
Executive Overview
The top illicit communities to monitor this year are a mix of dark web forums, markets/autoshops, and illicit communities across the instant messaging app Telegram. Most of them had previously existed, and are more recently gaining traction.
A comprehensive cyber threat intelligence strategy includes following a wide range of illicit sources to best understand how to appropriately monitor the external threats to your organization.
As threat actors shift in where they gather, stay up to date with the top illicit communities to keep a close watch on.
1. Russian Market
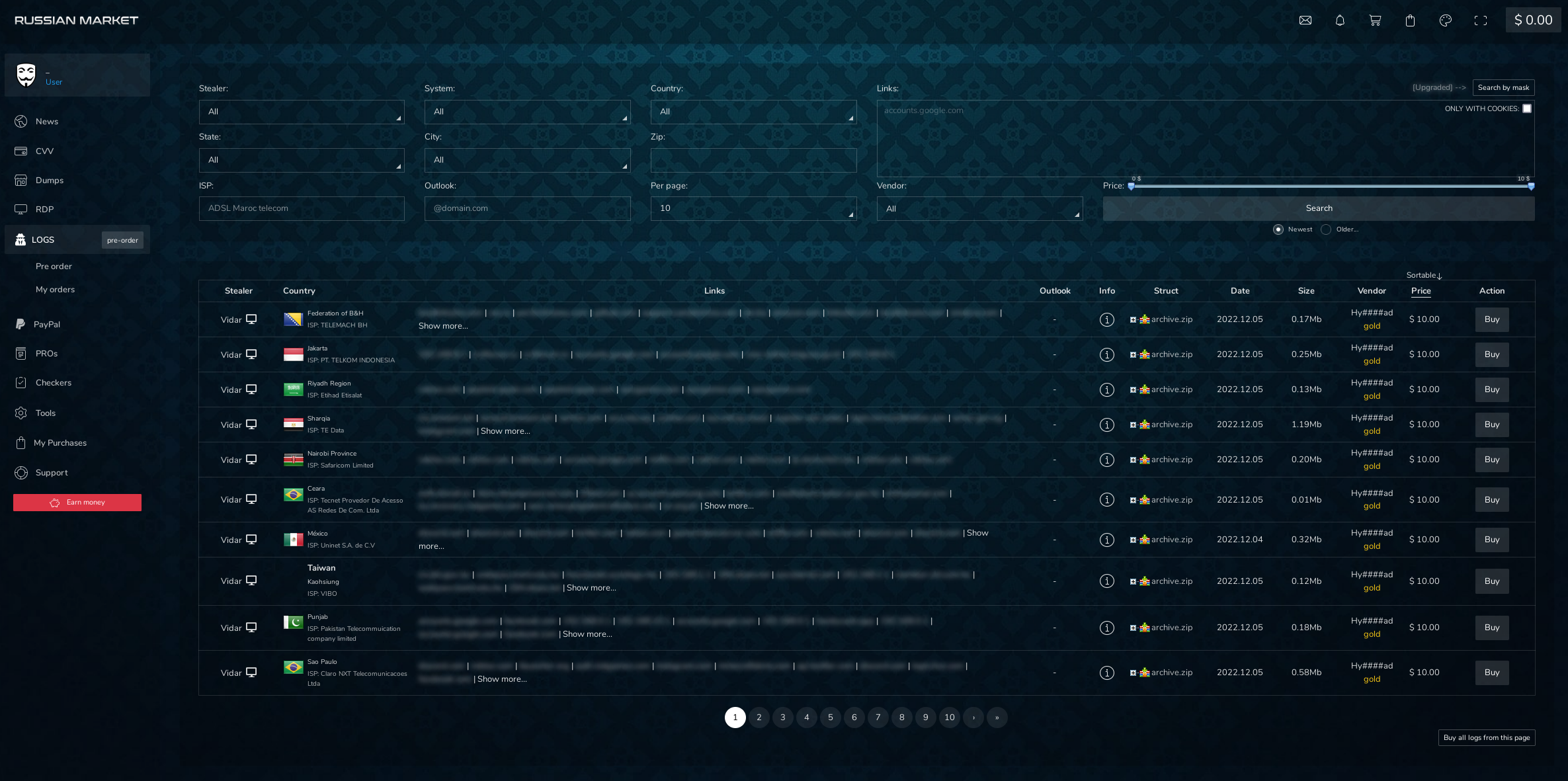
Russian Market is a dark web autoshop that sells stealer logs, which include stolen stored web browser information and some device details. It’s a top infected device market to monitor along with Genesis Market (included below). In a study completed in June 2022 on the stealer malware ecosystem, Russian Market hosted about 2.7 million logs available for sale with about 40,000 new bots for sale that week.
