by Eric Clay and Zaid Osta
This report conducts a case study on a large sample of initial access broker (IAB) posts on the Russian-language hacking forum Exploit.in (hereinafter referred to as “Exploit”), targeting critical infrastructure in NATO member states across Europe and North America. We first examine the anatomy of typical IAB posts and explore recent sample IAB posts from entities within NATO member states.
IABs are key players in the cybercrime landscape. They infiltrate systems and gain unauthorized access through various techniques, including spear-phishing, exploiting unpatched vulnerabilities, and leveraging leaked and stolen credentials. Their primary goal is to establish persistence in these environments, not to conduct the final stages of a cyberattack, but rather to sell this access to other malicious actors. Future buyers might use the access for deploying ransomware, data theft, or other criminal activities.
Key Findings
- Pervasive Threat of IABs in NATO Countries: IABs are increasingly targeting entities within NATO member states, indicating a persistent and geographically diverse cyberthreat landscape. Our case study, analyzing hundreds of IAB postings on the Exploit forum, reveals recent activities in 21 out of 31 NATO countries. This underscores their extensive reach and the consistent potential threat they pose to national security and economic stability.
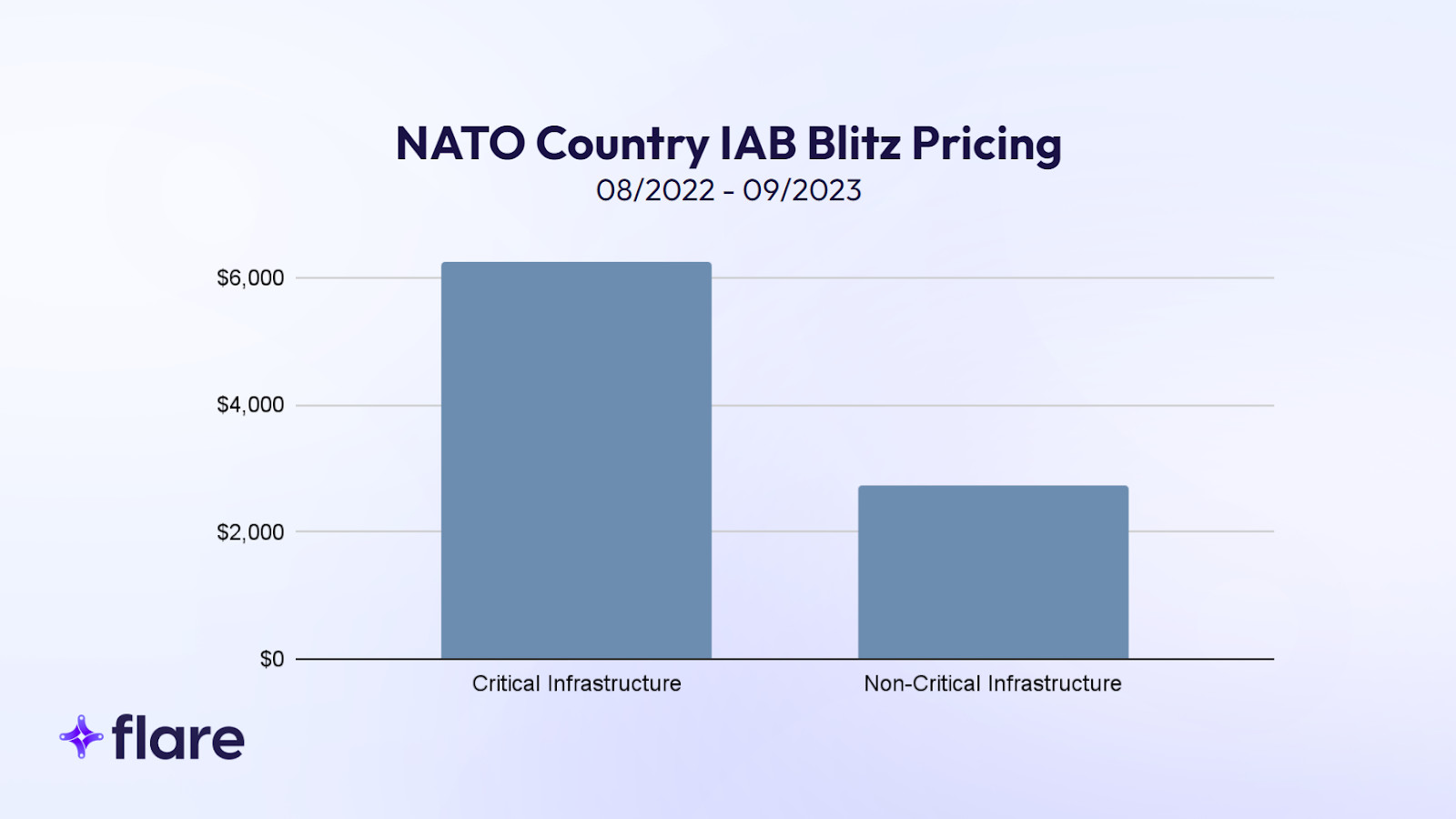
- High Value of Critical Infrastructure Access: The data shows that access to critical infrastructure sectors, as defined by CISA, commands notably higher prices in the cybercrime market. The average blitz price (“buy it now” price) for access in NATO countries is $6,396, significantly exceeding the average of $2,742 for other listings.
