
If cybercrime were a country, it would have the world’s third-largest gross domestic product (GDP). Cybercrime is worth $10.5 trillion, according to researchers, placing it just behind the U.S. and China’s economies. It’s also growing; the threat actor economy is projected to expand to $12.2 trillion by 2031.
As with any economy, cybercrime has stabilized, hardening into a system of sectors, specialists, supply chains, marketplaces and organized, profit-driven entities. Unfortunately, every dollar made by cybercrime is a dollar sucked out of a legitimate economy.
The cybercrime economy is vast and includes players of all kinds: from individuals buying toolkits to organized ransomware gangs to criminals backed by nation-states. However, there is order within this economy. Certain sectors are more lucrative than others, for example, and threat actors tend to use specific tools for communication and payment.
Why should security teams understand the economics behind cybercrime? Because threat actors operate on business logic: profit, efficiency, risk management. To build proactive defenses, it’s important to analyze their incentives and structures.
Why the Cyber Threat Economy Keeps Growing
Cybercrime is growing for one core reason: it works. Despite increasing crackdowns by government and law enforcement, conditions favor threat actors.
- Low risk, high reward: The risk-to-reward ratio is high for cyber criminals. Many actors operate in jurisdictions with weak extradition laws or nonexistent enforcement. Attribution is difficult, prosecution is rare, and penalties are inconsistent across borders. Considering the possible gains of a successful attack, it’s not surprising that so many bad actors make the choice to become cybercriminals.
- Low bar to entry: Threat actors don’t have to be coders to get into cybercrime. Thanks to plug-and-play malware, RaaS platforms, and phishing kits, anyone with a few hundred dollars can launch an attack.
- High demand for stolen data: The reason threat actors steal data is that there’s a demand for it. Stealer logs, credentials, payment information, corporate IP, and other data is routinely sold in illicit marketplaces.
- Underinvestment in defense: Despite increasing awareness, many organizations still rely on outdated tech stacks, lack MFA, or don’t monitor for initial access resale. This can create gaps that threat actors are able to exploit.
- Decentralized infrastructure: Threat actors don’t meet in places that are easy to find. Instead they use the dark web and decentralized messaging platforms — like Telegram — for communication and payment. Telegram, in particular, has become a favorite platform for cybercrime.
