
If cybercrime were a country, it would be the world’s third-largest economy, and by the end of this year, cybercrime will have cost the global economy $10.5 trillion.
The amount of money lost to cybercrime has been steadily (and rapidly) increasing for years. In 2018, the Center for Strategic and International Studies projected that cybercrime would cost the world an approximate $600 billion annually, nearly 1% of global GDP. That annual cost has been on the rise, although the sheer size of the cybercrime world is slowing its growth. Cybersecurity Ventures estimates that the sector will grow by 2.5% every year until 2031, when the cybercrime sector will cost the world $12.2 trillion a year.
This increase can be attributed to the evolution of the increasingly sophisticated cybercrime economy: a booming ecosystem that includes specialization, supply chains, and criminal enterprises that operate like legitimate businesses.
What does the “Cybercrime Assembly Line” Look Like in 2025?
When we published our article about the cybersecurity assembly line back in early 2023, we wrote about the increasing commodification of cybercrime. Two years later, despite high-profile arrests and government crackdowns on ransomware gangs and Telegram forums, the cybercrime economy is just as efficient as it was in 2023 — if not more so.
Even more of “everything as a service”
The cybercrime industry has very much embraced the “as a Service” (aaS) business model. Ransomware as a Service (RaaS), for example, works like legitimate software as a service (SaaS) platforms: affiliates log into the platform to see their dashboard, which shows them all their metrics, allows them to manage their attacks, and claim victims.
Post-Cronos Ransomware as a Service
This approach to cybercrime was popularized and refined by ransomware gangs like LockBit. LockBit ran an extensive affiliate program, focused on double extortion tactics, and dominated the RaaS sector for years. This approach was successful, but it wasn’t the norm, even in 2023. At the time, there were still ransomware gangs that hadn’t adopted affiliates or double extortion.
LockBit was taken down in 2024 by Operation Cronos, creating a more decentralized RaaS industry with several smaller, newer ransomware gangs. However, the model used by LockBit and similar gangs is now the norm in RaaS circles. The affiliate model, multiple extortion and the other hallmarks of RaaS are undeniably here to stay.
Stealers as a Service
Infostealers are another good example of specialization in the Malware as a Service (MaaS) industry. Infostealer malware is a form of Remote Access Trojan. Designed to steal user information, Infostealers target the information stored in a victim’s browser, such as:
- saved passwords
- form-fill data
- session cookies
The malware then exfiltrates the stolen data to a dedicated C2 infrastructure, and packages up the stolen information into a file called a stealer log, which is then sold to other threat actors, who use the logs to launch other kinds of attacks.
Phishing as a Service
Another specialized part of the MaaS market is Phishing as a Service, which allows threat actors to easily set up phishing pages thanks to various phishing kits offered in illicit marketplaces. Again, this model operates like a legitimate business model: threat actors pay a monthly fee and are sent regularly-updated kits by the developer.
Telegram: Go-to Messaging App for Threat Actors
When Telegram CEO Pavel Durov was arrested in August 2024, there was some concern in the cybercrime community about the use of Telegram for illicit activities, but Telegram is still a functioning marketplace for cybercriminals.
There have been crackdowns on Telegram over the past year and channels have been getting taken down because they’ve broken the terms of service.
Telegram’s error message shows up for an illicit channel that existed before that has been taken down
Occasionally, entire groups of channels will be taken down at once. However, this is more of a barrier than an obstacle for threat actors.
Multiple illicit Telegram channels that were once operating have been shut down since the more widespread crackdowns
Telegram is still attractive for the cybercrime sector; it’s free, it’s easy to use, and it’s simple to set up a new channel after an old one has been taken down. It’s also where the buyers are, so sellers are not likely to abandon it anytime soon.
The Dark Web and AI
Artificial Intelligence (AI) has changed the legitimate business world, and so you might think it would be doing the same for the cybercrime economy. However, that doesn’t appear to be the full story. Generative AI has accelerated some areas of cybercrime but not all; it’s not great at creating malware, exploiting networks, finding vulnerabilities, or writing bug reports.
That has not stopped developers from trying to sell criminal AI tools to other threat actors, however.
