Back in 2018, the Center for Strategic and International Studies came to the conclusion that cybercrime cost the world an approximate $600 billion annually, nearly 1% of global GDP. The cyber threat landscape has been constantly evolving, and the amount of money lost to cybercrime has only been increasing. According to IBM, the cost of data breaches has increased 12.7% in the last two years, and the number of cybercrime incidents has never been higher. Unfortunately, all evidence seems to point towards this tendency maintaining its course, as threat actors are always looking for ways to improve their attacks and gain in efficiency.
A factor that may be contributing to the sophistication of threat actors is the commodification of cybercrime. Just like legitimate modern supply chains, we are seeing a niche specialization and efficiency gains as a result of threat actors becoming proficient at one specific part of the cybercrime supply chain. The adoption and evolution of the “as a Service” (aaS) business model in the cybercrime industry has increased the ease of committing cybercrime; providing easier and convenient access to advanced tools and services to even the least evolved of threat actors.
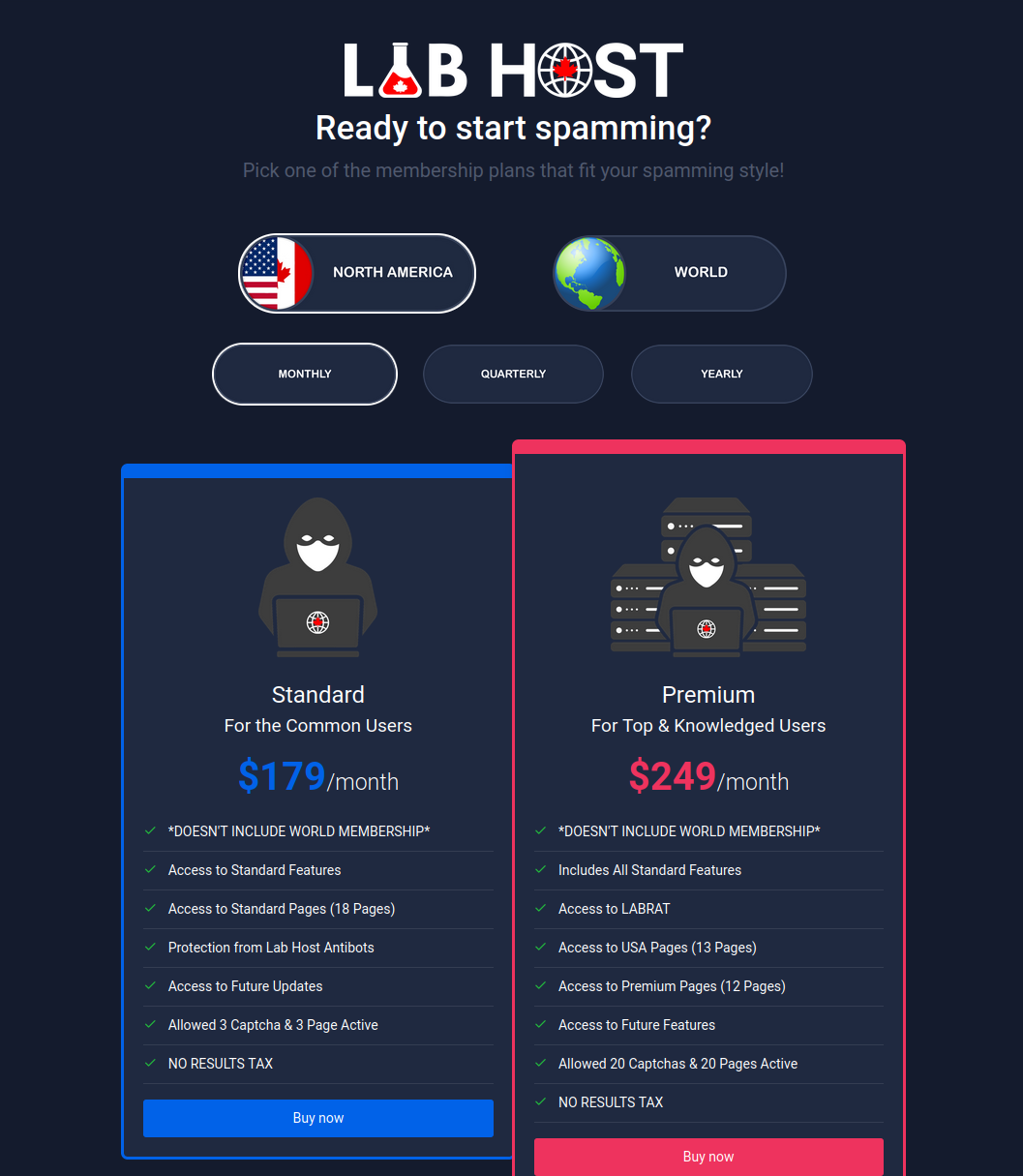
Anything as a Service
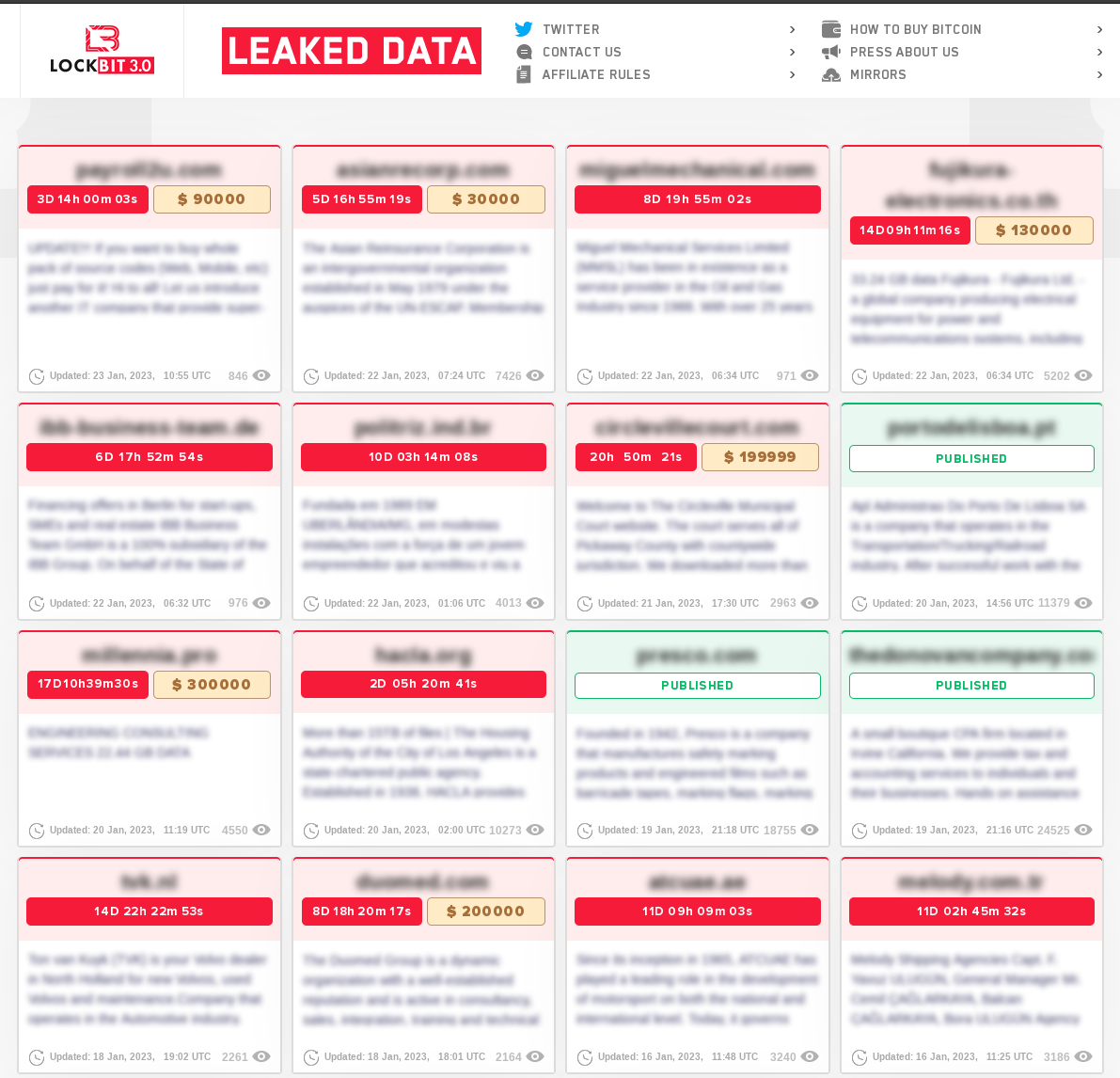
The expanding adoption of Ransomware as a Service (RaaS) allowed ransomware group LockBit to gain in notoriety and volume, to the point of being the most active ransomware in the world. Following an aaS model, the LockBit ransomware is being used by affiliates and Initial Access Brokers (IAB) to infect a targeted organization and extract payments, after which the LockBit group may keep up to ¼ of the ransom payment. This division of labor allows each concerned party to refine their operation; with the RaaS operators focusing on improving and updating their malicious software, and affiliates/IABs to develop and optimize ways to penetrate systems.
