
This blog was updated on June 26th, 2025.
Stolen credentials are big business among cybercriminals. According to Verizon’s latest Data Breach Investigation Report (DBIR), credentials were involved in 88% of basic web application attack breaches, making them the most common initial attack vector — and sometimes, the only vector used in an attack.
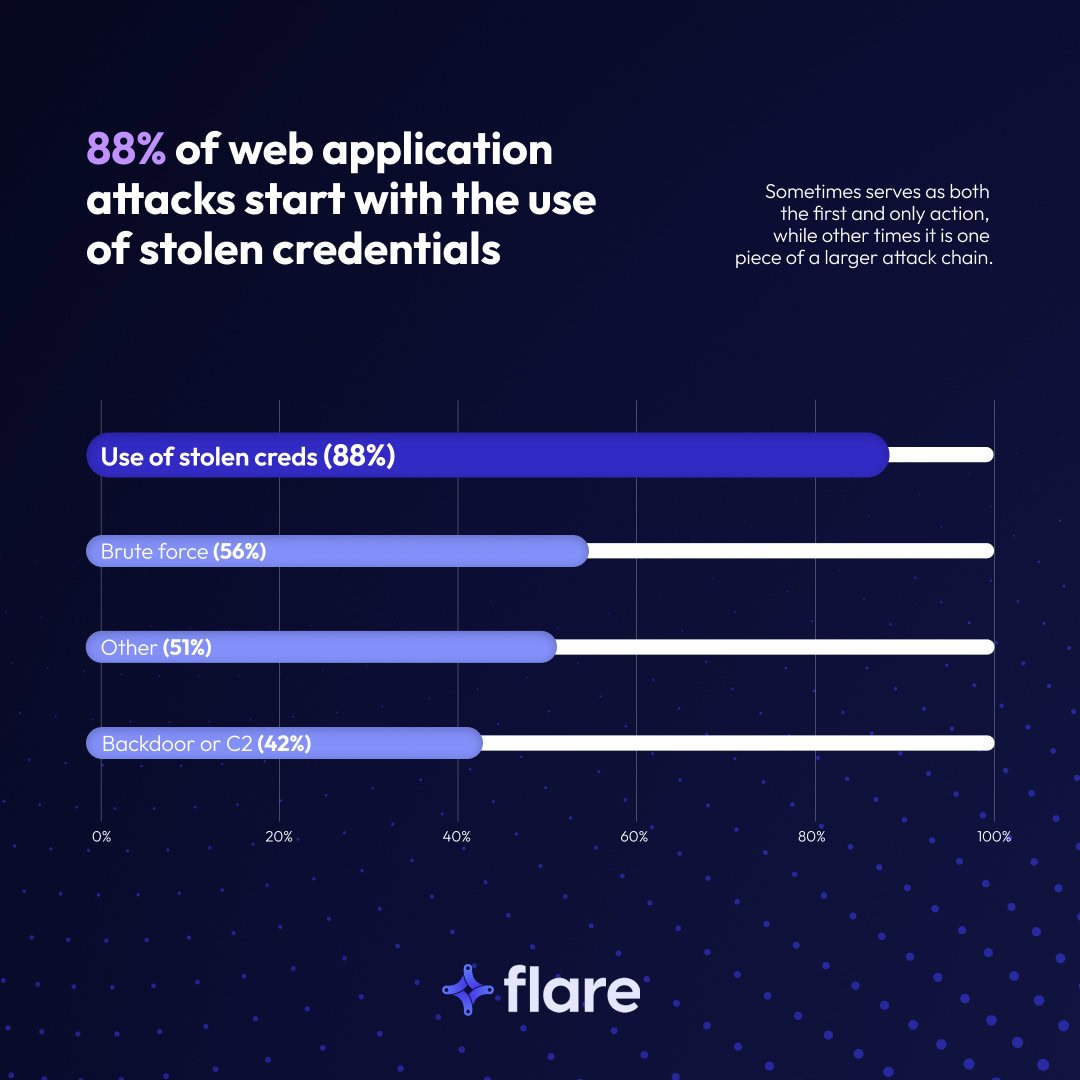
According to the Verizon DBIR 2025, web application attacks primarily begin with stolen credentials
How do threat actors get those passwords? A lot of the time, it’s through infostealer malware.
Infostealers have become an essential piece of the cybercrime economy, so much so that they’ve spawned their own ecosystem, complete with infostealer vendors, subscription-based pricing models, infostealer operators, stealer log brokers, and buyers.
The infostealer ecosystem has also had a marked effect on other types of cyber crime. Take ransomware, for example. According to the DBIR, 54% of ransomware victims’ credentials were found in infostealer logs, and 40% of those logs included corporate emails.