- Focused Targeting by Threat Actors: There is a marked concentration by certain threat actors on critical infrastructure sectors. Actors like “Roblette” and “Sandocan” display a disproportionate focus on these areas, suggesting strategic targeting by cybercriminals for potentially higher financial gains and greater impacts.
- U.S. Defense Sector as a High-Value Target: Our analysis indicates a clear trend of targeted cyberattacks on the U.S. defense sector. Access to U.S. defense contractors is priced on average at $5,750 for immediate purchase. This price point reflects the high value of these targets and suggests that threat actors recognize the significant impact of infiltrating defense-related systems.
- Complexity and Challenges: The analysis underlines the complexity of the cybercrime ecosystem and the challenges in identifying and responding to security breaches. The cautious approach of sellers on forums like Exploit, who often withhold sensitive details to avoid victim identification, is an example of the ongoing cat-and-mouse game between cybercriminals, researchers, and law enforcement.
Snapshot of IAB Postings in NATO Countries
The anatomy of an IAB post, with slight variations in wording, typically includes:
- Access Type: Usually RDP or VPN.
- Activity: Victim company’s industry.
- Revenue: Often sourced from data providers and services such as ZoomInfo.
- Level / Rights: Level of privileges obtained.
- Host / Network: Details about the victim’s network and security systems.
- Start, Step, and Blitz: Auction prices detailing the starting, bid increments, and ‘buy it now’ prices, respectively.
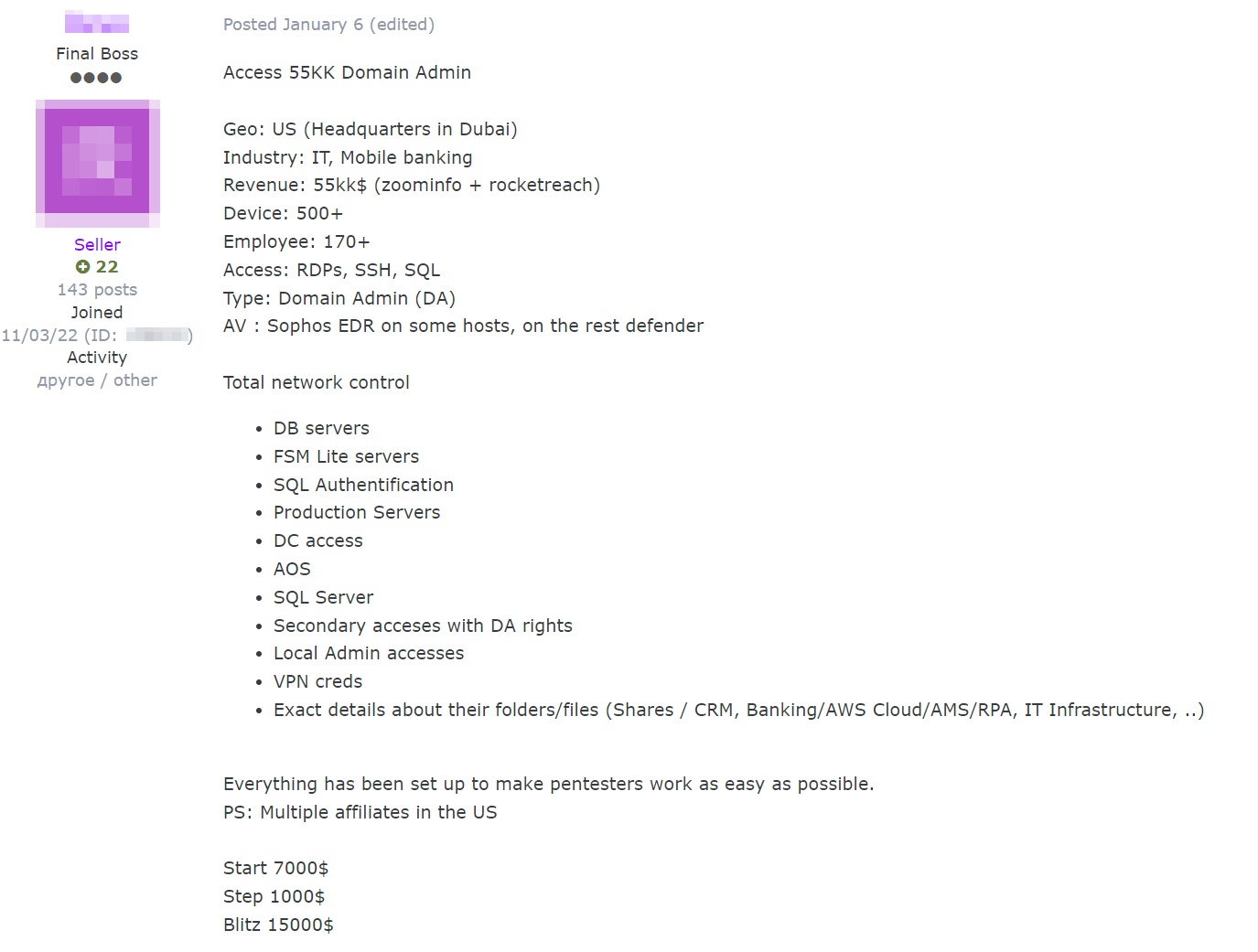
Sample 01/06/2024 IAB post on the Exploit forum.
To better understand the IAB threat landscape targeting entities in NATO member states, we present a snapshot of recent IAB sales from the Exploit forum. These sales, involving entities in 21 of the 31 NATO countries and primarily from the years 2023 and 2024, represent just a small sample of the multitude of IAB listings. Our search was limited to the Exploit forum, focusing exclusively on IAB sales and not other breaches like data leaks. As a result, some NATO countries are absent from this list.