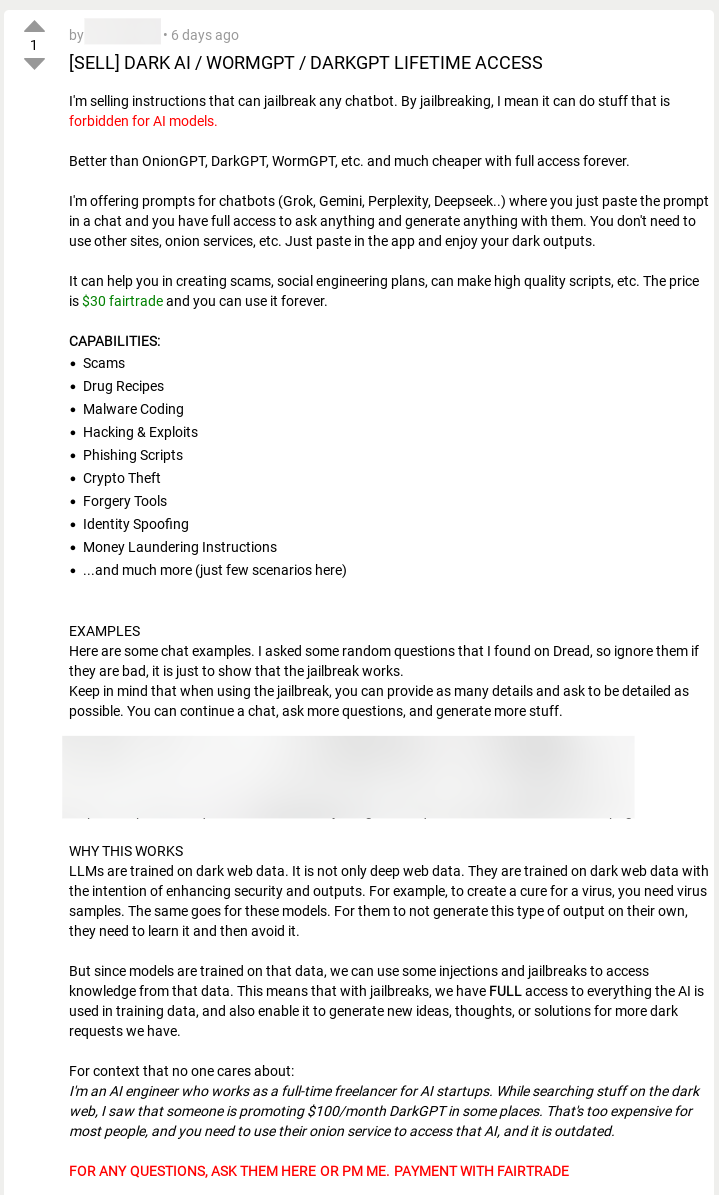
Threat actor advertises jailbroken AI tools that are trained on dark web data and can override security measures
WormGPT, DarkGPT, and FraudGPT are all being marketed in the cybercrime economy as jailbroken GPTs (even if they’re not true GPTs) optimized for fraud and crime. However, the reviews from users aren’t very good, and there doesn’t appear widespread AI use, at least not for the technical side of cybercrime.
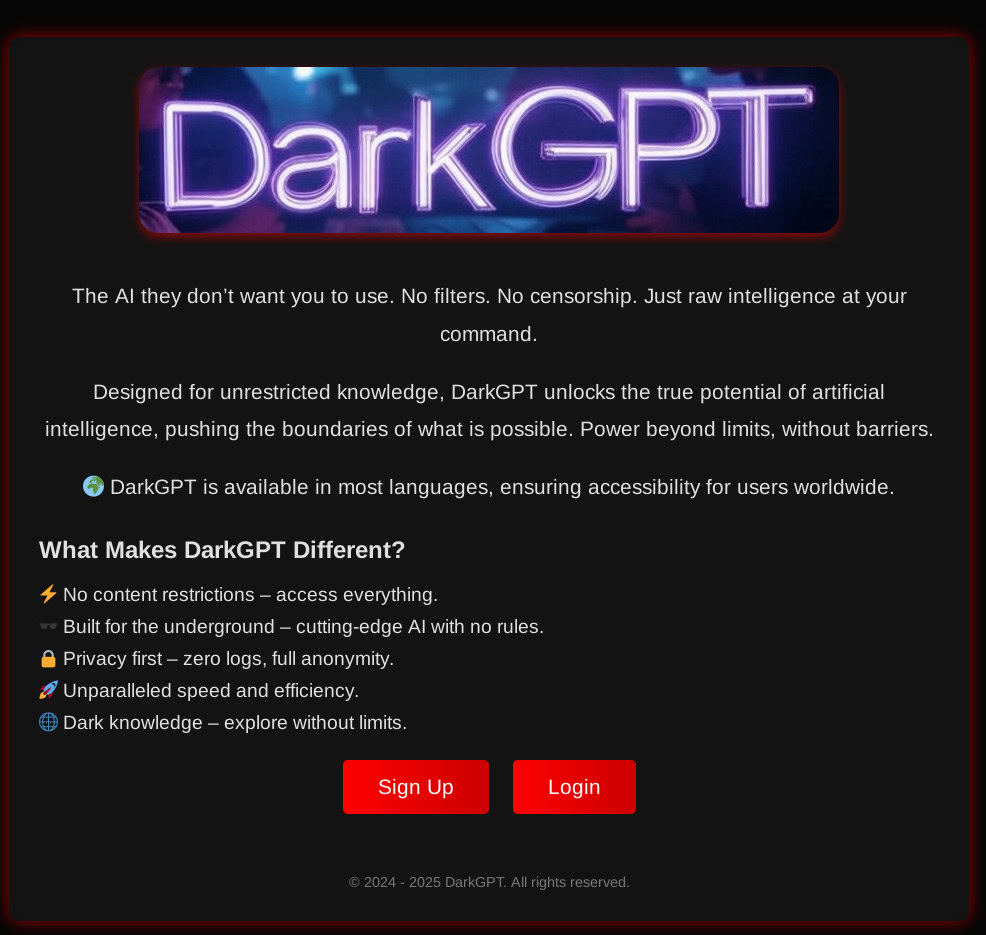
Advertisement for DarkGPT, which allegedly is built without rules and without content restrictions
AI Use in Cybercrime
Though not all uses of AI are suitable for cybercrime, it has accelerated the precision of phishing and vishing attacks. AI can create more believable phishing messages with a sense of urgency, which is especially useful for threat actors who aren’t fluent in the language they are creating phishing messages in.
Getting Ahead of Threat Actors
Threat actors are constantly refining their models. They evolve their tactics, share knowledge within criminal networks, and adopt new technologies with remarkable speed. In contrast, many security teams must navigate internal processes, compliance requirements, and resource constraints that can slow their ability to respond to threats.
It can be difficult for security teams to keep up with changing cybercrime tactics, but by evolving your security posture and tooling, you can stay ahead.
Disrupt the Cybercrime Supply Chain with Flare
Flare’s Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.