What is Infostealer Malware?
Infostealers are sophisticated remote access Trojans (RATs) that silently infect computers, picking up massive amounts of sensitive information, like session cookies, system data, and passwords. The infostealer compiles the stolen data into a stealer log and sends it back to the attackers.
Once the log is exfiltrated, the attacker then distributes it to other threat actors in cybercrime marketplaces on the dark web (like Russian Market), in prominent threat actor forums, or using a messaging platform like Telegram. Stealer logs may be sold, but are sometimes distributed as free samples — vendors often promote their channels and other offerings with daily and weekly samples of their wares.
Both purchased logs and the free samples are then used by other criminals to launch their own attacks such as:
- financial fraud
- data breaches
- Account and session takeovers
- ransomware attacks
What’s in an Info(stealer) Log?
Every stealer log represents a single user’s stolen data, and usually includes a snapshot of their browser and key details about their computer.
Not all stealers contain the same information, however. Different infostealer variants pull different types of data. (This can be a differentiator in the malware market; competing infostealer developers target specific types of data.) For example, one variant may pull clipboard data from the user while another variant may not.
Why not pull all data from a user? Malware developers realize that this would be counterproductive — the more data stolen by an infostealer, the more likely it is to be detected and stopped by Windows Defender or another anti-virus platform. There is a constant tension between the amount of data being stolen and keeping malware hidden.
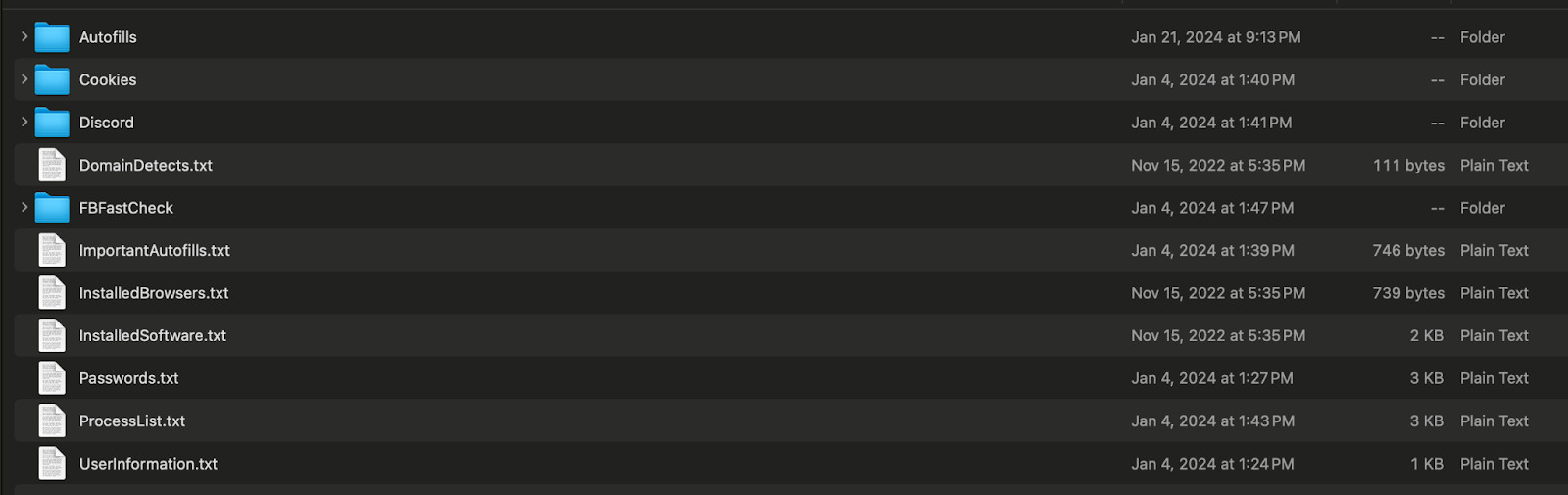
An infostealer log with separate .txt files for different types of stolen data
Here’s what’s in the infostealer log above:
- Autofills: This folder contains stolen data related to autofill functionality from web browsers, including names, addresses, and payment details. If compromised, this data can be used for identity theft or fraudulent transactions.
- Cookies: This folder holds browser cookies, which store session data and login credentials for websites. Stolen cookies could allow attackers to bypass authentication mechanisms and hijack active sessions, leading to account takeovers.
- Discord: This folder might store session tokens or credentials related to the Discord platform. Compromising these tokens could give attackers access to the victim’s Discord account, enabling them to steal sensitive communications or impersonate the user.
- DomainDetects.txt: This text file logs domains detected or visited by the victim. It could be useful for understanding the victim’s browsing behavior or identifying phishing targets.