In the brief selection below, we have opted to provide summaries rather than include original postings, which often contain sensitive details and screenshots, such as real server and workstation names from federal and private entities in NATO countries.
These sample summaries are a small part of the regular influx of IAB posts on cybercrime forums that Flare collects by the hour. Our overview aims to provide some insight into the diversity and reach of IAB activities affecting entities in NATO countries.
Belgium
- Date: 01/12/2024
- Industry: Commercial and Residential Construction
- Revenue: $12.8 million
- Technical: RDweb access (Microsoft’s Remote Desktop Web Client), limitations such as the disabling of PowerShell and CMD by the administrator.
- Auction: Start $500, Step $50, Blitz $600
- Notes: Access allows users to explore the network, “even the BACKUP folders.”
Canada
- Date: 01/11/2024
- Industry: Legal
- Revenue: $4.5 million
- Technical: RDP “via Tunnel,” domain admin privileges, 3 domain controllers, 400 users, 170 PCs, Windows Server 2012 R2 Standard
- Auction: Start $200, Step $100, Blitz $1,000
- Notes: Includes hashes of all users, suggesting potential for extensive unauthorized access within the firm’s network. Quick sale closure within 6 hours for a buyering offering a bid of “Blitz + 200$.”
Croatia
- Date: 07/04/2022
- Industry: Plastics Product Manufacturing
- Technical: RDP access with domain admin rights
- Auction: Start $35, Blitz $50
- Notes: On the same day, the threat actor responded to their own post writing that the sale had been “closed,” indicating a quick sale at the blitz price.
Denmark
- Date: 12/23/2022
- Industry: Business Services
- Revenue: Over $5 million
- Technical: RDWeb access, Windows Server 2012R2, Kaspersky Lab antivirus, 110+ PCs, MySQL database
- Auction: Start $400, Step $100, Blitz $800
- Notes: Transaction includes escrow service availability.