Telegram: A Marketplace for Cybercrime
In order to do business, threat actors need a place to meet. Telegram, a secure messaging app that offers encryption, has increasingly become that marketplace.
This is likely because Telegram is both anonymous and easy to use. Telegram users can quickly create new accounts or rename existing accounts, create new channels and groups, and search for channels dedicated to specific types of cybercrime.
Telegram also eliminates the middle man. On dark web forums, sellers might have to pay escrow. However, on Telegram, threat actors can sell infostealer malware, stealer logs, or credentials on their own terms. This doesn’t mean the dark web forums aren’t being used, however. Plenty of cybercriminals use both Telegram and the dark web, as well as other messaging apps.
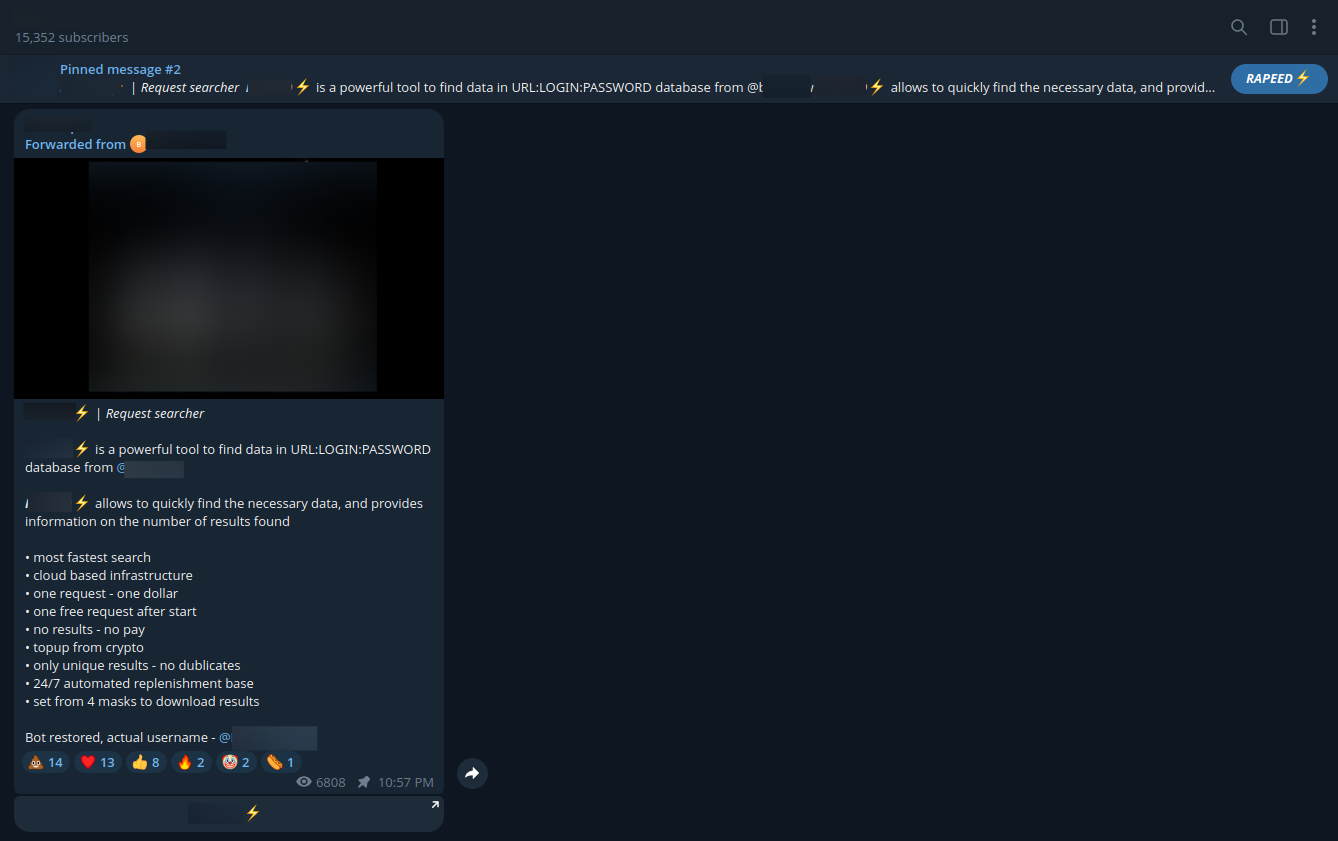
A threat actor advertises a stealer log ULP search bot on Telegram
The Malware-as-a-Service (MaaS) Ecosystem
Without Malware as a Service, most of the threat actors online wouldn’t be able to launch attacks. Many bad actors simply buy the ransomware or infostealers they’re using from a developer, many of whom operate much like legitimate Software-as-a-Service (SaaS) companies. Vendors offer support, automated subscription payments, and user dashboards.
The MaaS ecosystem includes infostealer malware.
The booming ransomware economy
One of the most profitable sectors in the threat actor economy is ransomware, and it’s also one of the most organized. Ransomware groups are increasingly sophisticated and operating like legitimate enterprises. For example, groups like LockBit and Conti are structured like companies with PR departments, HR policies, affiliate programs, and even customer service for victims trying to pay.
Ransomware is big business, profitable for two main reasons. First, ransomware gangs often hit high-yield targets and second, because there are several possible layers of extortion. Rather than simply asking for a ransom to return control of a system to a victim, threat actors also demand ransom for decryption or to prevent data exposure.
More recently, some groups are experimenting with new tactics, like using ChatGPT to summarize the contents of a breach, or selling stolen data on behalf of others.
Infostealers: the backbone of the threat economy
The ransomware economy runs on stealer logs.
Stealer logs are huge files, each containing a massive amount of information about one person, compiled by infostealer malware. These files include data, such as credentials, session cookies and tokens, browser data, cryptocurrency wallets and more.
