by Tammy Harper (CYPFER) & Eric Clay (Flare)
Background
An out-of-place data leak appears.
The dark web is no stranger to drama. Threat groups often collude, fight, and attempt to expose each other. This past week witnessed a notable example of such conflict, involving a confrontation between the LockBit ransomware group and a threat actor known as KonstLiv3. This strife led to an explosion of drama across the Russian-language dark web cybercrime forums XSS and RAMP. But what caused this dissension?
There are few rules that Russian threat actors are expected to follow. However, one crucial, non-negotiable, and immutable rule is that threat actors must never target entities belonging to Russia or any country in the Commonwealth of Independent States (CIS). These countries include, in addition to the Russian Federation, Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, and Uzbekistan.
So, what happens when a threat actor disregards this rule? What happens if a threat actor attempts to sell a massive data dump from a significant multinational Russian company, which has ties to the Russian government and Russian intelligence services?
Last week provided a compelling example of this.
AN Security[.]ru Allegedly Breached
The saga began when KonstLiv3 posted on the invite-only dark web forum RAMP, claiming to have breached a multinational Russian physical and cybersecurity firm, AN-Security[.]ru (hereinafter referred to as “AN Security”). The threat actor alleged they had accessed a substantial trove of data and were trying to sell it for a staggering 100 BTC, approximately $4.3 million USD at the time of writing. Within hours, fellow RAMP users were calling for KonstLiv3’s ban. The RAMP moderators responded to these demands, resulting in KonstLiv3’s ban within nine hours.
