This article was updated on December 11th, 2025.
Infostealer malware is one of the defining trends of the 2020s. Threat actors have long leveraged leaked credentials to take over enterprise and consumer attacks, but infostealer malware provides a new and incredibly easy vector for them to exploit. Infostealer variants such as Lumma, Redline, Raccoon, Vidar and others infect computers and exfiltrate all of the credentials and session cookies saved in the browser, in addition to Discord tokens, VPN credentials, and cryptocurrency wallet data. A single stealer log contains all of the data from one victim.
Keep reading to explore what security teams would benefit from knowing about stealer logs, so they
Explore an interactive stealer log below:
Infostealer Log Structure
EDUCATIONALClick folders to expand, files to view contents. All data is fictional.
The evolution of the infostealer ecosystem has precipitated a dramatic increase in credential based attacks. Threat actors almost always follow the path of least resistance when attempting to compromise consumer or enterprise accounts, and the mass availability of direct access credentials and session cookies makes it far easier than before to simply log-in to applications.
Infostealer logs represent one of the primary threat vectors for enterprise companies today. A single stealer log can compromise many corporate credentials and provide threat actors with a seamless way to directly directly log-in to enterprise accounts, and session cookies can be used to bypass two-factor authentication.
Is Your Organization Exposed?
More than 60% of companies with over 1,000 employees have at least one critical infostealer exposure. Flare monitors millions of stealer logs daily so you can find compromised credentials before attackers do.
Infostealer Malware as a Service
The Infostealer malware ecosystem begins with specialized vendors known as Malware as a Service (MaaS) vendors who sell licenses to infostealer variants for a monthly (and in some cases) lifetime subscription fee. These transactions are typically carried out on Telegram channels using the anonymous cryptocurrency Monero.
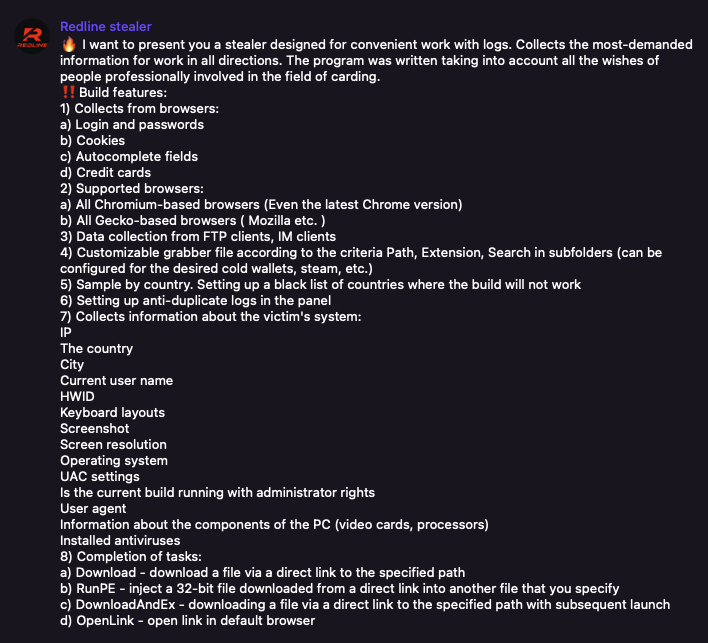
Notice that in this case the Redline Stealer account heavily advertises specific feature and data collected by the infostealer. The malware as a service ecosystem displays many of the dynamics of a competitive market economy, complete with cut throat competition, price wars, and advertising.
Infostealer Infection Campaigns
After a threat actor purchases a license to infostealer malware, they need to set up a system to mass infect their victims. There are many ways that threat actors can accomplish this. At Flare we’ve seen dozens of examples of campaigns ranging from custom infrastructure that the threat actor sets up to impersonate specific brands to simply taking over YouTube accounts and posting a video for free cracked software, then posting a link to fire sharing infrastructure to send unsuspecting victims to download the malware.
Example: The Midjourney Infostealer Campaign
Most infostealer campaigns are not very complex, but some involve significant investments of time and effort from threat actors. One poignant and sophisticated example of infostealer distribution came in 2023, where threat actors set up a sophisticated campaign to impersonate the AI platform Midjourney in order to achieve mass infections.
