
Initial access brokers (IABs) gain unauthorized access to the system then sell this access to other malicious actors. Based on a large sample of IAB posts on the Russian-language hacking forum Exploit.in (Exploit), IABs increasingly target entities within NATO member states, with research revealing recent activity in 21 of 31 countries. Additionally, access to organizations within industries classified as “critical infrastructure” commanding higher prices. Based on the basic concept of supply-demand pricing models, these postings indicate that threat actors may be targeting these industries, especially given the clear trend around cyberattacks targeting the U.S. defense sector.
As organizations seek to mitigate their risks, understanding cybercriminal networks and monitoring them becomes increasingly important.
To learn more, check out the full report, Initial Access Broker Landscape in NATO Member States on Exploit Forum, or keep on reading for the highlights.
Exploit: Insight into a Cybercrime IAB Forum
Understanding how attacks work means understanding how the cybercrime world functions. With visibility into cybercriminal forums, organizations can better understand the threats they face and implement appropriate proactive security controls more effectively.
The typical IAB post includes the following information:
- Access Type: Usually RDP or VPN.
- Activity: Victim company’s industry.
- Revenue: Often sourced from data providers and services such as ZoomInfo.
- Level / Rights: Level of privileges obtained.
- Host / Network: Details about the victim’s network and security systems.
- Start, Step, and Blitz: Auction prices detailing the starting, bid increments, and ‘buy it now’ prices, respectively.
A small sample of recent IAB sales from 2023 and 2024 involving entities in 21 of 31 NATO countries provide insight into the various industries and access offered. A few highlights include:
- A Belgian company in the Commercial and Residential Construction industry providing access that allows users to explore the network, including backup folders, with the action starting at $500, stepping at $50, and blitzing at $600
- A Canadian company in the Legal industry providing all user hashes offering potential for extensive unauthorized access within the firm’s network with the auction starting at $300, stepping at $100, and blitzing at $1000
- An Italian company in the Energy, Utilities, & Waste industry providing screenshots showing workstations and folders on the network with the auction starting at $3000, stepping at $1000, and blitzing at $6000
- A Polish company in the Construction Materials and Sanitary Equipment industry providing user domain rights and an escrow services for added security with auction starting at $700, stepping at $100, and blitzing at $1500
- A US company in the Telecommunications industry providing enterprise admin access within a domain controller starting at $300, stepping at $550, and blitzing at $6000
Across the sales, listings offer insight into different security tools that the buyers can either compromise or evade, including:
- Kaspersky Lab antivirus
- Pulse Secure VPN
- Symantec antivirus
- ESET antivirus
- Cortex XDR
The Exploit Forum: A Deep Dive
Established in the mid-2000s, Exploit is a well-known Russian-language hacking forum that beginner and experienced cybercriminals use for exchanging information and services. Historically, the forum serves as a marketplace for various illicit digital goods, including:
- botnets
- unauthorized system access
- stolen credit card details
- ransomware
- phishing kits
IABs are typically active in the “Commerce” section, selling access and making custom requests for access to specific countries or regions. Recognizing that security researchers and law enforcement may be monitoring the forum, sellers often withhold location and company details.
The Why and What
438 IAB listings collected from Exploit between August 2022 and September 2023 were significantly similar to those posted on other hacking forums as cybercriminals often cross-post their listing to increase the likelihood of selling their goods. Since Exploit has an active user base, it offers robust data for a meaningful use case.
The research focused on organizations that qualify as critical infrastructure based on the Cybersecurity & Infrastructure Security Agency (CISA) definition. The analyzed data included:
- post date,
- actor name,
- victim revenue,
- industry,
- auction prices,
- access type,
- level of access
By examining IAB posts and prominent threat actors, the research aimed to answer the question: Are attackers disproportionately targeting NATO countries’ critical infrastructure?
Key Findings
Although approximately 15% of all listings mentioned organizations within critical infrastructure sectors, the pricing models show a trend that indicates targeted cyber attacks against them.