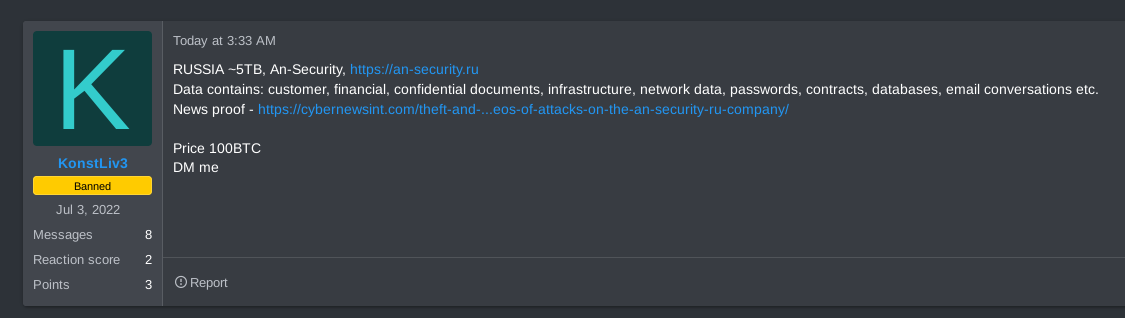
KonstLiv3’s claim of breaching Russian security services company AN Security. Monday, Jan 22, 2024, 3:33AM
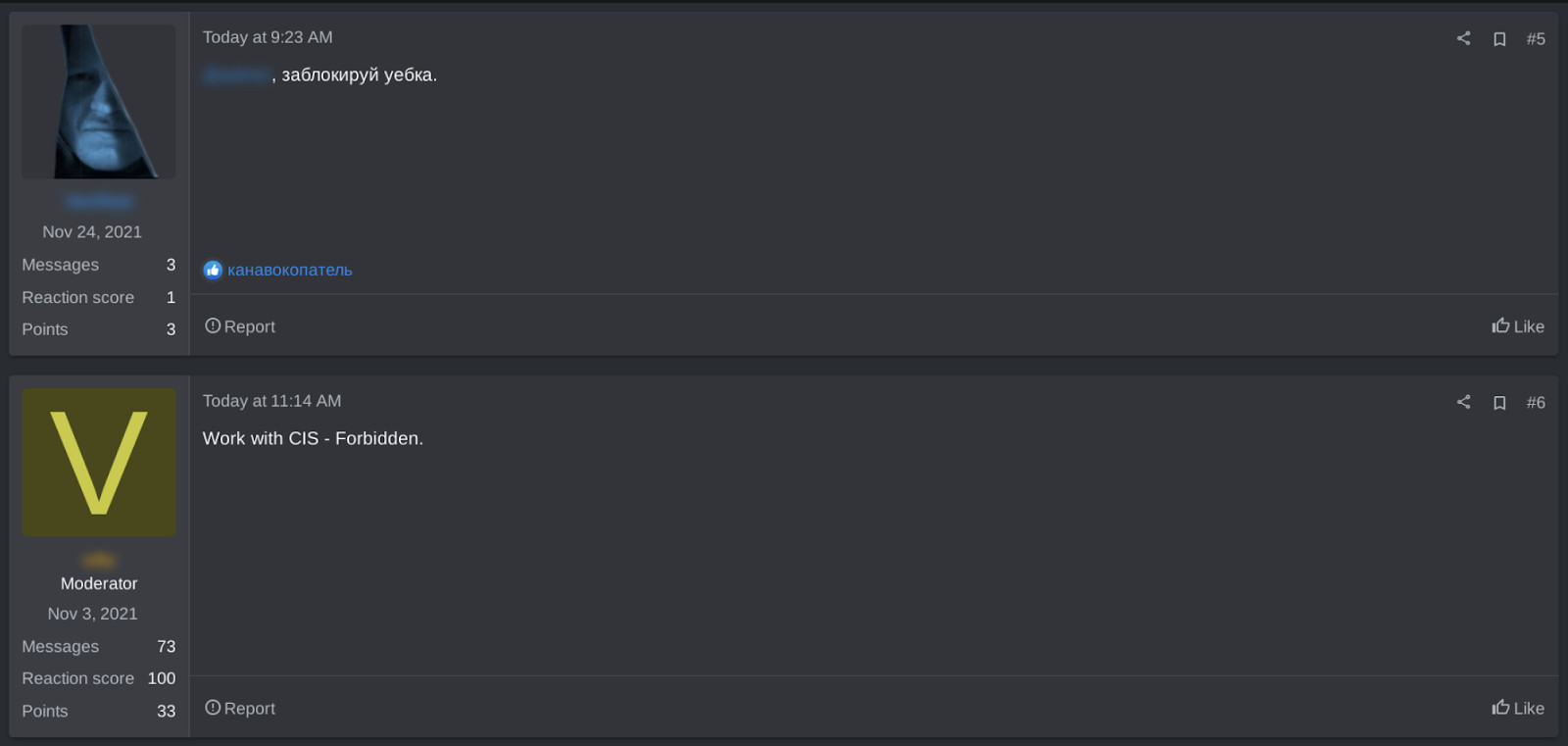
A RAMP user, writing in Russian, demands KonstLiv3’s ban. A RAMP moderator then acknowledges that “work,” a euphemism for malicious activity, is “Forbidden” against CIS countries, before proceeding to ban KonstLiv3. Monday, Jan 22, 2024, 9:23AM, 11:14AM
LockBit Enters the Chat
Hours later, LockBitSupp, the primary public-facing account operating the LockBit ransomware-as-a-service (RaaS) platform, expressed significant concern on the prominent Russian-language forum XSS. They feared being framed for the attack on AN Security. The perpetrator of the attack had allegedly utilized a leaked version of LockBit 3.0, also known as “LockBit Black,” a more modular and evasive variant of LockBit’s previous ransomware.
LockBitSupp claimed to have reached out directly to an employee at AN Security, who supplied them with the ransom note allegedly left with the organization, which directly implicated LockBit in the attack. For LockBit, this was alarming news. Much of the threat cyber intelligence community believes that LockBit operates primarily out of the Russian Federation. However, a major breach had just occurred at an entity directly associated with the Russian state, allegedly by a LockBit affiliate.