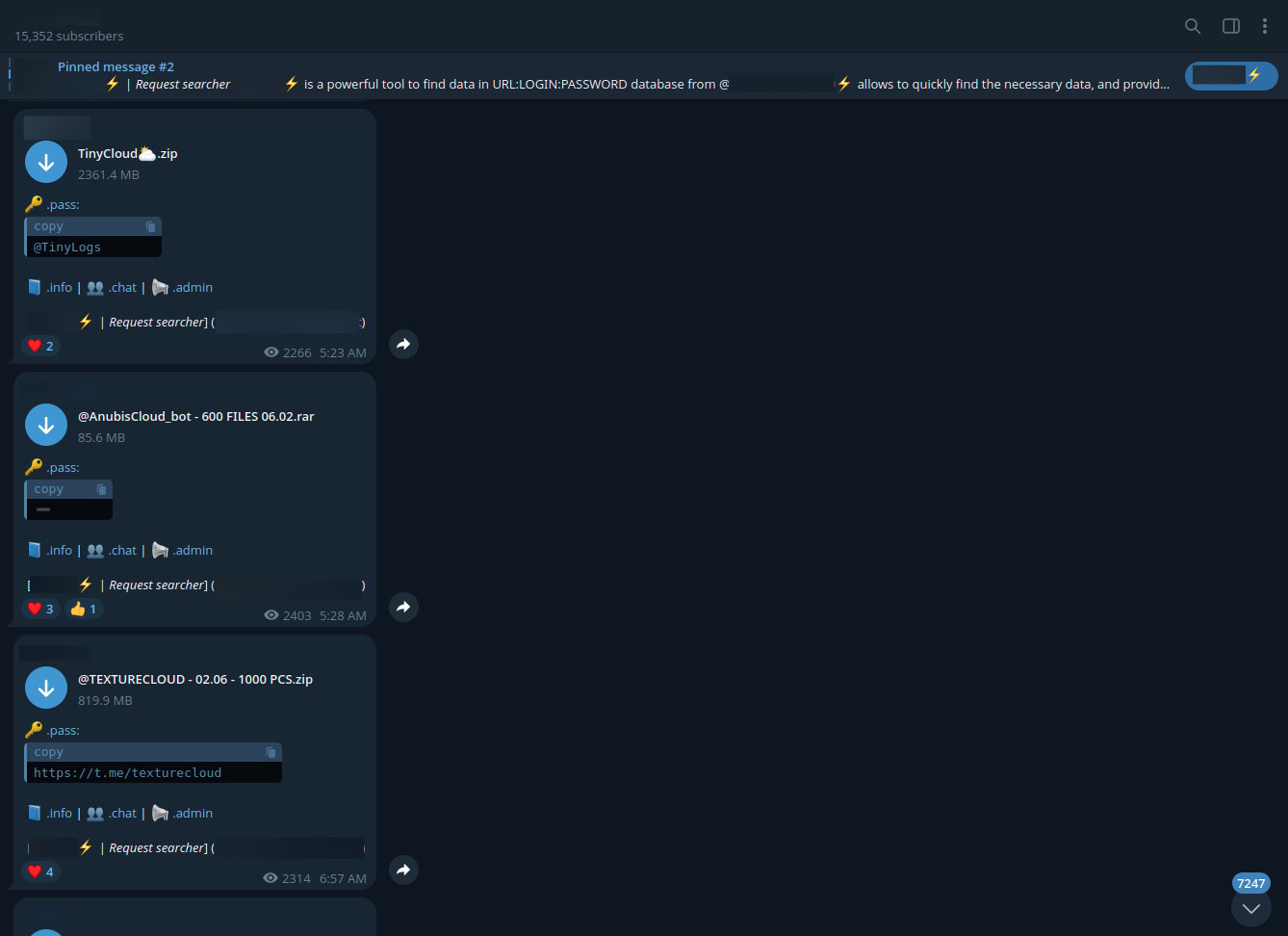
Threat actors post messages of bulk stealer log postings, with zip files containing hundreds of logs
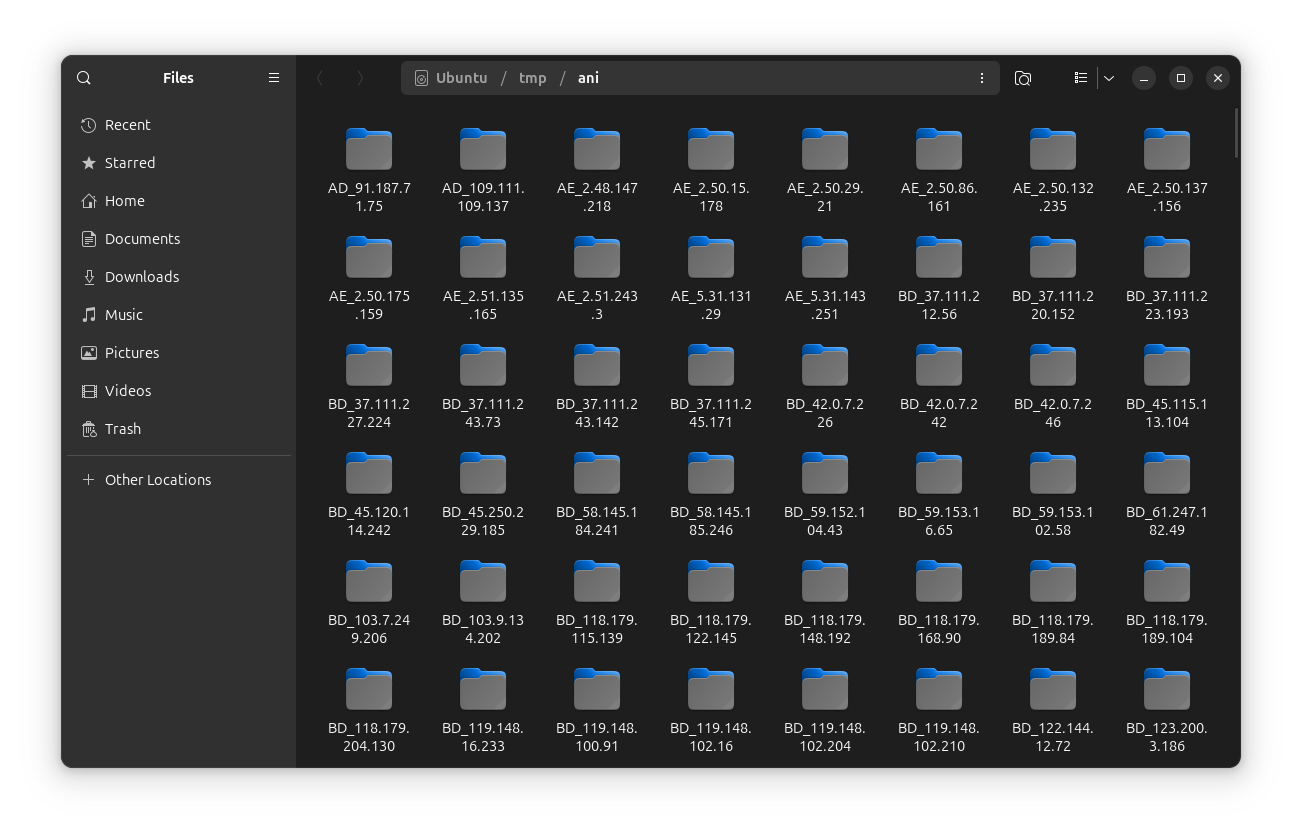
A zip file containing folders corresponding with each victim
In many ways, stealer logs are the backbone of the threat economy; they’re sold and distributed in illicit marketplaces. Their buyers then use that data to launch further attacks. For example, ransomware operators often look for stealer logs that contain specific information, or target certain industries.
Like ransomware, infostealers are sold as toolkits and malware as a service. The pricing structure varies, depending on the stealer variant:
Standard variants:
- Monthly subscription model
- Price range: $130-170 USD
- Payments accepted in cryptocurrency
- Includes C2 infrastructure hosting
Specialized variants:
- macOS stealers command premium pricing
- Higher prices reflect limited competition in the Mac malware space, however, there has recently been an increase in the number of stealers targeting macOS, so this may change.
Laundering the Spoils
If the threat economy proves anything, it’s that crime pays. But unfortunately (for threat actors), crime pays in traceable cryptocurrency. One of the biggest challenges comes after a payday is cleaning money. Laundering stolen money is risky and difficult, and may attract the notice of authorities or bigger malicious actors in the threat actor ecosystem. Turning stolen money into legally-usable cash usually is a multi-step process that requires planning.
- Cleaning the money: This is the easy step. Cybercriminals “clean” cryptocurrency by swapping it at an exchange or using a mixer — a service that obfuscates the origin of cryptocurrency by blending funds from multiple users — making it harder to trace the source and destination of the coins. However, this doesn’t make the funds legal or usable.
- Legalizing cleaned money: Just because money has been cleaned doesn’t make it usable or legal. Legal income can be openly declared, invested, or spent without attracting scrutiny. Threat actors tend to be secretive about how exactly they accomplish this step.
Despite the concerns around laundering, most criminals don’t bring in enough cash to require it. Legalizing stolen money is a problem for the most profitable cybercriminals, like the owners of ransomware-as-a-service operations and other organized groups.
The Cybercrime Economy’s Future
The cybercrime economy isn’t slowing down; it’s evolving, expanding, and operating with a level of professionalism that rivals legitimate businesses. From ransomware operations and infostealer markets to the rise of Telegram as a cybercrime hub, today’s threat actors are agile, organized, and increasingly difficult to track.
To defend against these threat actors, security teams benefit from greater visibility—not just into their own infrastructure, but into the dark corners of the internet where stolen data is sold, access is brokered, and tools are traded.
Follow the Cyber Threat Economy with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.

