
The shady underworld of the dark web provides cybercriminals with an outlet to trade stolen information, tools, or malware, hold victims of cyber attacks to ransom, and discuss their targets and tactics. But the dark web forums that normally host illicit marketplaces and discussions are starting to lose their allure. Find out why the messaging app Telegram is emerging as a new dark web frontier and now functions as a popular alternative to traditional dark web forums.
Curious about other illicit sources to include in your monitoring strategy? Take a look at our top illicit sources to monitor in 2023.
Table of Contents
• Why Are Cybercriminals Turning to Telegram?
• Real World Cyber-Crime on Telegram
• Will Telegram Make the Dark Web Redundant?
• Monitoring Illicit Telegram Activity
Why Are Cybercriminals Turning to Telegram?
Telegram is a messaging app with enhanced privacy and encryption features. The app works across popular mobile and desktop platforms and syncs messages across all of a user’s registered devices. Aside from private one-to-one conversations, Telegram users can subscribe to channels on which owners post content or they can become members of groups in which all participants discuss topics.
Research from 2021 found a 100% rise in Telegram usage by cybercriminals. The natural question then is what factors explain this meteoric rise?
Illicit Telegram Groups Provide Better Anonymity
Cybercriminals doubt just how much anonymity they get when using dark web forums that administrators can easily monitor. While IP addresses and geolocations get hidden automatically through a special type of routing, there is the fear of being monitored by admins and having identities revealed. Telegram has no traditional admins monitoring its groups and one-to-one chats, which is attractive for anonymity. Threat actors can also hide their phone numbers on the service.
Illicit Telegram Groups Offer Encrypted Communications
Encryption is an interesting topic when it comes to illicit cybercriminal activity. Telegram offers end-to-end encryption for messages by default, which helps to avoid potential man-in-the-middle attacks that can snoop on messages in transit. Dark web forums and marketplaces also have an encryption option but threat actors need to use something like Pretty Good Privacy (PGP) to ensure encryption, which is less convenient.
Illicit Telegram Groups Offer Hardened Operations
Another important factor is how Telegram offers hacking groups and lone wolf actors a way of hardening their operations. Having to register a domain to offer services and tools for sale makes threat actors’ operations vulnerable to distributed denial of service (DDoS) attacks that can take them offline. Telegram channels bypass this requirement for a domain and ensure cybercriminals can stay online as long as the Telegram service remains online.
Real-World Cyber Crime on Telegram
With an understanding of why threat actors increasingly opt for Telegram, it’s worth taking a look at some real-world cases that highlight the danger of this new dark web frontier.
PlayBook Sports Data Leak
Online privacy advocate vpnMentor’s research uncovered a data leak containing personal information on over 100,000 US citizens from the sports betting tips website PlayBook Sports. The data exposure included email addresses, home addresses, and full names of affected individuals.
Combolist
A public Telegram channel named Combolist attracted over 45,000 subscribers all interested in buying and downloading data dumps containing compromised username and password credentials. A Financial Times report led to the channel’s removal from Telegram after separate posts offered 300,000 emails and passwords for video game platforms and 600,000 logins for popular web services like Yahoo and Yandex.
Remote Access Tools and Info Stealers for Sale
Posts about remote access tools and info stealers are prevalent on many Telegram channels and groups. Particularly popular are SpyMax and Mobihok, which provide remote access to Android devices. Info stealers like RedLine and Oski Stealer that covertly steal information from user devices are also widely available for a fee.
Vulnerability Exploits
Integrate the world’s easiest to use and most comprehensive cybercrime database into your security program in 30 minutes.
Also widely seen on Telegram channels and groups are exploits for various cybersecurity vulnerabilities. The most widely seen exploits include a remote code execution vulnerability in Microsoft Remote Procedure Call (RPC) and remote code execution bug known as Spring4Shell in the popular Java Spring framework.
Common Threats on Telegram
We see many of the same threats on Illicit Telegram channels that we see on dedicated dark web markets and forums. In many cases threat actors have moved directly off of more traditional TOR websites, and onto Telegrams offering the exact same goods and services.
Infected Devices and Illicit Telegram Channels
Though Genesis and Russian Markets are established autoshops where threat actors can buy and sell infected devices, they can also be found on Telegram channels.
Threat actors distribute stealer logs in various ways depending on the channel. They distribute stealer logs themselves for free, while monetizing access to the channel through subscriptions. This way, they can have access to fresh stealer logs without waiting for autoshop sales. For example, we found a channel with a $100 per month subscription that promises a minimum of 1,000 new logs per day.