France & United Kingdom
- Date: 01/15/2024
- Industry: Various
- Revenue: France entity over $45 million, UK entity over $500 million
- Technical: Pulse Secure VPNs
- Auction: Start $1,000, Step $200, Blitz $5,000
- Notes: UK access offers admin rights and France with user rights. In the same posting, the threat actor is selling access to a South Korean company’s Pulse Secure VPN with a revenue surpassing a whopping $50 billion, also offered with user rights. The auction is time-constrained, closing 12 hours after the last bid. The threat actor emphasizes that bids should be serious: “Please do not offer if you do not have real buying intentions.”
Germany
- Date: 12/18/2023
- Revenue: Over $155 million
- Technical: RDP access, 1,320 hosts, Sophos antivirus (turned off)
- Auction: Start $1,000, Step $200, Blitz $5,000
- Notes: This auction is time-sensitive, concluding 12 hours after the last bid.
Greece
- Date: 12/17/2023
- Industry: Broadcasting, Media & Internet
- Revenue: $7 million
- Technical: Shell access
- Auction: Start $2,000, Step $500, Blitz $15,000
- Notes: No sale after initial offer; price reduced twice due to lack of interest. The seller shares that this entity receives about 65,200 visitors per day, as per MuStat.com
Hungary
- Date: 12/12/2023
- Industry: Retail (Shop)
- Technical: FTP server access
- Auction: Start $100, Step $50, Blitz $200
- Notes: Full access to the shop’s FTP server. Seller encouraged interested parties with a reputable background to inquire about the domain name. Quick blitz sale within hours of posting.
Italy
- Date: 01/11/2024
- Industry: Energy, Utilities & Waste
- Revenue: $154.3 million
- Technical: Citrix access, over 1000 network computers
- Auction: Start $3,000, Step $1,000, Blitz $6,000
- Notes: The post included two screenshots: one displaying a PowerShell window with a sample list of workstations in the domain, and another showcasing sample folders on the network.
Luxembourg
- Date: 07/09/2022
- Industry: Likely Yachting
- Technical: RDP access, user rights
- Auction: Start $35, Blitz $70
- Notes: Potential buyers were invited to message the seller for a screenshot of the access. Quick sale, with the listing closed the following day.
Netherlands
- Date: 12/23/2023
- Industry: Website Development
- Revenue: $5 – $10 million
- Technical: Root access to servers, FTP, hosting; Plesk with 120 domains
- Auction: Start $1,500, Step $500, Blitz $3,000
- Notes: Threat actor and seller’s name “pmc_vagner”likely refers to the private military company and Russian paramilitary organization the Wagner Group. Access to the Dutch company has not been sold despite a detailed offer.
North Macedonia
- Date: 02/09/2023
- Industry: Federal
- Revenue: $34 million
- Technical: Domain admin access, 271 hosts, Symantec antivirus
- Auction: Start $1,000, Step $500, Blitz $3,000
Norway
- Date: 01/04/2024
- Industry: Marine Shipping & Transportation
- Revenue: Approximately $1.1 billion
- Technical: Citrix access
- Auction: Start $2,000, Step $500, Blitz $5,000
- Notes: Very high-revenue company, auction ends after the last bid or blitz purchase.
Poland
- Date: 09/10/2023
- Industry: Construction Materials and Sanitary Equipment
- Revenue: $200 million
- Technical: Windows Server 2008 R2, ESET antivirus, 3TB HDD, 20+ PCs
- Auction: Start $700, Step $100, Blitz $1,500
- Notes: User domain rights included, with an escrow service for added security.
Portugal
- Date: 01/20/2024
- Industry: Home Furniture
- Technical: Magento (popular open-source e-commerce platform) access, 200,000 customers, 600 weekly orders
- Auction: Start $300, Step $100, Blitz $700
- Notes: The post includes an image displaying various payment methods accepted by the shop, including PayPal, VISA, and Klarna, among others. The listing specifies that there are no admin rights included, and that the buyer “Need to raise exploit” to gain further access
Romania
- Date: 06/16/2023
- Industry: Electrical Equipment and Component Manufacture
- Revenue: Estimated at $35 million
- Technical: “VPN-RDP” access, 43 hosts, ESET antivirus
- Auction: Start $1,000, Step $250, Blitz $2,500
- Notes: The seller, writing in Russian, mentioned their inability to find the Romanian company’s information on ZoomInfo and suggested that anyone with a “днб” (“dnb”) account, likely referring to Dun & Bradstreet (D&B), might be able to access this information.