- FBFastCheck: This is actually an advertisement for another subscription service the channel owner offers which enables users to quickly sort through stealer logs to identify the type of credentials they are after.
- ImportantAutofills.txt: This file stores more critical autofill information such as sensitive entries like payment cards, billing addresses, or personally identifiable information (PII) from browser autofill data.
- InstalledBrowsers.txt: A list of browsers installed on the victim’s system.
- InstalledSoftware.txt: Contains a list of all software installed on the victim’s machine.
- Passwords.txt: This file is critical, as it contains cleartext passwords harvested from the victim’s browser.
- ProcessList.txt: This file logs running processes on the victim’s machine at the time of the infostealer infection.
- UserInformation.txt: This file contains detailed information about the victim’s account or system, such as usernames, computer names, or operating system details. It also contains information about the infection date and build of the malware.
The Infostealer Malware-as-a-Service Ecosystem
Modern infostealers operate within a sophisticated Malware-as-a-Service (MaaS) ecosystem, that looks almost like the legitimate Software-as-a-Service (SaaS) economy; vendors offer support, automated subscription payments, and user dashboards.
Infostealers are distributed via malware markets, forums, Telegram channels, and private deals. There are also affiliate programs that allow other criminals to act as resellers.
The pricing structure varies, depending on the stealer variant. In the last 2 years, prices of stealer log subscriptions have mostly remained the same.
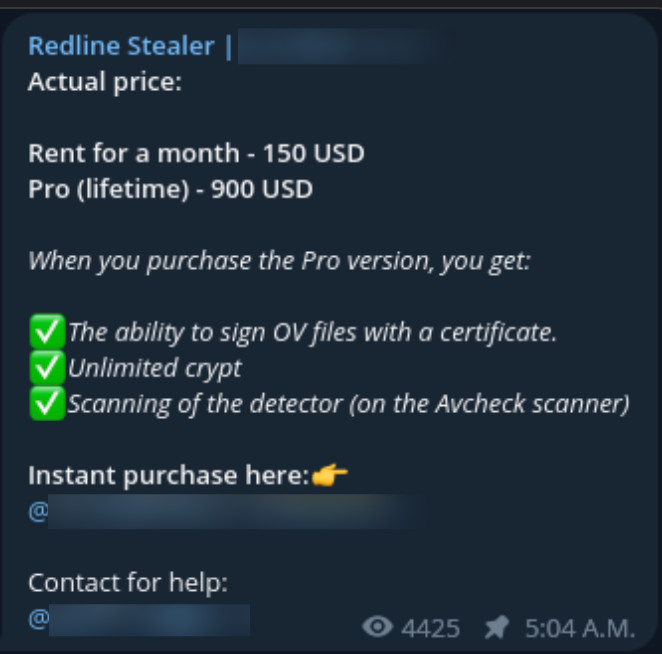
Telegram post of a redline stealer for sale
Standard variants:
- Monthly subscription model
- Price range: $130-170 USD
- Payments accepted in cryptocurrency
- Includes C2 infrastructure hosting
Specialized variants:
- macOS stealers command premium pricing
- Higher prices reflect limited competition in the Mac malware space, however, there has recently been an increase in the number of stealers targeting macOS, so this may change.
MaaS vendors fulfill a critical role in the ecosystem. Malware development is difficult and time-consuming and requires substantial expertise – particularly to get around modern AV/EDR systems. By having specialized infostealer developers maintaining their own code and selling it as a service, they can leverage the economic principle of role specialization while making a significant profit, particularly for developers that build popular variants such as Redline.
Infostealer Distribution: Common Attack Patterns
After acquiring an infostealer variant, cybercriminals employ various distribution methods to infect victim systems. While multiple approaches exist, the most prevalent involves embedding malware within purported “cracked” software downloads.
Below is the typical attack flow:
- Initial Setup
- Threat actor purchases an infostealer variant through Telegram channels
- Package typically includes C2 infrastructure
- Some variants come with detailed infection pipeline documentation
- Distribution Infrastructure
- Creates landing pages using either paste-type sites, stolen websites, or sites hosted on bulletproof hosting
- Uploads malicious payload to file-sharing platforms (e.g., Mega.nz)
- Uses password protection to bypass antivirus scanning during download
- Traffic Generation
- Acquires compromised Google Ads accounts
- Purchases compromised YouTube accounts
- Use these platforms to advertise (real or fake) cracked software seeded with infostealer
- Data Exfiltration
- Victims download and execute the malicious files
- Infostealer harvests various data types:
- Login credentials
- Browser data
- System information
- Stolen data is transmitted to:
- Dedicated C2 infrastructure
- Telegram channels (in some configurations)
While cracked software distribution is common, sophisticated threat actors may employ other techniques:
- Targeted phishing campaigns
- Watering hole attacks
One particularly interesting campaign occurred in mid-2023 and targeted potential users of the AI platform Midjourney. This campaign leveraged several of the aforementioned features – malicious google ads likely being run from compromised accounts.
