergence enables organizations to proactively identify, prioritize, and respond to the types of exposure threat actors most commonly leverage to attack companies.
Flare’s platform serves as the focal point for integrating exposure management throughout the security function creating continuous risk reduction and improving compliance posture.
Start a Free TrialCTEM is Gartner's Top Strategic Technology Trend for 2024
Companies implementing Threat Exposure Management processes will see a 66% decline in data breach risk by 2026
60% of organizations are actively developing or considering implementing a Continuous Threat Exposure Management Program
Practical Solutions for Ransomware Defense
Supply Chain Ransomware Exposure Monitoring Use Cases
Start a Free TrialVisibility Across Your Known and Unknown Supply Chain Entities
- Unrestricted access to Flare’s intelligence database
- Effortless monitoring of known third parties
- Apply your context to Flare’s intelligence for visibility into the unknown areas of your supply chain
Near Real-Time Alerting of Ransomware Leaks
- World-class coverage of ransomware threat actor platforms
- Near-real time updates of threat actor activity
- Nimble data collection methodologies
Rapid and Precise Risk Evaluation of Your Threat Exposures
- AI-powered file path analysis
- One-click file download request
- Detailed threat actor profiling and history
Boost Your Compliance Efforts with Contextual Intelligence
- Same-day time to value
- AI-powered custom and contextual reporting
- Robust API and Integrations
0+
Flare tracks over 50 of the world’s most active ransomware threat actor organizations including LockBit, CL0P, and ALPHV/BlackCat
0%
of victims opted not to pay the ransom, thereby accepting risk of data breach disclosure
(Coveware, 2023)
0
Average number of third parties and vendors affected per data breach.
(BlackKite, 2022)


Start Free Trial
Try Flare for Yourself
Experience Flare for yourself and see why is used by organization’s including federal law enforcement, Fortune 50 financial institutions, and software startups.




Essential Information in One Place
Explore ResourcesFeatured Resources
Explore Flare’s Resource Center for the latest research, security updates, expert blogs, and valuable insights.