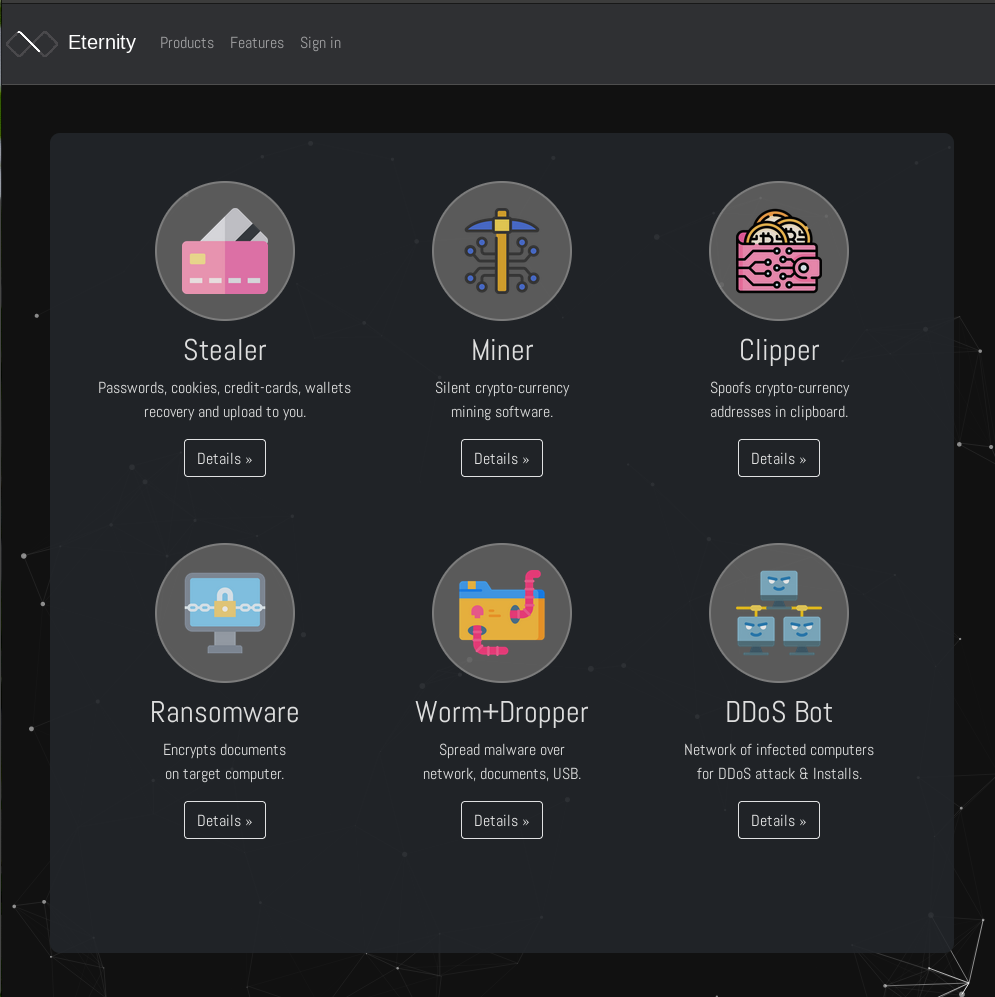
Following the same idea, it should come as no surprise to see the aaS model being adopted at large in other aspects of cybercrime; malicious actors offering Phishing as a Service, where threat actors can easily set-up phishing pages from various phishing kits offering on rented Virtual Private Servers (VPS); botnet operators renting their infrastructure in order to perform a Distributed Denial of Service (DDoS) attack on a targeted network (DDoS as a Service); Stealer Malware developers being able to focus on developing malware by following the Malware as a Service model, for example, the RedLine stealer malware; or even sometimes all of the above.
Integrate the world’s easiest to use and most comprehensive cybercrime database into your security program in 30 minutes.
This evolution in the cybercrime supply chain represents a major concern for everyone, and a growing challenge for the cybersecurity industry as a whole. The ease of use provided by those services, as well as a comprehensive support system provided by the service operators, may well lead to increased adoption of sophisticated tools as well as a new generation of threat actors attracted to the ease of use offered. The refinement of the tools available to threat actors, paired with the ease of (relatively) anonymous communication the Telegram message application provides, will undoubtedly lead to an increasing amount of advanced threats tomorrow’s organizations will have to face.
“Know thy enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle.” – Sun Tzu, The Art of War
Cyber attacks are, and will remain, a major issue for today’s organizations. Being better prepared starts with knowledge; knowing how threat actors operate, their tactics and their techniques is of vital importance. This can help in being able to respond to the inevitable cyber attacks and mitigate their impact.
Disrupt the Cybercrime Supply Chain with Flare
As threat actors’ methods develop in complexity, cyber teams need to stay ahead of them. Accelerate your organization’s threat identification speed by five times with Flare. Book a demo to learn how Flare can help your team.