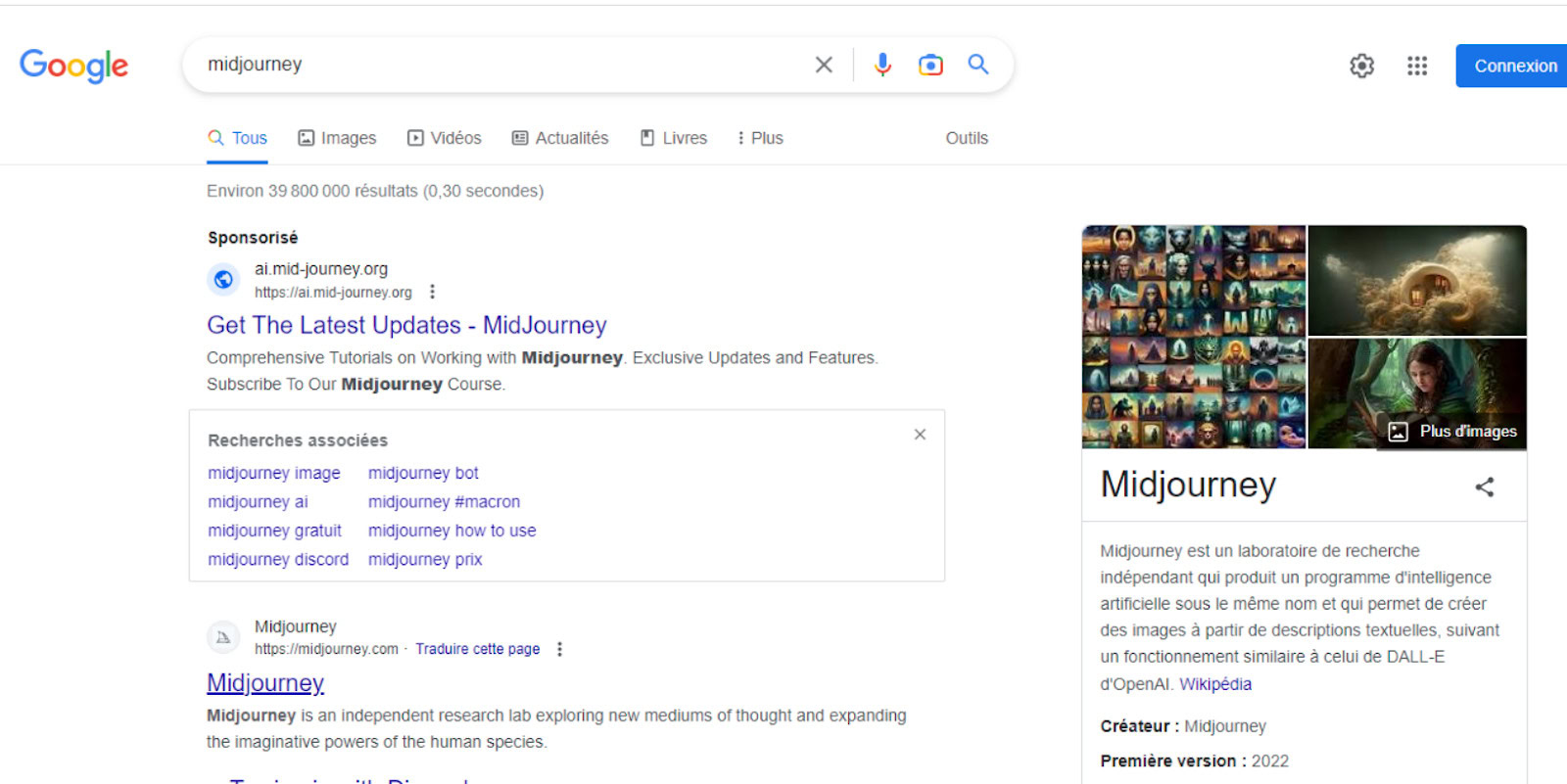
A user would search for Midjourney and the first result was the now defunct “ai.mid-journye.org” which was advertised using Google Ads. Clicking on the advertisement would bring the user to a custom build landing page.