Even though they can be sold for just a couple of dollars, browser fingerprints and stealer logs can represent the digital lives of their victims. With saved login credentials and more (especially combined with OSINT), a threat actor could even guess the victim’s general geographic location.
With corporate devices, malicious actors can gain access into companies’ environments.
Want to learn more about stealer malware? Read our report: Dissecting the Dark Web Stealer Malware Lifecycle with the MITRE ATT&CK Framework.
Illicit Telegram Channels and Stolen Credentials
There are billions of stolen credentials on the dark web. In the hands of a threat actor, these credentials can be abused to cause horrendous data breaches for individuals and organizations. Illicit Telegram channels are a common new vector that facilitates the routine distribution of stolen credentials. In some cases this may be for free and in other cases the credentials may be purchased through automated mechanisms on specific channels.
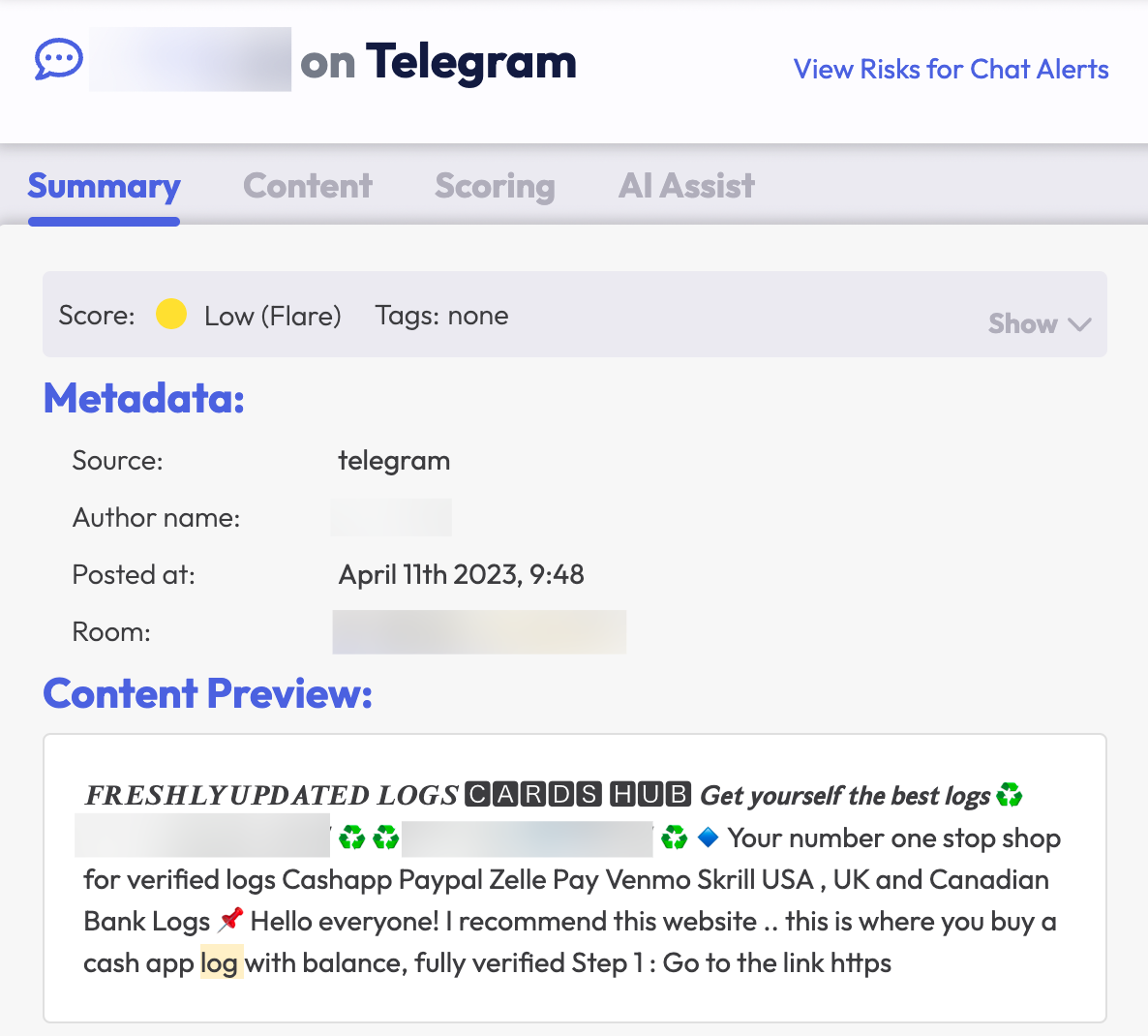
Are you curious about Telegram channels and stolen credentials? Check out our Threat Spotlights on leaked credentials and on leaked credentials and geography.
