This article was updated on December 22nd, 2025.
Initial access brokers (IABs) are a special class of threat actors that focus on gaining an initial foothold on enterprise networks that they auction off on cybercrime forums such as RAMP, Exploit, and XSS. Initial access brokers are a key element in the cybercrime supply chain – providing ransomware affiliates and groups with a key ingredient needed to carry out sophisticated attacks against organizations.

An IAB post on the Russian Language cybercrime forum Exploit
What Role Do Initial Access Brokers Play in the Cybercrime Ecosystem?
Initial access brokers (IABs) serve as specialized middlemen in the cybercrime supply chain, focusing exclusively on gaining unauthorized access to corporate networks and then selling that access to other threat actors. Rather than conducting full attacks themselves, IABs invest their time and resources into compromising organizations through methods like exploiting vulnerable VPNs, leveraging stolen credentials from stealer logs, or conducting targeted phishing campaigns against employees with privileged access. Once they establish a foothold, they package and list the access for sale on dark web forums and marketplaces, typically advertising details like the victim’s industry, annual revenue, number of endpoints, and the type of access obtained (RDP, VPN, Citrix, or domain admin credentials).
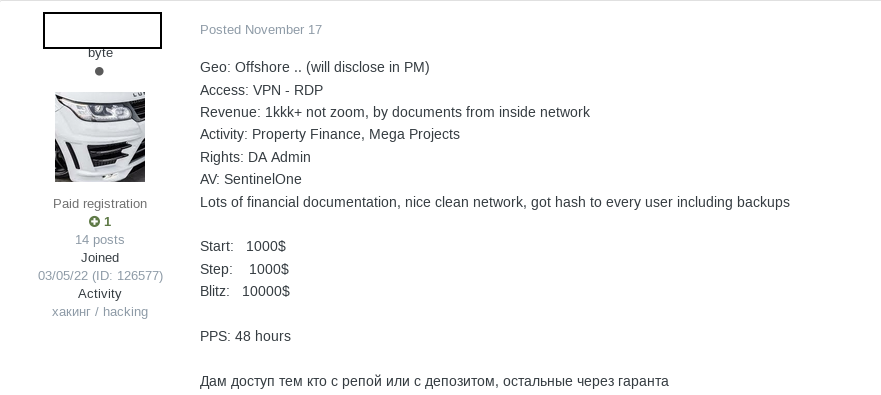
IAB post
This specialization has dramatically lowered the barrier to entry for ransomware operators and other cybercriminals who lack the technical skills or patience to breach networks themselves. A ransomware affiliate can simply purchase verified access to a Fortune 500 company for anywhere from $500 to $50,000 depending on the target’s size and the quality of access, then immediately begin lateral movement and data exfiltration. This division of labor has accelerated the pace of ransomware attacks and made the overall ecosystem more efficient and dangerous. IABs effectively turn network compromise into a commodity, allowing attackers to scale their operations without scaling their intrusion capabilities.
The relationship between IABs and ransomware groups has become increasingly formalized, with some ransomware-as-a-service (RaaS) operations maintaining preferred relationships with specific brokers or even bringing IAB capabilities in-house. Monitoring IAB listings on forums like Exploit, XSS, and RAMP has become a critical function for threat intelligence teams, as spotting your organization’s access for sale often represents the last opportunity to intervene before a ransomware deployment or major data breach.
The Structure of an IAB Post
Initial Access Brokers and Ransomware Groups
What the LockBit-IAB Conversation Teaches Us About Ransomware Operations
The leaked conversation between LockBit and an initial access broker operating under the username “aa” on the XSS forum provides a rare window into the operational dynamics between ransomware operators and access brokers. One of the most striking revelations is the clear division of labor and specialization within the ransomware ecosystem. The IAB “aa” explicitly states that he does not understand antivirus evasion or backup deletion, and that he “always just handed them off” after obtaining domain admin privileges. His value lies entirely in the initial compromise and privilege escalation, not in the technical execution of the ransomware attack itself. This specialization allows IABs to focus on what they do best while ransomware affiliates handle the complex work of evading EDR solutions, exfiltrating data, and deploying encryptors.
The conversation also reveals the sophisticated tiering system that major ransomware-as-a-service operations use to manage their affiliate networks. LockBit repeatedly references “top affiliates” versus less experienced ones, explaining that he distributes access based on complexity. Networks protected by advanced EDR solutions go to affiliates “proven over the years” who “have been paid millions of dollars,” while simpler targets without robust security controls go to less skilled operators. This matching of target difficulty to affiliate capability maximizes the overall success rate of the operation. LockBit also demonstrates the role of the RaaS operator as a central coordinator, managing multiple simultaneous attacks across different affiliates while personally handling ransom negotiations that can stretch for weeks.