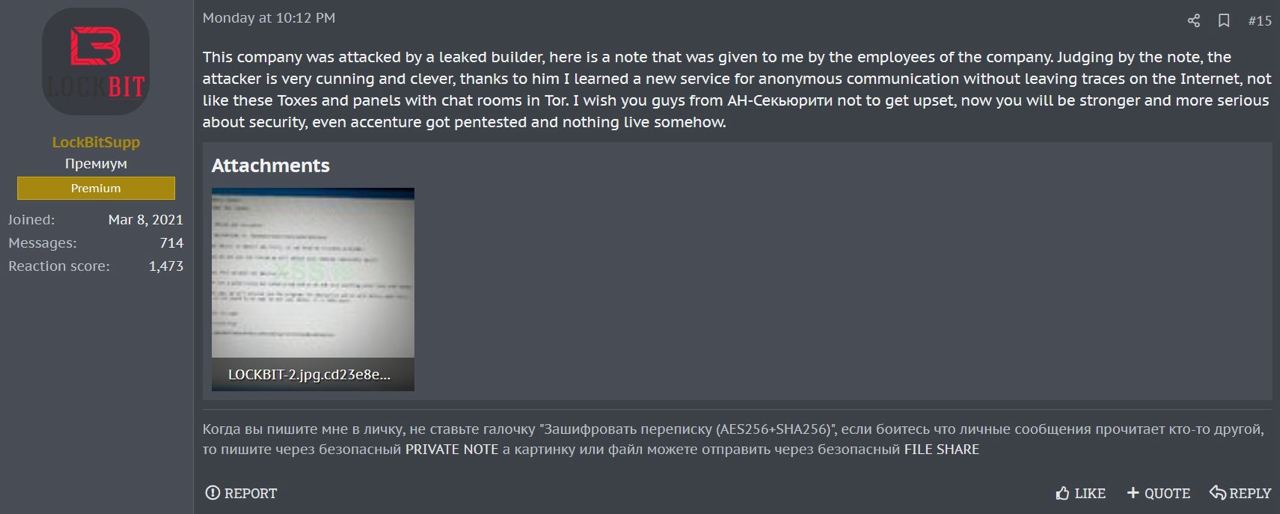
LockBitSupp’s response on XSS to the insinuation that LockBit was involved in the AN Security breach. Monday, Jan 22, 2024, 9:10:12PM
Shortly after LockBitSupp’s post, XSS user alex778 commented, describing AN Security as: “a very fat and very old St. Petersburg PSC [private security company] from the dashing 90s. Whether it is so fat that citizen LockBit will now be poisoned with polonium… It definitely looks like a setup.” A few hours later, LockBitSupp returned to XSS with an update. They alleged that the user Signature was behind the setup.
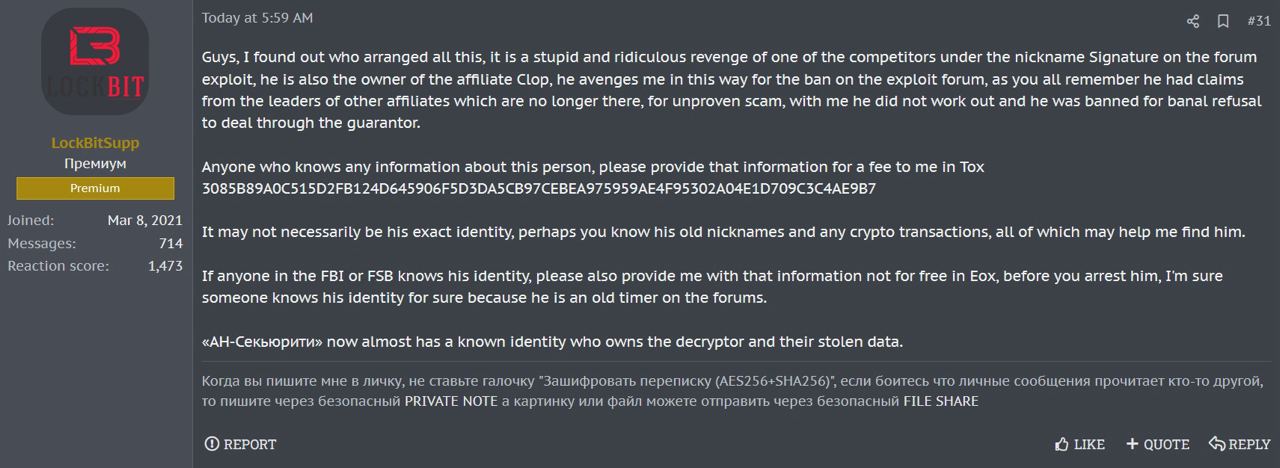
LockBitSupp, the primary public-facing account of LockBit, accuses CL0P of orchestrating the attack and framing them. Tuesday, Jan 23, 2024, 5:59AM
Signature was a user on Exploit, another infamous Russian-language forum specializing in initial access, and the sale of exploits and malware. LockBitSupp made some astounding allegations. Firstly, LockBit claimed that Signature was the owner of the CL0P ransomware gang. CL0P, a notorious group with connections to FIN7, also known as the Carbanak Group, gained significant prominence last year after exploiting the MOVEit (CVE-2023-34362) and GoAnywhere (CVE-2023-0669) vulnerabilities, targeting hundreds of organizations worldwide and resulting in over $100 million in ransom demands.