Slovakia
- Date: 06/07/2023
- Industry: Vehicles
- Revenue: $25 million
- Technical: Microsoft Office365 “admin user” and 120 email accounts
- Auction: Start $100, Step $50, Blitz $1,500
- Notes: The Slovakian company is an authorized service center for various brands including VW, Škoda, SEAT, Jeep, Toyota, Cadillac, Corvette, Camaro, and many others.
Spain
- Date: 12/19/2023
- Industry: Software License Sales
- Technical: RDP “via Tunnel,” Windows Server 2016, Cortex XDR security solution, 162 PCs, 537 users
- Auction: Start $300, Step $100, Blitz $1,000
- Notes: Access includes both “Enterprise Admin” and “Domain Admin” rights.
Turkey
- Date: 07/17/2023
- Industry: Banking & Finance
- Revenue: $31 million
- Technical: “Domain Admins” rights, Symantec antivirus
- Auction: Start $500, Step $100, Blitz $1,000
- Notes: Sale restricted to PM or Jabber for Russian speakers only.
United States
- Date: 01/21/2024
- Industry: Telecommunications
- Revenue: $75 million
- Technical: Enterprise admin access within domain controller
- Auction: Start $3,000, Step $550, Blitz $6,000
- Notes: Just six minutes after the listing was posted, a forum user expressed immediate interest in this high-value access and requested a “Blitz (checking via escrow)” purchase.
Exploit Case Study
Background
Exploit is a Russian-language hacking forum established in the mid-2000s that has gained notoriety in the cybercrime world for enabling the exchange of information and services among a wide range of cybercriminals, from beginners to experts. This forum serves as a marketplace for various illicit digital goods, including botnets, unauthorized system access, stolen credit card details, ransomware, and phishing kits. As of late 01/2024, Exploit boasts a membership of approximately 61,000, with around 1.34 million posts across over 213,000 topics.
Exploit forum’s homepage, screenshot as of 01/2024.
Within the forum’s diverse structure, the “Commerce” section is particularly relevant, where IABs are notably active. These brokers offer unauthorized access to various systems and networks. Not only do IABs sell their access, but they also often make custom requests for access to specific countries or regions. For instance, a post from 11/2023 explicitly seeks network access in France and Germany, stating: “I will buy France and Germany Network Access with any type of privilege. I provide the best offer in the forum. First contact in PM.”
Sellers on Exploit typically adopt a cautious approach, frequently withholding sensitive details to prevent victim identification by researchers or law enforcement. In a 01/2024 post, when a seller was asked about the state and specific location of a U.S. company they were offering access to, they responded: “i can’t provide this information! Protection against researchers Sorry!” Similarly, another seller offering access to a Swedish company with over $500 million in revenue stated: “Because of researchers and police, I’ll keep some details private for serious buyers.” Another seller offering Citrix access to a “HUGE BRAZIL DATA CENTER” quickly replied to an inquiry for more details about the company, saying: “PM for additional info, don’t ask for the site name publicly.”
These are just a few examples of the complexity of the cybercrime ecosystem, as well as the challenges faced by researchers and potential victim entities in identifying and responding to potential security breaches.
Exploit forum’s “Commerce” section, screenshot as of 01/2024.
Findings
We conducted a case study after collecting 438 IAB listings from Exploit between August 2022 and September 2023. While we initially collected data from other hacking forums similar to Exploit, like XSS and Ramp, we noticed significant redundancy in postings across these platforms, with threat actors often replicating their listings to increase the likelihood of a sale. Due to this redundancy and Exploit’s active user base, we concentrated on the Exploit forum alone.
We classified organizations as critical infrastructure following CISA’s taxonomy, which defines 16 sectors so vital that their “incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety.” The data included post date, actor name, victim revenue, industry, auction prices, access type, and level of access. Exclusions were made where geography or industry details were missing. Our research aimed to determine whether there is disproportionate targeting of NATO countries’ critical infrastructure or not, examining IAB posts and prominent threat actors.
Note: Our research was based exclusively on self-claimed compromises of critical infrastructure and forum postings by threat actors, without independently verifying the legitimacy of these listings.