These stealer logs are like a vault of information about the victims. Since they can show saved logins and PII, someone viewing them could make guesses on the general area they live in (maybe even home address), their job, their birthdays, and the places that they often visit. Credential leaks on their own can already be terrifying, especially when a threat actor is skilled at social engineering tactics. However, with stealer logs, malicious actors can dig much deeper into someone’s life or into an organization. The price tag for all of this information is surprisingly low, at about $10 per stealer log.
2. Genesis Market
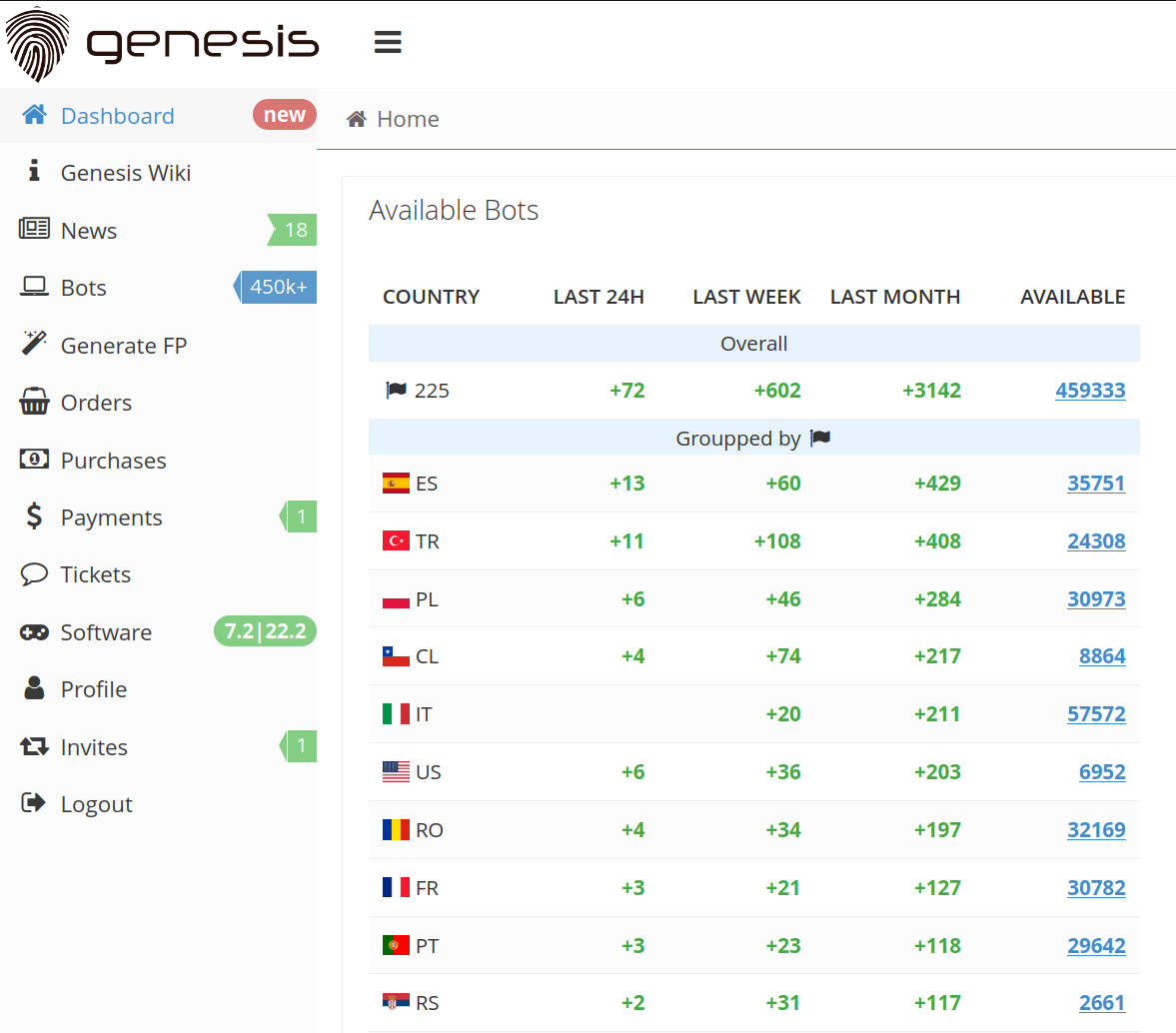
Genesis Market is similar to Russian Market. However, it operates on the clear web, and specializes in selling browser fingerprints. In an analysis completed in June 2022 on the stealer malware ecosystem, Genesis Market had about 400,000 bots for sale with about 1,600 new bots for sale that week.