This campaign involved multiple steps, first they set up website imitating Midjourney’s image generation software:
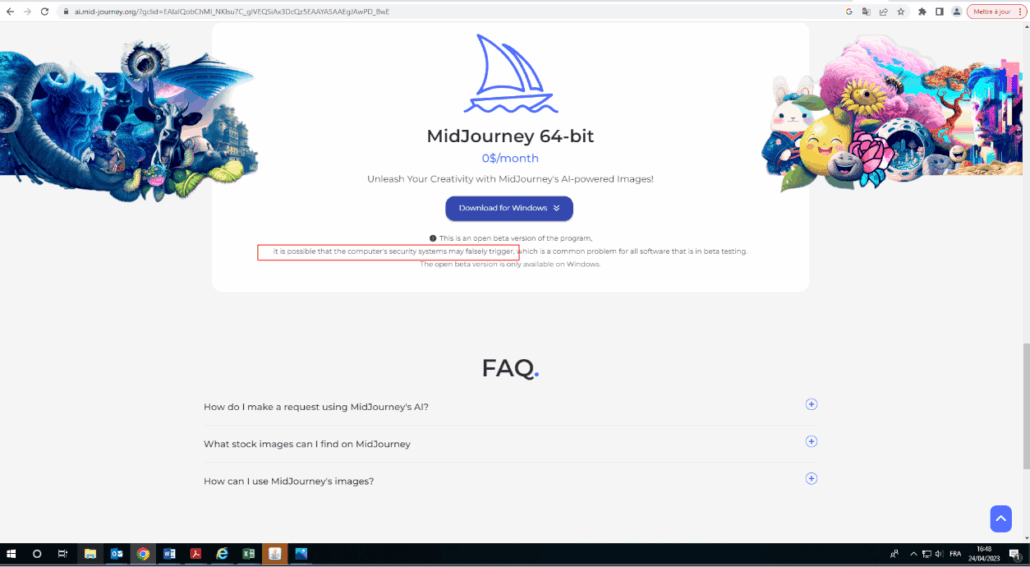
Notice that the page advertises Midjourney for free and that the domain is ai.mid-journey.org rather than the actual midjourney website which can be found at midjourney.com.
Next the threat actors either set up or took over various Google ads accounts to ensure that the result appeared at the top of the page when users searched for midjourney. It is difficult to estimate, but this campaign led to tens of thousands of infections over a multi month period at a minimum.
In many cases threat actors will even use popular messaging applications such as Discord and Telegram as C2 infrastructure, leveraging API’s to send logs directly back from victims to the platforms which dramatically simplifies the infrastructure requirements while also
Stealer Log Distribution
The threat actors that launch infection campaigns are often (but not always) different than the ones that actively leverage the logs. As it turns out, threat actors can employ economics principles as well, and it is far more profitable for a threat actor to focus on one leg of the supply chain (such as exploiting access to logs) than it is to design malware, run distribution, and then actively exploit credentials.
Stealer Log Distribution on Telegram
Cybercriminals typically monetize harvested stealer logs in one of two primary ways. First and most commonly they run a private/public Telegram channel combo. Fresh logs are posted to the private Telegram channel and older logs are posted to the public Telegram channel which serves as an advertisement for the private one. Threat actors will limit the number of “seats” in the private channel to a maximum of 10-25 and charge several hundred per month for “membership”. The public channel serves as an advertisement in much the same way as a free sample at a grocery store does.
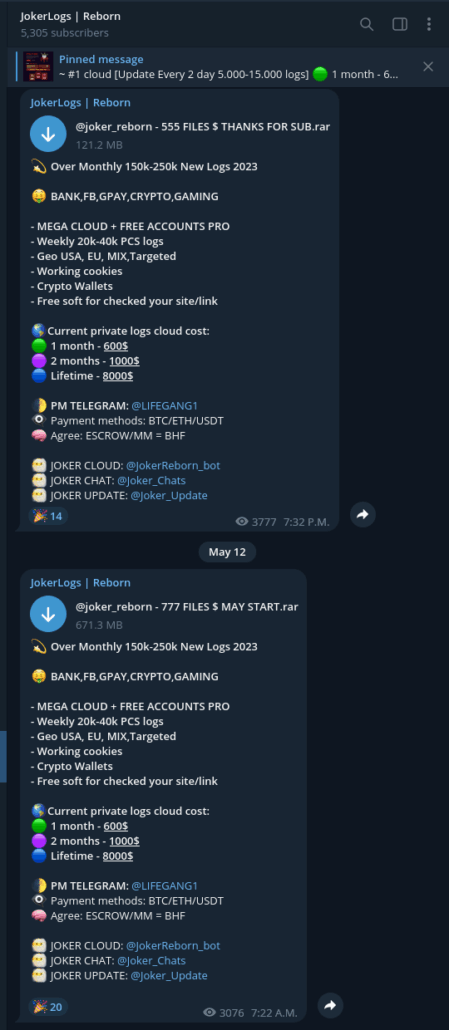
Example of a private Telegram channel advertisement, it is probably a poor idea to purchase a “lifetime license” from cybercriminals
Stealer Log Distribution on Russian Market
Russian Market is a dark web autoshop focused on selling stealer logs. Unlike Telegram channels in which threat actors download bulk files of stealer logs, Russian Market allows them to search for specific domains within the log they are looking for. Each log is sold one time for $10 regardless of the contents of the log.