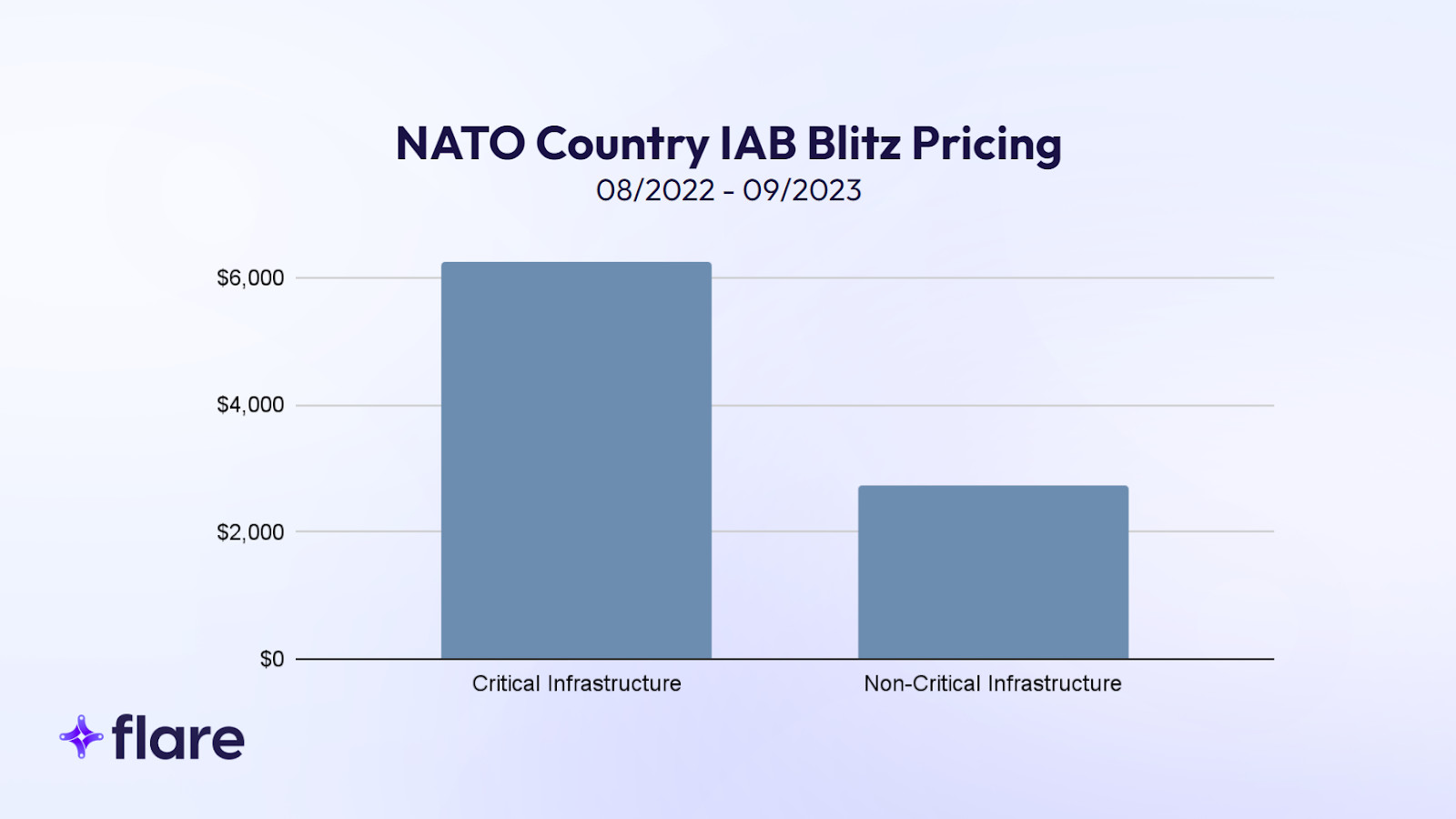
The disproportionately higher “buy now” prices appear to mean cybercriminals can request more money for critical infrastructure data, indicating that the demand is higher.
An analysis of individual threat actors focusing on critical infrastructure found 108 unique actors with higher levels of activity. Of these posts, two threat actors appeared to specifically target critical infrastructure:
- Roblette: 29% of their posts targeted critical infrastructure, with 57% of them focused on US companies and 94% of them focused on NATO countries
- Sandocan: 25% of their posts targeted critical infrastructure, with with 53% of them focused on US companies and 71% of them focused on NATO countries while including NATO-allied countries like Australia increased that percentage to 93%
The U.S. Defense Sector
As several recent high-profile attacks targeted the U.S. defense sector, the research aimed to answer two questions:
- Are financially motivated threat actors targeting these organizations because they can command higher prices due to the role the sectors play in national security?
- Are these incidents a byproduct of widespread phishing and social engineering campaigns?
Across hundreds of Exploit posts, listings, and discussions, IABs and forum users regularly mentioned specifically targeting the defense sector and highlighted the value of accessing companies that have government connections. Some notable finding include:
- U.S. defense contractor access commanding an blitz price of $5750 compared to $1489 across other sectors
- Offers that included privileged access to U.S. IT management companies with federal contracts
- Frequent and explicitly promotion of access to U.S. government digital assets
Risk Mitigation Strategies
While IABs currently appear to target critical infrastructure across NATO member states, no organization is immune to these pervasive threats. To mitigate risk, organizations should:
- Actively Monitor Forums that Enable IABs: While anonymized posts make identifying a target victim difficult, organizations can gain insights by reviewing post information like geography, revenue, industry, and especially technical details like number of hosts, sample usernames, and antivirus solutions. With early detection, organizations can proactively address existing breaches before threat actors leverage them as part of ransomware attacks or other malicious activities.
- Actively Monitor Stealer Logs: IABs typically gain initial access using leaked credentials and cookies from stealer logs which can contain information like RDP, VPN, and local network IP credentials. By detecting leaks in the dark web and illicit Telegram channels, organizations can act upon these leaked credentials and infected devices before IABs do.
- General Security: Organizations should continuously assess and update their security measures by implementing and maintaining vulnerability scanning, patch management processes, multi-factor authentication, and employee awareness training.
Monitoring Dark Web Forums with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and illicit Telegram channels 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.