Illicit Telegram Channels and OTP Bots
Through one-time password bots (OTP bots), threat actors can try to collect 2FA codes from victims at scale. When we conducted a search in 2022 on Telegram for the terms “OTP Bot” and “2FA Bot,” we found 1,700 results. To give more context: below are the number of results searching in the same chatrooms for the following terms:
- “Vbv”: 2,500 results
- “Fullz”: 50,000 results
- “No2fa”: 3,300 results
There is an active demand for OTP bots, as many of these results displayed activity within minutes of the query. Generally, malicious actors purchase access to bank account login credentials first, then search for OTP bot availability in fraud-oriented Telegram channels.
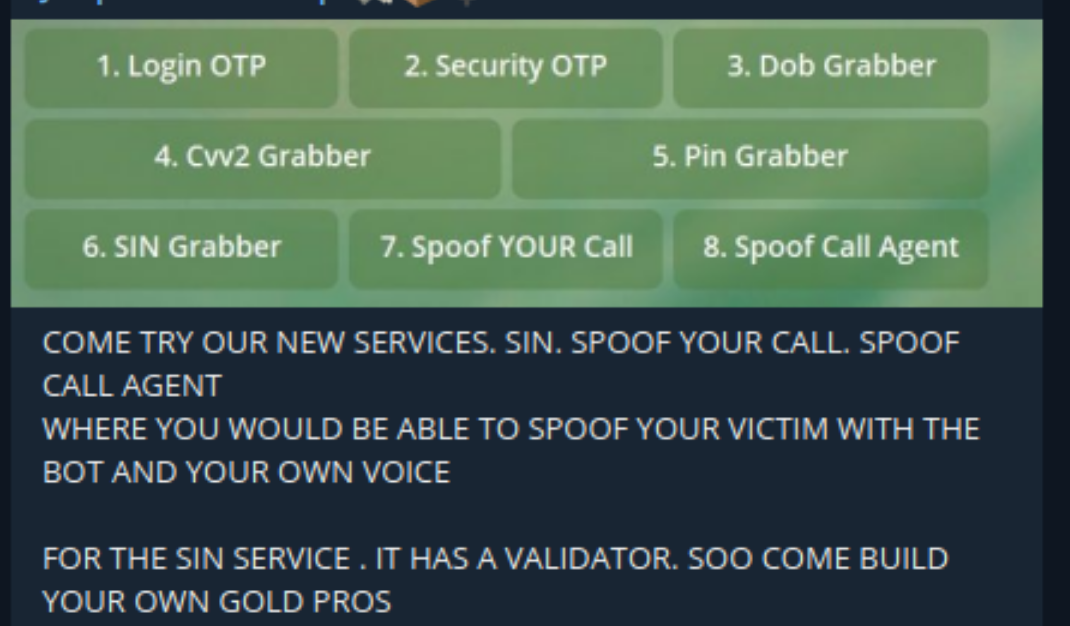
Threat actors typically use OTP bots for personal financial fraud rather than corporate. However, this method could be applied to corporate attacks. For example, if a data breach exposes corporate logins, a malicious actor could find those victims’ phone numbers through OSINT, then leverage that to solicit one-time passwords to bypass 2FA controls. A threat actor applied this TTP in the Cisco breach and a malicious actor used a similar method to cyberattack Uber.
Want to learn more about OTP bots? Take a look at our Threat Spotlight: Illicit Telegram Markets & OTP Bots.
Will Telegram Make the Dark Web Redundant?
Despite the emergence of Telegram as a new dark web frontier, cybercriminals are likely to continue using underground dark web forums. These forums offer a range of features that Telegram does not, such as built-in scoring systems, which allow actors to establish reputations. Telegram’s previously hands-off approach and refusal to cooperate with law enforcement have also changed with the removal of several illicit channels and groups that garnered lots of subscribers.
The dark web is unlikely to get abandoned any time soon as a cybercrime hub. Expect cybercriminals to split their operations between messaging apps and traditional underground forums and marketplaces. Comprehensive monitoring requires coverage of both the dark web and messaging apps.
Monitoring Illicit Telegram Activity with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and illicit Telegram channels 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.