Stealer Log Log Exploitation
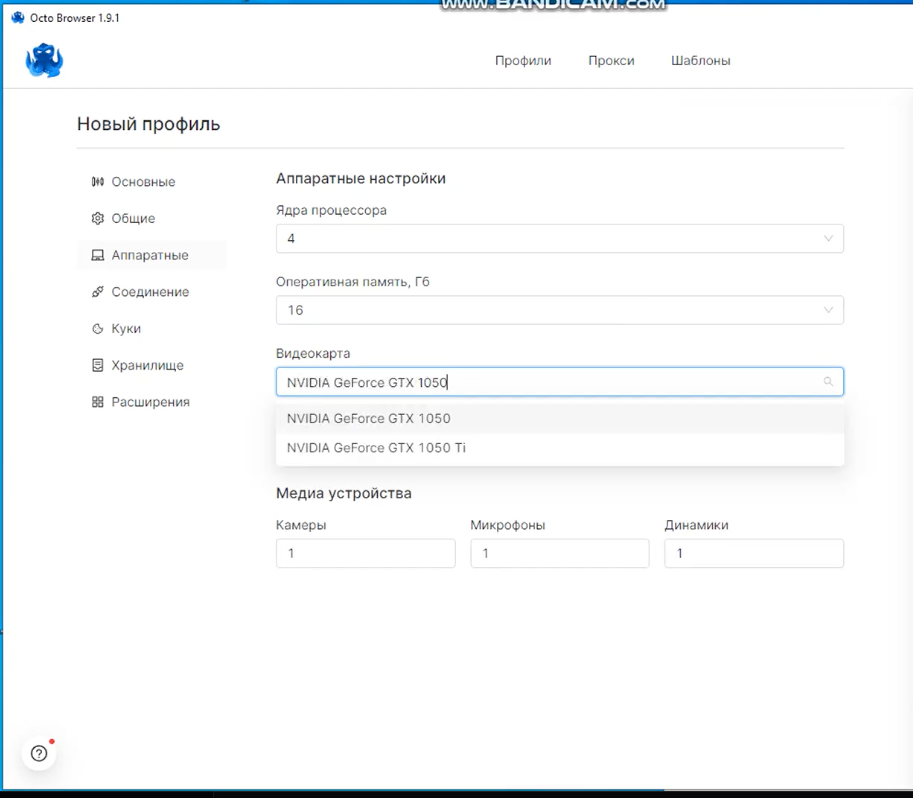
Anti-detect browser that enables the user to replay session cookies while also mimicking key details from the victim’s computer to bypass anti-fraud mechanisms
Before we dive into a specific example, let’s begin by discussing exactly what criminals are doing with infostealer logs in broad strokes. Web applications don’t just rely on session cookies and credentials in order to successfully authenticate users. In some cases they will also look at the “fingerprint” of the browser to identify key details about the user that can be used for additional validation. The combination of infostealer malware, anti-detect browsers, and checkers represent a multi-pronged approach to defeating these controls.
Threat actors use anti-detect browsers to impersonate the user’s browser fingerprint based on details found in the stealer log to successfully replay the session cookies and facilitate an account takeover attack. Once in, the actor changes key profile information such as email, password, and two-factor authentication (2FA) to authentication mechanisms that they control. So what do threat actors do then? Well it depends, different actors specialize in taking over different types of accounts. Some common methodologies include:
1. Exploit the stolen information for personal gain, such as using stolen credit card details.
According to Flare research, stealer logs with financial data such as bank logins and credit cards sell for an average of $112 on Genesis Market, compared to the average of about $15 across all logs for sale. Threat actors highly value financial accounts, as they can steal directly from consumers.
2. Gain unauthorized access to other systems.
Bad actors like TRIPLESTRENGTH leverage infostealer logs as a source for stolen credentials and cookies. The group hijacks clouds for cryptocurrency mining operations and other threat activity.
3. Sell the information to other criminals.
Threat actors profit off of or build up their reputation by distributing these stealer logs. They may open a public Telegram channel with a free “sample” of a stealer log and then grant access to private channels with fresher logs for $200-$500 per month.
In another example, threat actors could sell to initial access brokers who buy hundreds of thousands of stealer logs to identify which credentials could serve as the initial access into corporate IT environments.
Initial access brokers target stealer logs with access to CRMs, RDP, VPNs, cloud hosting platforms, SaaS application access, and other corporate devices. They can exploit the credentials gain initial access to enterprise systems, then resell that access in an auction style format on cybercrime forums such as XSS and Exploit.