Spot IAB Listings Before Attackers Strike
Flare monitors XSS, Exploit, RAMP, and other forums where Initial Access Brokers sell corporate network access. Get alerted when your organization or third-party vendors appear in listings.
Perhaps most instructive is the payment dispute that ultimately led to LockBit’s ban from XSS. The IAB expected a fair, fixed percentage (around 25%) for providing high-quality access with domain admin credentials already obtained. LockBit countered with a tiered structure starting at just 10% and increasing by 1% per successful ransom, up to a maximum of 20%, arguing that this would incentivize the IAB to provide more volume. The IAB pushed back, noting that he was “doing half the work” by delivering domain admin access ready for immediate exploitation. This disagreement highlights the tension inherent in criminal partnerships where there are no enforceable contracts, and demonstrates why forum arbitration systems exist to mediate disputes. When LockBit refused to pay what the IAB considered fair compensation for Access1, the resulting arbitration case damaged LockBit’s reputation and showed that even the most prolific ransomware operations depend on maintaining trust within the cybercriminal community.
How Do IABs Get Access to Networks?
IABs focus on gaining unauthorized access to networks by exploiting the weakest links in an organization’s security posture. Phishing emails remain one of the most effective techniques, with IABs crafting targeted spear-phishing campaigns aimed at employees with elevated privileges such as IT administrators, finance staff, or executives. These emails often impersonate trusted vendors, internal colleagues, or service providers to trick recipients into clicking malicious links or entering credentials on spoofed login pages. More sophisticated IABs conduct reconnaissance using LinkedIn and corporate websites to personalize their lures and increase success rates.
Credential-based attacks represent another major vector for initial access. Brute-force attacks systematically attempt common passwords against externally exposed services like VPNs, Remote Desktop Protocol (RDP), Citrix gateways, and webmail portals. Password spraying takes a more measured approach, testing a small number of commonly used passwords across many accounts to avoid triggering lockout thresholds. IABs frequently combine these techniques with credential stuffing, using username and password combinations leaked from previous data breaches to exploit password reuse across personal and corporate accounts. The explosion of stealer logs on Telegram and dark web marketplaces has made this approach increasingly effective, as IABs can purchase fresh credentials that include corporate SSO cookies capable of bypassing multi-factor authentication entirely.
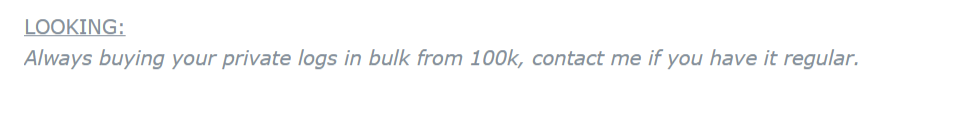
An IAB on XSS Advertises they are seeking to purchase stealer logs in bulk
How Can you Defend Against Access Brokers?
- Monitor IAB forums: IABs understandably don’t want their victims to learn that their data is for sale. For this reason, their posts in forums are anonymized. However, it’s still worth monitoring IAB forums; combination of geography, revenue, industry, and type of access may be enough information to provide some organizations advanced notice that they have potentially been compromised. Flare recommends monitoring Exploit, XSS, and other IAB forums to receive advanced notice that access to your environment may be for sale.
- Monitor stealer logs: Many threat actors distribute stealer logs across forums and Telegram channels. The stealer logs are likely a source of vectors for IABs, which may sift through enormous numbers of logs to find those with RDP, VPN, and other forms of corporate access which can be established, expanded, and resold.
To learn more about stealer logs and a massive continuous data leak, read the report Breached Identities and Infostealers: One of the Largest Ongoing Data Leaks in History.
Initial Access Brokers and Flare
Flare provides the leading Threat Exposure Management (TEM) solution for organizations. Our technology constantly scans the online world, including the clear & dark web, to discover unknown events, automatically prioritize risks, and deliver actionable intelligence you can use instantly to improve security. Protect your intellectual property from IABs by using Flare’s automated platform to scan for stolen data as well as mentions of your assets or organization.
Our solution integrates into your security program in 30 minutes to provide your team with actionable intelligence and automated remediation for high-risk exposure. See it yourself with our free trial.


