
Stealer logs are at the center of today’s cybercrime economy. They’ve become a key enabler for ransomware, account takeovers, and corporate breaches, and law enforcement has taken notice.
In part one of our Leaky Weekly cybercrime current events podcast mini-series: Use a Stealer Log, Go to Prison, we cover the importance of stealer logs in cybercrime today. Host and security researcher Nick Ascoli discusses two recent cases in which stealer log use (or related tactics) led to high-profile arrests of the threat actor IntelBroker, and threat actors who attacked retail companies in the UK (attributed to Scattered Spider).
Tune into Use a Stealer Log, Go to Prison (Part One) below at Spotify, at Apple Podcasts, check out the video episode on YouTube (below), and/or keep reading this article for the highlights. Check out the second part here.
What Are Stealer Logs?
A stealer log is the packaged output of an infostealer malware infection. When a victim unknowingly installs malicious software, which is often hidden inside cracked software downloads or poisoned ads, the malware quietly harvests data from the device.
These logs typically include:
- Usernames and passwords saved in the browser
- Active session cookies that bypass multi-factor authentication
- Financial information such as banking credentials
- Web browser fingerprints and autofill data
- Desktop files and screenshots, often showing compromised security tools
In short, each log is like a digital skeleton key, often zipped and sent to a command-and-control (C2) server for operators to sell or exploit.
Why Stealer Logs Matter in 2025
The 2025 Verizon Data Breach Investigations Report (DBIR), which Flare contributed to, found that 88% of web application attacks begin with stolen credentials. Stealer logs are a prime source of these credentials.
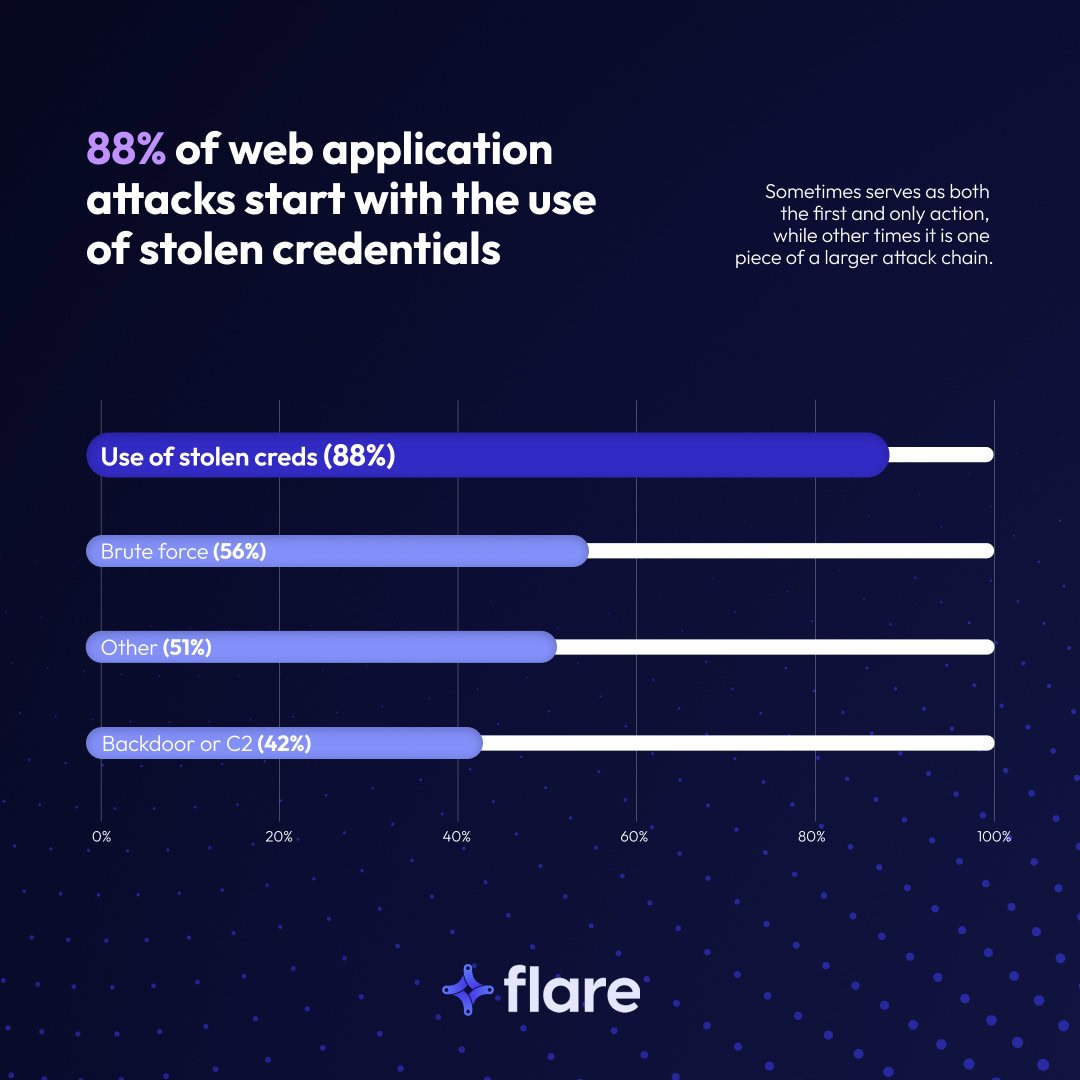
According to the DBIR, 88% web application attacks begin with stolen credentials
Our own analysis at Flare showed that 46% of stealer logs collected from personal devices contained corporate credentials, meaning personal browsing habits can directly expose corporate networks.