Stealer Log Exploitation Case Study: Bank Account Takeover Attack
Infostealer Screenshot, Sep 5, 2024, BLTools Campaign. Note that presence of the“Bypass KYC New working Updated” file saved on the host
Infection Date: September 5, 2024
Possibly Relevant Tools: Telegram, BLTools
Location: Nigeria
VM/Proxy: No
Next we are going to look at a real life criminal who themselves got infected with an infostealer, leading to their credentials and browser history being compromised. This provides an excellent vignette to see just how threat actors leverage logs for criminal gain.
This user is a perfect example of how an average threat actor exploits stealer logs. They have been infected by downloading BLTools (almost certainly based on campaign details), and even a cursory glance at their profile reveals that their motive is direct access to financial services accounts. Based on the IP address and other data on the computer, we can place the user in Nigeria. The following URLs had saved credentials in their browser:
- coinbase (crypto exchange)
- oi.huidclaims.ui.hawaii.gov (government claims site)
- 53.com (banking)
- patriotsoftware (business payroll)
- found.com (small business banking)
Interestingly, if we look more closely at the browser history, we can see that they seem to have had some success. In fact, their browser history contained a real example of the actor taking over a consumer Bank of America account through session hijacking. Reviewing the criminals browser history we can see:
https://secure.bankofamerica.com/login/sign-in
https://secure.bankofamerica.com/login/sign-in
https://secure.bankofamerica.com/login/sign-in/signOnSuccessRedirect
https://secure.bankofamerica.com/myaccounts/signin/signIn
https://secure.bankofamerica.com/myaccounts/brain/redirect
https://secure.bankofamerica.com/myaccounts/accounts-transfer
https://transfers.bankofamerica.com/jsp/bofa/account_add
https://transfers.bankofamerica.com/jsp/bofa/ft_overview
https://transfers.bankofamerica.com/jsp/bofa/make_transfer
https://secure.bankofamerica.com/myaccounts/signoff/signoff-default
- The threat actor accessed Bank of America’s login page, successfully logged in, and viewed account details through the “Accounts Overview” page. This suggests the actor has access to online banking credentials or session cookies found in infostealer logs.
- The individual accessed the “Transfers to Other Banks” feature, possibly with the intent to transfer funds to external accounts. The URL paths, particularly those mentioning “interbankTransfersSA” and “cashedge,” suggest an attempt to move money between different financial institutions, potentially to accounts the threat actor controls or to launder funds.
- These URLs show the threat actor navigating through pages to validate emails, add new external accounts, and manage accounts for transfer purposes. This step is essential in linking external bank accounts to facilitate fraudulent transfers.
- The actor likely proceeded to make transfers to either domestic or international accounts. The final URL indicates that the system was used to initiate and manage financial transfers.
- After completing their activities, the actor signs off from the account.
This instance is a common example of how threat actors use infostealer logs, searching for easily accessible financial credentials, gaining access, and transferring money to an account that the actor can use to further forward the illicitly gained funds on.
Best Practices for Security Teams: Preventing, Detecting, and Remediating Stealer Logs
Organizations can prevent, detect, and remediate stealer logs by implementing these measures:
- Password managers: Encourage employees to use a password manager and not save their passwords in the browser. It can eliminate a significant amount of risk.
- MFA: Multi-factor authentication adds another layer of security to corporate devices. Stealer logs can steal session cookies, but it’s possible they aren’t fresh enough to use.
- Employee training: Employees are the first layer of defense against external risks. Providing cybersecurity training, especially additional training for users who fail the initial training, will holistically improve the organization’s defenses.
- Personal device policies: Employees saving corporate credentials in their personal devices’ browsers are a major risk factor. It’s also crucial for employees not to share work devices with other people. Strict policies on how employees should use work and personal devices would greatly help with avoiding infostealer malware.
- Restricting download privileges: Limit the ability to download and install software to a select group of users. Implement application whitelisting to prevent unauthorized software, which is often a source of infostealer infections.
- Stealer log monitoring: Make sure your Continuous Threat Exposure Management plan includes monitoring for stealer logs across the clear, deep, and dark web. It will help your organization discover potential data leaks sooner.
How Flare Addresses the Threat of Stealer Logs
How does Flare monitor for stealer logs?
Looking through illicit sources manually can be incredibly difficult, and searching for stealer logs relevant to your organization makes that search even more challenging.
Flare’s Threat Exposure Management (TEM) solution automatically monitors the clear & dark web to deliver prioritized actionable intelligence on external threats, including stealer logs.
We are tracking more than 100 million stealer logs with over 1.3 million new stealer logs per week.
To learn more about stealer logs and corporate access, read the report on Stealer Logs, Single Sign On, and the New Era of Corporate Cybercrime.
Monitoring for Stealer Logs with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.