Our analysis indicates a trend of targeted cyber attacks on the critical infrastructure of NATO countries. Through a detailed examination of various recent online listings, we identified 64 that correspond to the critical infrastructure sectors as defined by CISA, accounting for approximately 15% of all listings analyzed. While our findings do not reveal concrete proof of threat actors directly selling access to these infrastructures to hostile nations, the patterns we observed are nonetheless concerning.
IAB listings advertising critical infrastructure access sold for more than double the average IAB listing price. The average blitz price for NATO country infrastructure was $6,396, compared to $2,742 for all listings. Employing the Interquartile Range (IQR) method to eliminate outliers, we found the average selling price for critical infrastructure was still higher: $1,782 versus $1,420 for non-critical infrastructure.
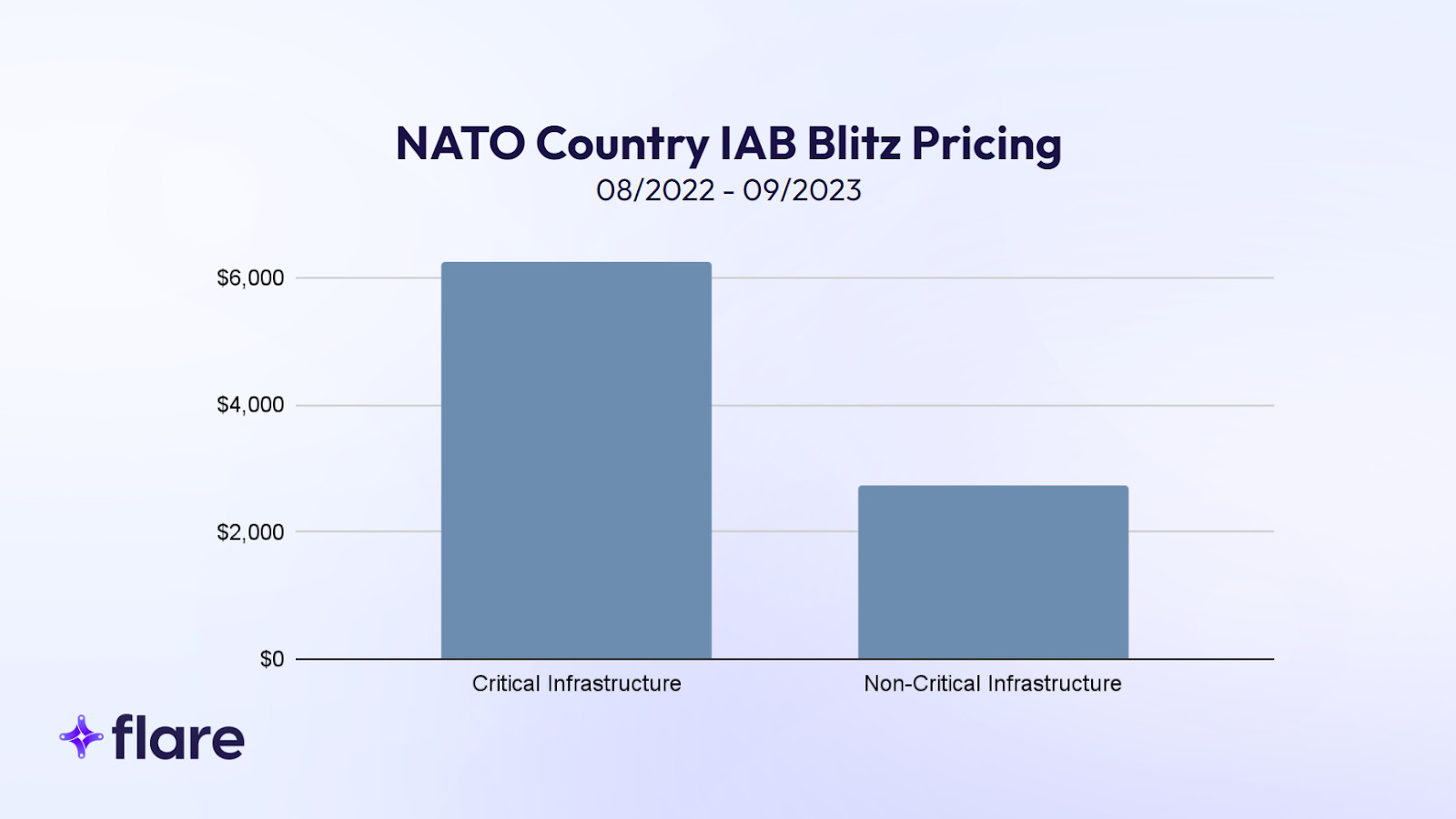
We then analyzed individual threat actors’ focus on critical infrastructure. Of all posts, approximately 15% included NATO critical infrastructure access. Among 108 unique actors, a few showed disproportionate activity. ‘Prolific’ actors, with over 15 posts, had a baseline critical infrastructure targeting rate of 12.4%. Notably, “Roblette” targeted critical infrastructure in 29% of their posts, and “Sandocan” in 25%.