LockBitSupp and Signature had a history on Exploit. They attempted a few deals, but these fell through when Signature refused to use the main escrow on Exploit, leading to a ban from the forum. This allegedly angered Signature, leading them to use a leaked build of the LockBit Black builder to attack AN Security. Signature allegedly encrypted their network, exfiltrated over 5TB of data, and offered it for sale on XSS, RAMP, and BreachForums. In response, LockBitSupp placed a bounty on the XSS forum for any information leading to the personal identification of Signature. Over the next few days, the forum buzzed with activity as users tracked down potential usernames and TOX IDs.
The well-connected actor Bratva posted a thoroughly compiled list of users potentially connected to Signature.
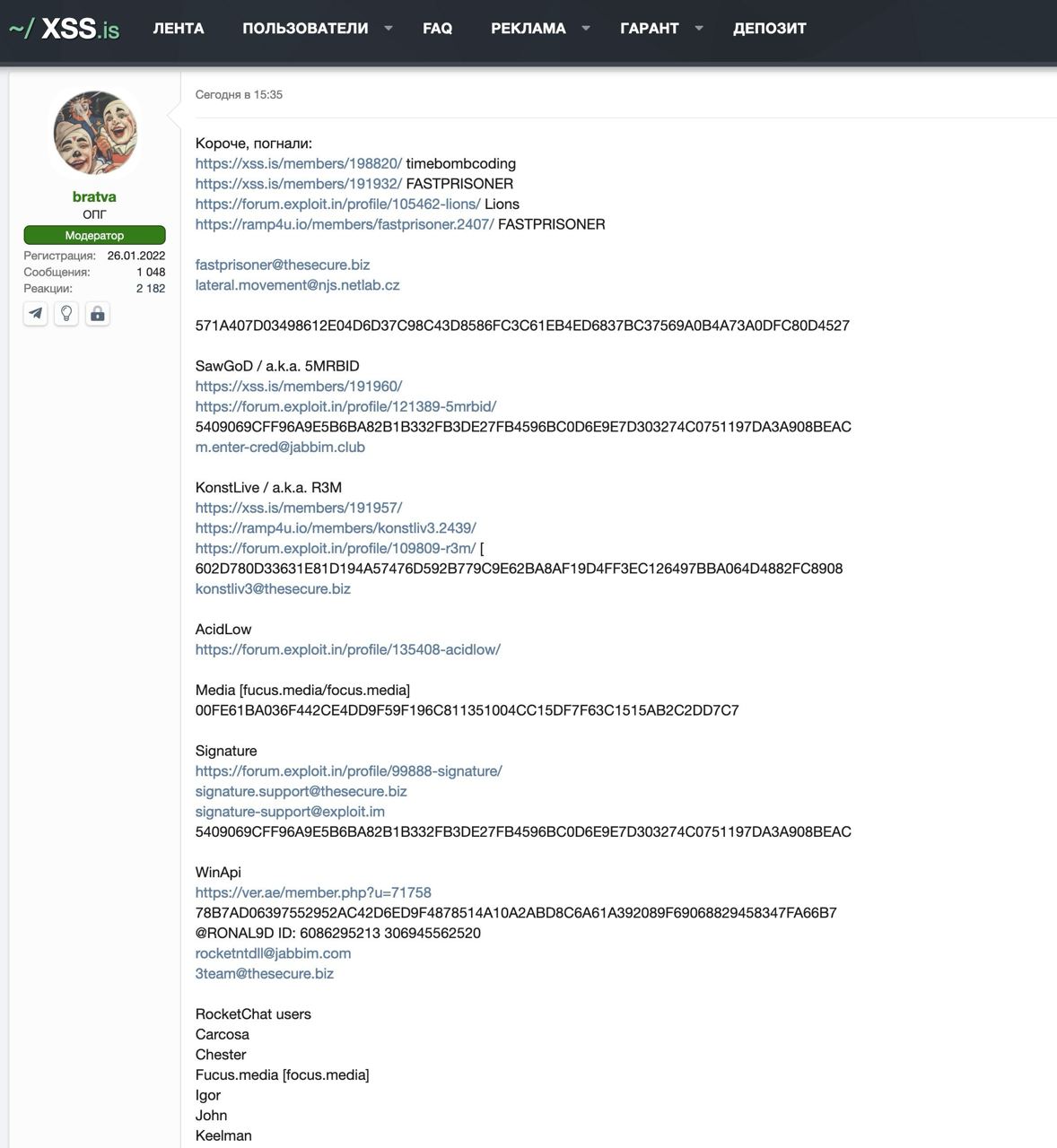
Bratva (a term for Russian mafia) posts usernames they believe are associated with Signature.