The stealer logs have a greater range in cost than on Russian Market, ranging from about less than a dollar to a little over $170.
When malicious actors purchase a bot on Genesis Market, they can also gain access to detailed guides on how to use the purchased bot fingerprints.
3. Telegram
Dark web forums used to be the go-to destination for threat actors, but they’re moving more to instant messaging platforms like Telegram. Unlike dark web sources that are intensely monitored by various law enforcement agencies and cybersecurity teams, these platforms are more appealing to use because:
- The platform is more reliable than a forum that often changes hosting systems
- Strict privacy policies establish a sense of safety (whether that feeling is accurate or not)
- Some channels have the “disappearing messages” setting that can delete messages after a certain amount of time, like in 24 hours
- The interactions can feel “less permanent,” as with the rapid flow of messages, even existing messages can seem to get washed away and disappear, even if they still technically exist
4. Stealer Logs
Stealer logs are the result of stealer malware infecting devices to steal information stored on the victim’s web browser. With the forms, logins, cookies, and credentials from the victim’s browser, threat actors can impersonate their victim to gain access to their accounts, usually for financial gain.
Curious about the lifecycle of a stealer malware attack? Learn the details in our new report: Dissecting the Dark Web Stealer Malware Lifecycle with the MITRE ATT&CK Framework.
Integrate the world’s easiest to use and most comprehensive cybercrime database into your security program in 30 minutes.
5. Exploit.in
Exploit.in is a dark web forum featuring a robust auction system. The dominant language used on the forum is Russian. Some content is hidden behind participatory walls that threat actors can gain more access to by establishing a greater reputation through sharing and buying.
Some forum users are “initial access brokers” and sell information about organizations’ VPNs or administrative powers to provide access into those companies’ environments, through the forum’s auction system. Other malicious actors can bid either in private messages (to keep their usernames private) or in the thread directly.
Threat actors also share proof of concept for exploits, malware samples, and various hacking techniques on this forum.
6. Cracked.io
Cracked.io is a forum with a strong focus on sharing credential leaks. Threat actors sell and share combo lists often from breaches that are initially shared elsewhere on the dark web, as well as leaked databases and various breaches.
Resharing content from other forums is common, which contributes to a large volume of posts in this forum.
7. XSS.is
XSS.is is a Russian-language dominated forum similar to Exploit.in. Forum users can build reputation points through the forum’s system or pay for a VIP account that bypasses this system. Malicious actors who frequently post relevant content can get more likes on their posts which provides them greater access to various threads.
This is a pretty technical forum with posts about new hacking tools, proofs of concept, red teaming tools, and more. A lot of leaks originate here.
8. Breached Forums
Pompompurin, a prominent member of RaidForums, which was shut down by law enforcement in January 2022, launched Breached Forums just a few months later, in March 2022. This forum quickly gained notoriety as the central place to share leaks and breaches. On this forum, threat actors can sell the results of exploited systems.
9. ASAP Market
ASAP Market is one of the biggest dark web markets; facilitating the sale of drugs, fraud-related items, and more. This is an international market, but buyers can check where items are shipped from in order to purchase local items. This way, buyers can avoid customs checking packages that arrive from outside of the country.
10. We the North
We The North is a Canadian exclusive dark web marketplace; meaning products may only ship to and from Canada. We The North rose in popularity after the downfall of a previous Canadian exclusive marketplace, Canadian HQ. Just like its predecessor, We The North hosts a wide array of items for sale, with a strong offering of digital items, especially related to financial fraud.
How Flare Can Help
Though these top illicit sources should be included in your organization’s monitoring approach, they are not the only communities to keep track of. Make sure to follow all sources relevant to the threats your organization faces or is likely to face.
Interested in what monitoring illicit sources with Flare could look like? Try out our free trial option or book a demo to get your questions answered.