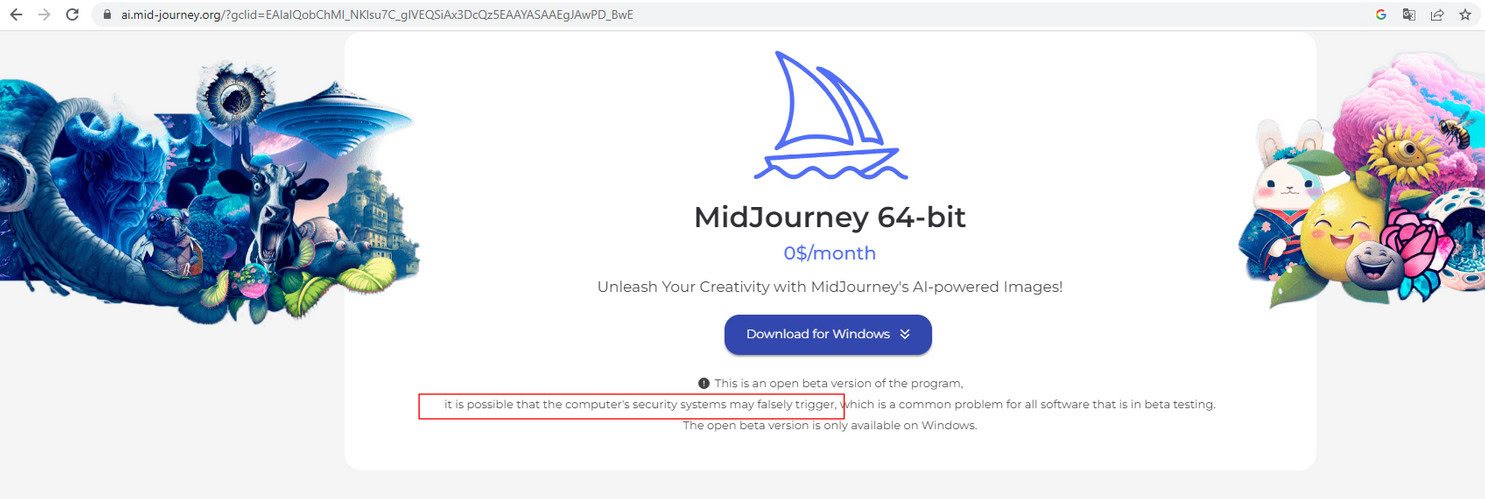
The landing page was fairly sophisticated and well designed to entice the user to download the Windows application. Note the highlighted red “it is possible that the computer’s security systems may falsely trigger” and the lack of a MacOS option.
Info(stealer) Log Distribution
Stealer logs are distributed in four main ways:
- Telegram channels: Telegram channels are the top method for stealer distribution in 2025. Automated channels provide bulk infostealer logs packaged together (typically files with hundreds or thousands of bundled logs). Threat actors use their public rooms as a way to build reputation and credibility, and in some cases to promote their private channels which require a paid monthly subscription.
- Private Telegram channels: These channels require users to pay a monthly subscription fee and sometimes limit the number of users in a specific channel (to 5-20 individuals). Prices range from $100 to $500 a month and heavily depend on the reputation of the threat actor and the frequency with which new logs are published to the channel.
- Live logs: Sometimes threat actors sell access to live logs. In this case, Telegram serves as a backend where logs are sent directly upon a victim being infected. There is substantial time relevancy to logs – newer logs are more likely to contain unexpired session cookies and unchanged credentials – providing the threat actor maximal opportunity to gain unauthorized access to core services.
- Russian Market: Russian Market is a marketplace operating as a dark web hidden service which allows infostealer distributors to bulk upload logs that are sold for $10 each. Russian Market also enables buyers to search through logs and identify those with specific credential sets they are interested in compromising prior to purchase.
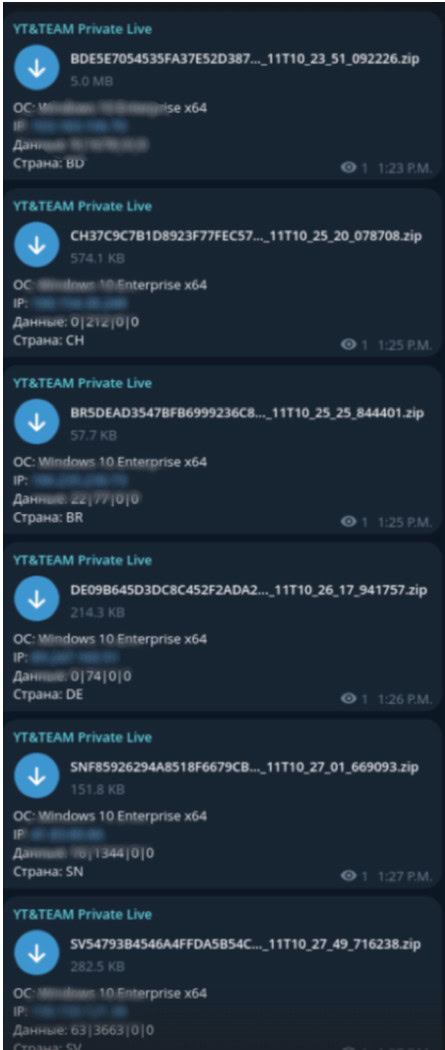
Stealer logs for purchase and download
Time and the Relevance of Infostealer Logs
Like baked goods, stealer logs are more desirable when they’re fresh, and go stale surprisingly quickly. Threat actors want the newest stealer logs (and are willing to pay for them) for a number of reasons:
- Fresh logs are much more likely to include active session cookies which can be used to bypass MFA on web applications. To do this, threat actors use what is called an “anti-detect” browser.