The link to ransomware is also becoming clearer. The DBIR highlights that the median time between a ransomware victim disclosure and the appearance of related stolen credentials is just two days. This strongly suggests stealer logs are contributing to ransomware operations.
Why Threat Actors Use Stealer Logs
Threat actors gravitate to using stealer logs for three main reasons:
- Lower barrier to entry: Infostealer malware can be purchased for around $100 USD per month on dark web marketplaces. Even threat actors with no technical skills can operate them using pre-built C2 infrastructure.
- Automated credential prioritization: Infostealer panels can automatically flag “high-value” credentials, such as corporate SaaS logins (Okta, JumpCloud, Auth0), banking accounts, and session cookies. This automation streamlines access for threat actors.
- Financial gain: Stealer logs with high-value credentials can be sold to other threat actors. Prominent threat actor communities, dark web forums, and illicit Telegram channels facilitate the sale of stealer logs.
This combination makes stealer logs one of the most accessible, profitable, and destructive tools in the cybercrime ecosystem.
IntelBroker, BreachForums Administrator, Arrested
One of the biggest cybercrime developments this summer came from the takedown of IntelBroker, a BreachForums administrator. Known for high-profile extortion campaigns against tech, telecom, and retail giants, IntelBroker’s identity was long shrouded in mystery.
Speculation swirled for years…was IntelBroker Iranian state-sponsored? A Serbian lone wolf? The truth came out on June 25, 2025, as U.S. prosecutors unsealed an indictment revealing IntelBroker as Kai West, a 25-year-old British national.
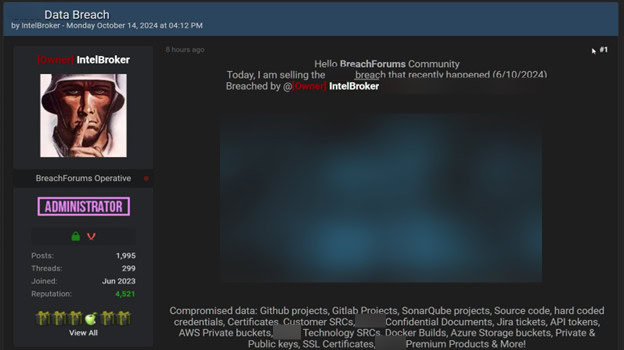
IntelBroker’s advertisement on BreachForums for selling leaked information
Key details from the case:
- Background: Formerly a Security Researcher Trainee at the UK’s National Crime Agency, allegedly brought in after a teenage arrest for swatting and bomb threats.
- What led law enforcement to uncover his identity: Accepted Bitcoin (instead of Monero) for a controlled purchase, later withdrawing it to a Coinbase account linked to his real identity
- Arrest: Taken into custody in France following an international law enforcement operation targeting BreachForums admins
- Charges: Conspiracy to commit computer intrusions (5 years), conspiracy to commit wire fraud (20 years), accessing a protected computer (5 years), and wire fraud (20 years)
IntelBroker’s arrest highlights the longevity of threat actor personas and coordinated law enforcement efforts against cybercrime.
Ransomware Attacks on UK Retail Giants
The UK’s retail sector has been hit by damaging ransomware attacks, and some of the suspects have been arrested recently. On July 10, 2025, the National Crime Agency announced the arrests of four individuals: a 20-year-old woman in Staffordshire and three males aged 17–19 across London, the West Midlands, and Latvia.
The group is accused of using the DragonForce encrypter in a spree of ransomware attacks against major retailers including:
- Marks & Spencer (M&S)
- Co-op
- Harrods
The threat actors wrote to the CEO of M&S with a picture of a dragon attached.

Image of a dragon attached to the email for the CEO
The April attack on M&S was especially damaging, forcing the company to suspend online shopping for nearly seven weeks and costing an estimated £300 million ($400 million USD) in lost profit.
Investigators tied the group to Scattered Spider, a loose network of threat actors often organized via Discord. Unlike nation-state APTs, Scattered Spider operates more like a chaotic subculture—young, opportunistic, and highly destructive.
The suspects now face charges under the Computer Misuse Act, as well as accusations of blackmail, money laundering, and participation in organized crime.
Stealer Logs Contribute to Lowering the Barrier to Entry for Cybercrime
Stealer logs are at the core of the modern cybercrime landscape, as they can be behind powering account takeovers, ransomware campaigns, and corporate breaches. Because of this, more threat actors are trying to take advantage of them.
Security teams can stay ahead of threat actors by monitoring for stealer logs to mitigate risks before malicious actors abuse them.
Leaky Weekly and Flare Academy
For a deeper dive into these trends, check out more episodes at YouTube, Spotify, or Apple Podcasts.
Join us at Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick and Tammy!), and more.