Analysis of our dataset indicates that 35% of all posts targeted victims in the U.S. Both threat actors exceeded this rate: “Roblette” targeted U.S. companies in 57% of posts and NATO countries in 94%, while “Sandocan” targeted U.S. companies in 53% of posts and NATO countries in 71%. The latter percentage rises to 93% if we include NATO-allied countries or “enhanced opportunities” partners like Australia.
The chart above includes another actor we analyzed, Nixploiter, who has dozens of listings to provide an additional point of comparison.
We then focused our analysis on a specific subset of IAB posts which specifically target the U.S. defense sector. Following our review and considering the context of recent high-profile attacks – some of which stemmed from improper password use and hygiene – and the consistent influx of fresh infostealer malware logs that Flare collects and analyzes daily (millions per week), including those containing official government and high-profile government contractor credentials, we assess:
- Certain threat actors deliberately target critical infrastructure and defense sectors. They are motivated by the sectors’ significant roles in national security, which can command higher prices in terms of revenue for the threat actors.
- Conversely, other incidents appear to be incidental, arising from widespread phishing and social engineering campaigns and enabled by tactics like credential stuffing or password spraying.
In our review of hundreds of posts, listings, and discussions on Exploit, pertaining to defense contractors and companies, we came across numerous instances where IABs and forum users were explicitly targeting the defense sector, as evidenced by their postings. We also saw posts that highlighted the value of accessing companies with government connections, as per threat actors’ vocabulary when describing fresh access and sales with great enthusiasm. Notable findings from analyzing this subset of IAB data include:
- Access to U.S. defense contractors is priced at an average of $5,750 for immediate purchase, in stark contrast to an average of $1,489 for all other industries (after removing outliers). This disparity suggests that threat actors are willing to pay a premium for potential access to highly sensitive environments.
- Offers of privileged IT access to American IT management companies with federal contracts were observed, raising concerns about the potential for a wider-scale impact and the possibility of expanded cyber supply chain attacks.
- Threat actors frequently and explicitly promote access to U.S. government digital assets, suggesting they recognize the value of accessing high-level privileged information.
Conclusion
IABs target a diverse range of entities, including those belonging to critical infrastructure sectors in NATO member states. No organization is immune to the threat of infiltration, and so in light of this pervasive threat, we recommend the following:
- Actively monitor forums that enable IABs: It is crucial for organizations to actively monitor forums such as Exploit to detect potential compromises. Given the anonymized nature of IAB postings and cautiousness of sellers, it is often difficult to determine an exact victim. However, since threat actors often use publicly available services like ZoomInfo for victim description, analyzing differences in postings – such as geography, revenue, industry, and especially technical details like number of hosts, sample usernames, antivirus solutions, etc. – can provide insights into potential compromises within their environments. This proactive approach facilitates early detection, allowing organizations to address existing breaches before they escalate into ransomware or other undesirable malicious activities.
- Actively monitor stealer logs: Leaked credentials and cookies from stealer logs can be a common vector for IABs to gain initial access. Organizations should implement automated systems to monitor fresh logs, which often contain information like RDP and VPN credentials, as well as local network IP credentials that can assist in internal post-compromise pivoting. It is crucial to act immediately upon detecting these leaked credentials and infected devices – before an IAB potentially does. This detection should extend across both public and private channels on Telegram and include premium paid logs from surface and dark web marketplaces, such as “Russian Market.”
- General security: Organizations should continuously assess and update their security measures. This includes regular vulnerability scanning, patch management, and the implementation of multi-factor authentication to strengthen their security posture. Additionally, training employees to recognize and respond to cyber threats is essential in reducing the risk of successful phishing attacks and other social engineering tactics frequently used by IABs.
About Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and illicit Telegram channels 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools.
Want to learn more about monitoring for relevant threats with Flare?