- Threat actors disproportionately value fresh logs due to the fact that the session cookies are more likely to be valid.
- Utilizing new logs also makes it less likely that another threat actor has already gained access to financial resources, crypto wallets, and other data in the stealer log.
Infostealer Log Use Cases
Why do threat actors use infostealers? The biggest use cases are fraud and — no big surprise here — monetary gain.
- Account takeovers: Infostealers capture login credentials from browsers, VPN clients, and remote desktop apps. They also harvest session cookies and tokens, which can be used to bypass multi-factor authentication and gain instant access to corporate systems. This makes them a perfect tool for account takeovers and internal pivoting.
- Financial gain: Stolen credentials are sold on dark web markets for anywhere from $1 to hundreds of dollars, depending on value. In addition, access to wallet files, banking logins, and crypto seed phrases can be used to drain funds directly.
- For future attacks: Infostealers are often the first step in ransomware or data extortion attacks. They allow initial access brokers (IABs) to collect and sell entry points into corporate environments. The data is used to escalate privileges, move laterally, and deliver more destructive malware.
Threat actors are primarily not looking to compromise corporate accounts, nor is it the reason that the vast majority of threat actors use them, instead a typical workflow might look something like this:
1. Threat actors process downloaded logs through specialized “checker” applications that:
- Validate session cookie authenticity
- Filter logs based on customizable parameters
- Flag high-value targets (e.g., active financial service sessions)
- Prioritize logs containing authenticated access to valuable services
The checker tool essentially serves as a triage system, allowing actors to quickly identify and prioritize the most potentially valuable compromised accounts from large batches of logs.
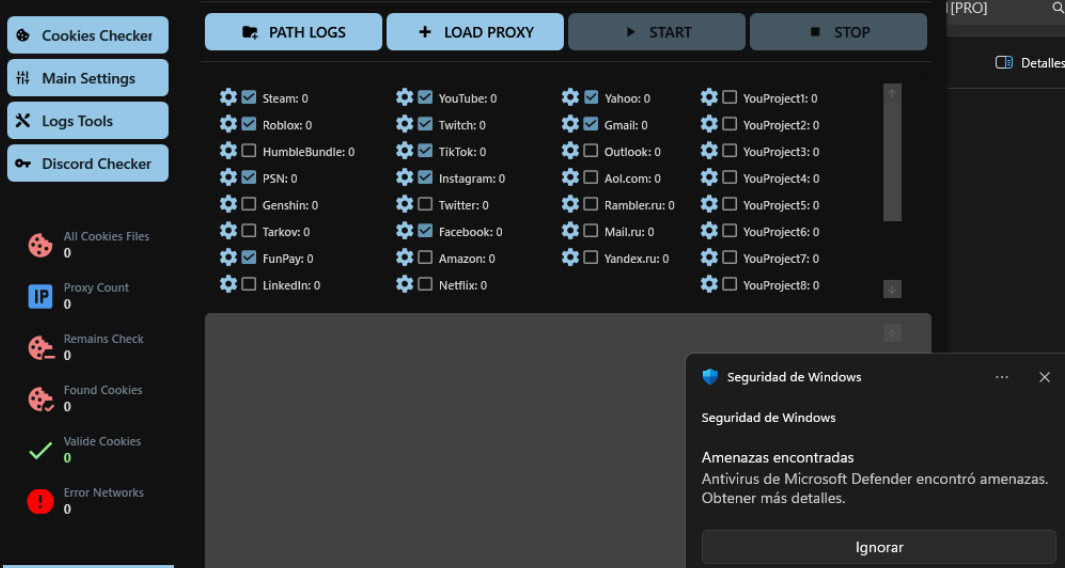
A threat actor uses a checker to identify high-value logs
2. The actor then uses an anti-detect browser to impersonate the victims session on specially selected financial services logs.