Another user, lisa99, presented an analysis of the news site used to verify the breach’s authenticity. The domain cybernewsint[.]com was registered on December 17th, 2023, just a few weeks before the initial data leak posts began to surface online.
The earliest news article on cybernewsint.com is dated January 9th, 2024. Lisa99 also pointed out that the website is linked to vk[.]com/dailyhackernews and the admin vk[.]com/sozdam_sayt. This admin is identified as: “a certain redacted,” whose profile mentions: “I make websites [for] order,” before lisa99 concludes that: “Apparently this site was ordered for him too.”

Lisa99 posts on BreachForums, sharing the results of their initial investigation into the news site.
LockBit Increases the Bounty
LockBitSupp, frequently boasting about their OPSEC and ability to elude international justice, has taken a unique approach to deter detection and personal identification. They have established a bounty on their own identity, offering $1 million USD in cryptocurrency to anyone who can provide their full name and explain the method used to uncover it. In a notable move, LockBitSupp has now raised this bounty from $1 million USD to $10 million USD. This substantial increase either signifies growing concerns over their own anonymity, or is simply a technique to establish and prove ‘innocence.’
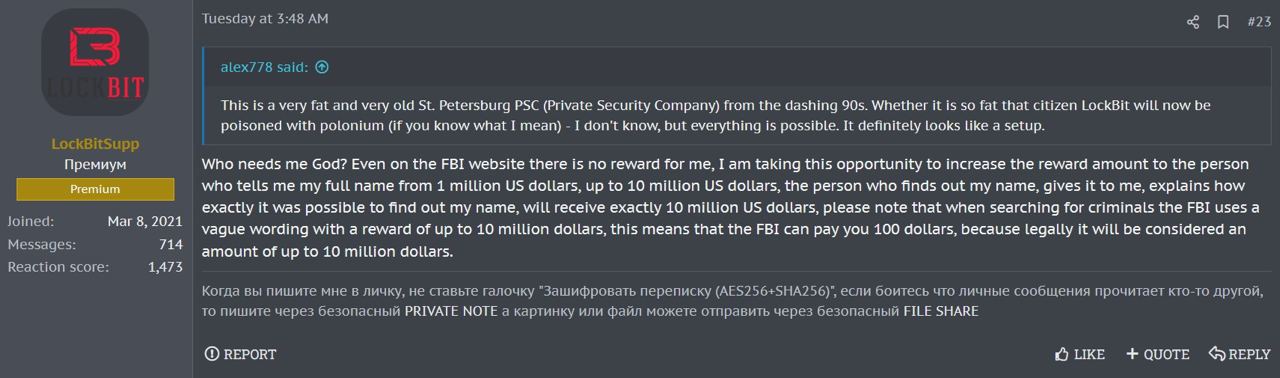
LockBitSupp announces an increase in the bounty on their own identity in a post on XSS.
This tenfold increase in their self-imposed bounty might also serve to reassure affiliates and core members of the LockBit group, especially in light of the extra scrutiny brought about by this alleged breach. LockBitSupp has a history of making similar offers, including incentives for getting LockBit tattoos, rewards for finding vulnerabilities on the LockBit site, and other bounties related to their identity.
Breakdown and Analysis
With the basic facts laid out, several aspects of this episode merit further exploration. A primary question arises: Did Signature, allegedly the leader of CL0P, attempt to weaponize the Russian state against a competing ransomware group? Furthermore, what does this incident reveal about the broader cybercrime ecosystem?
Inconsistencies Abound
This conflict is riddled with oddities. Firstly, it’s peculiar that an actor, active on top-tier dark web forums since at least 2022, would deliberately target and publicize data from a Russian state-affiliated entity. Such a move is highly unusual and almost inconceivable. Signature would surely be aware that targeting CIS country organizations is strictly forbidden, and it is improbable to find a buyer under these circumstances.
A Fake News Site?
Another bizarre element is the possible creation of a fake cyber news site, still operational at the time of this writing, seemingly to legitimize an attack that occurred. If the attack was fabricated, did LockBitSupp post a fake ransomware note from the affected AN Security? Additionally, one would expect any party ready to make a massive $4.3 million payment to verify the news site’s authenticity.
Data Size Inconsistency Across Forums
KonstLiv3’s actions and timeline also raise questions. Initially, they listed the data exclusively on the RAMP forum and were banned hours later. He then moved to XSS, followed by the English-language BreachForums. There are two notable points:
- The exorbitant asking price, in a market where data dumps typically sell for $5,000-$100,000, suggests the posts might have been more about publicizing the breach of a major Russian company than actually selling the data.
- KonstLiv3’s post on BreachForums was nearly identical to their RAMP forum post, except – the data size dropped by 1TB, while the price remained at 100 BTC. One possibility is that part of the dataset was sold, or that AN Security (or another entity) paid to prevent the publication of the most sensitive data. It is likely that the sloppy user could have simply forgotten to align the data size across forums.
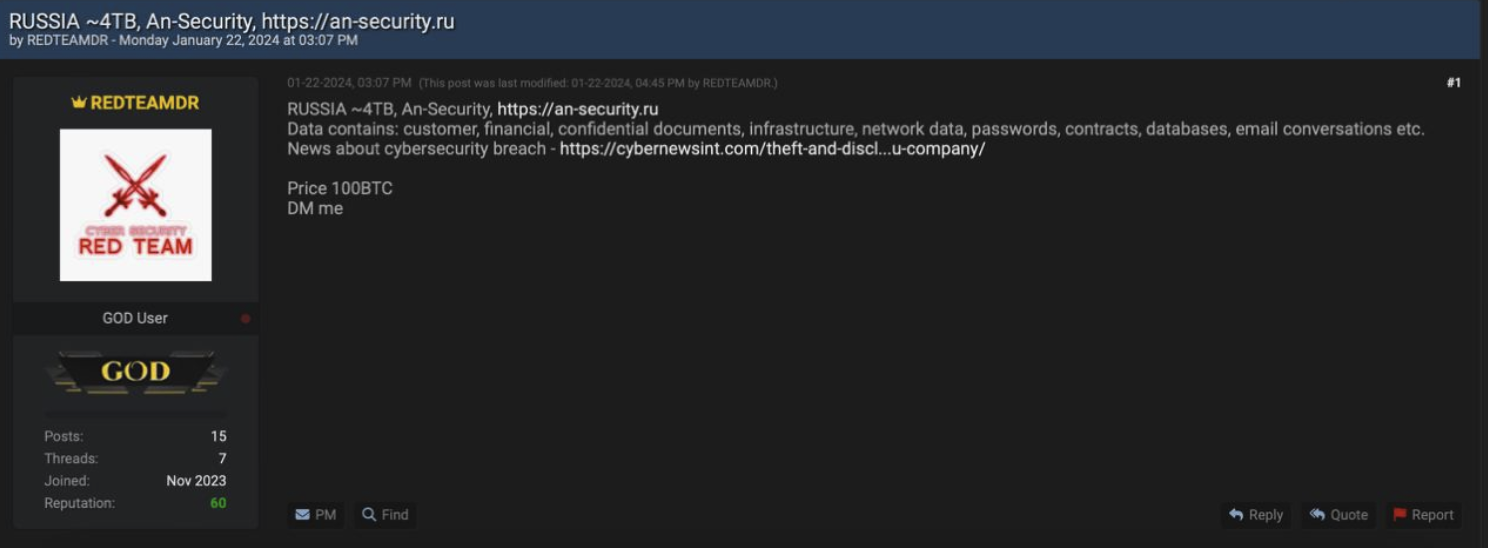
The final post on BreachForums advertises access to AN Security, with the sale price unchanged but a noticeable 1TB decrease in the claimed data size (originally “~5TB” on other forums)
The Russian State and Cybercrime
A key takeaway from this event is the importance that the illicit cybercrime community places on the rule against targeting entities in CIS countries. Breaking this rule jeopardizes all involved parties. Forum admins are responsible for the community’s welfare, and users attracting undue attention can endanger the forum’s security.
Ransomware groups operate within a fine line of tolerance. Attacking highly sensitive targets in NATO countries risks drawing national government and law enforcement attention, as seen in the Colonial Pipeline 2021 attack. Targeting organizations within CIS countries is strictly forbidden, and the ability of Russian authorities to press charges against cybercriminals in Russia is significantly stronger than that of Western countries.
Even in the cybercrime underground, content moderation is crucial.
Image Credits
https://twitter.com/3xp0rtblog/status/1750469704773161244
https://twitter.com/azalsecurity/status/1749637667577356335
https://twitter.com/3xp0rtblog/status/1750521829847187797
https://twitter.com/azalsecurity/status/1749637667577356335/photo/3
https://twitter.com/ddd1ms/status/1750560454932385848
https://twitter.com/azalsecurity/status/1750565920806727973/photo/1