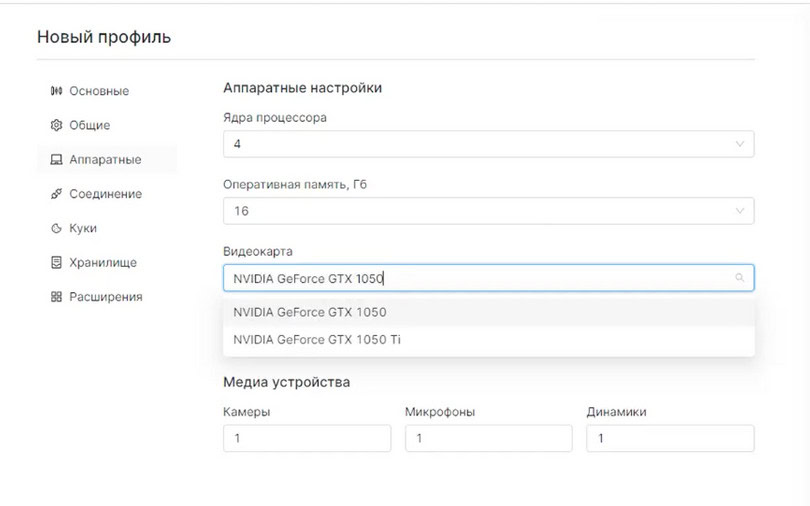
Screenshot of an anti-detect browser from a tutorial video on how to impersonate sessions
3. The actor gains access to the account and transfers money or otherwise buys cryptocurrency using the victim’s bank account.
Infostealer Malware and Corporate Cybersecurity
Infostealers have largely flown under the radar for corporate security teams, particularly those at smaller organizations or those with a less sophisticated security posture. Unfortunately they have not flown under the radar for threat actors looking for easy ways to compromise corporate IT environments.
Why? Millions of employees in the U.S. save credentials from their jobs onto their personal computers and subsequently get compromised by infostealer malware. Our own research found evidence of this; out of more than 33,000 stealer logs, 30% of the compromised systems were enterprise-licensed, meaning that they were corporate devices. We also discovered that 46% of the compromised devices with potential corporate credentials were non-managed. This means that these breaches might have been prevented with better BYOD controls, or a crackdown on shadow IT.
The irony of this is that the average threat actor doesn’t target infostealer campaigns at corporate employees. However, if a bad actor infects tens of millions of computers, huge numbers of corporate credentials and session cookies are bound to show up.
This is well known by ransomware groups and other criminal entities that target businesses. Both ransomware actors and initial access brokers directly leverage stealer logs and infostealer malware infections to gain access to corporate IT systems.
To learn more about threat actors and corporate stealer logs, take a look at our report Stealer Logs, Single Sign On, and the New Era of Corporate Cybercrime.
Infostealer Malware & Initial Access Brokers
Infostealer malware is likely one of the most common ways that initial access brokers get into corporate networks. Initial access brokers (IABs) serve as a “white glove” service for ransomware groups and other criminal entities, gaining initial access to a victims corporate systems, then auctioning it off on Russian language cybercrime forums.
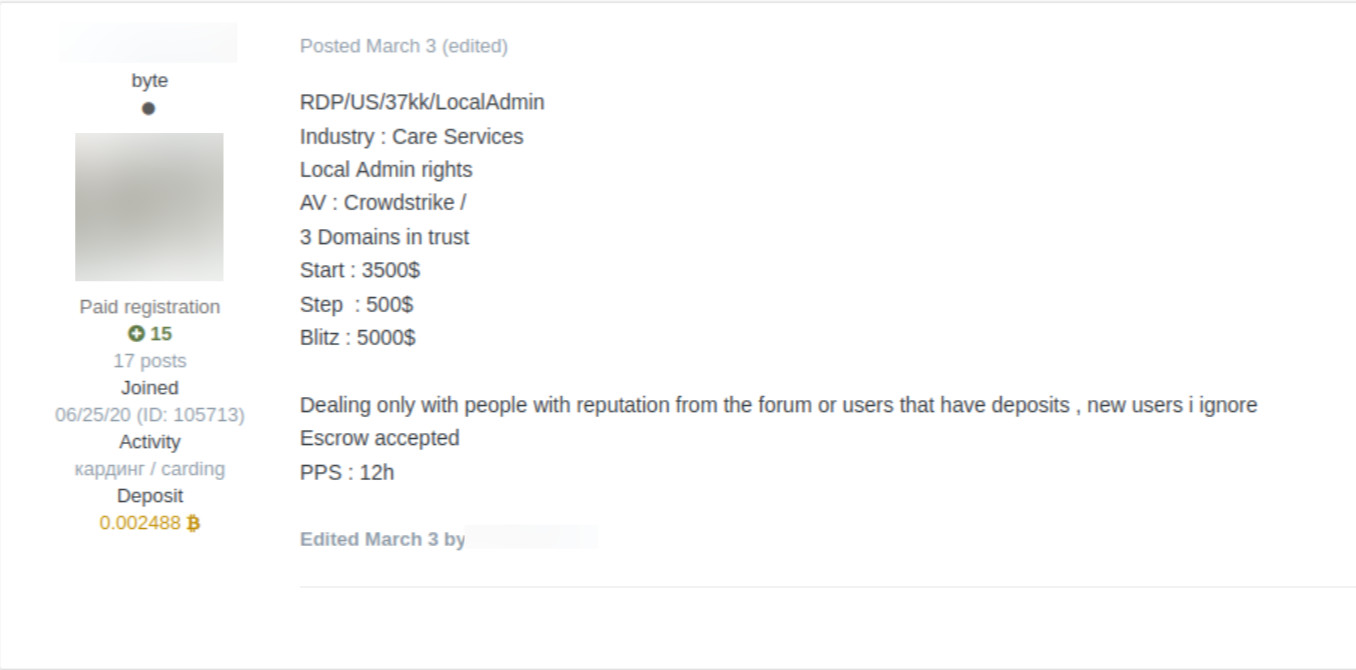
Forum post from initial access broker
When there are millions of corporate credentials and session cookies floating around Telegram, it defeats much of the need for threat actors to launch more complicated attacks such as spear-phishing or exploiting vulnerabilities on publicly facing hosts.
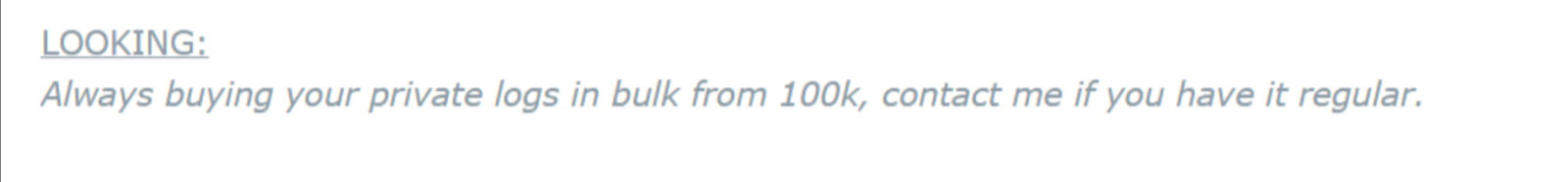
An initial access broker advertises logs for sale on the Russian language cybercrime forum XSS
For example, an attack facilitated by an initial access broker might look something like this:
- IAB purchases an infostealer log from a dark web marketplace. The log contains credentials, session cookies, and other sensitive data from multiple victims.
- Among the entries, they identify a high-value target: credentials for a user with an email from a mid-sized financial services firm.
- Using a virtual private server (VPS) or proxy to match the target’s geographic location, the IAB attempts to log into the financial firm’s VPN with the stolen credentials.
- Login is successful, and they are granted access to the internal network.
- The IAB installs a covert remote access tool (RAT) to maintain control even if the VPN password changes.
- They create a hidden administrator account to re-enter if the initial access point is detected or closed.
- Using the RAT, the IAB maps the network, identifying key systems like file servers, databases, and sensitive applications.
- They collect more internal credentials, including administrative passwords, using tools like Mimikatz.
- The IAB gathers the details of the access they’ve achieved:
- VPN login credentials
- Privileged admin access to specific systems
- Network map and location of sensitive financial records
- They list this package on a dark web forum, advertising it as “Administrator-level access to mid-sized financial services firm” and setting a starting price.
- The IAB provides guidance on navigating the network and any details to ensure a smooth handoff.
- The ransomware group uses the access to deploy ransomware across the network, encrypting financial data and issuing a ransom demand to the firm.
Stealer Logs & The Growing Cybercrime Ecosystem
It’s no secret that cybersecurity is adversarial, however in the past decade the nature of offense has changed. The cybercrime economy is vast – stretching into hundreds of millions, and actors ranging from lone wolves to highly coordinated groups leverage it to profit.
The complexity of the ecosystem is a source of its strength. Individual vendors each specializing in particular parts of the attack chain enable role specialization which can create scalability through the “cybercrime assembly line.” If an actor had to design their own infostealer variant, distribute it, harvest credentials, and leverage them it would be a far slower process.
Monitoring for Stealer Logs with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Our customer recently said, “Stealer logs have been the [sources] where we have seen the most actionable intelligence regarding leaked credentials.”
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.





