Threat Spotlight: The Dark Web and AI

Executive Overview More than 200,000 credentials to AI language models are currently being sold on the dark web as part of stealer logs, files containing thousands of credentials derived from infostealer malware. This certainly raises the risk that employees will leak sensitive data into models, and then lose the credentials. However, we see even more […]
Threat Intelligence Analytics: Making the Most of Your CTI Program

The threat landscape has never been more challenging for CISOs and security teams than in 2023. Our research has found ransomware attacks have increased by more than 100% since 2022, hundreds of thousands of corporate credentials are being distributed on Telegram with SSO, active directory, and corporate SaaS application credentials, and initial access brokers (IAB) […]
Dark Web Analytics: Detecting Threats Across the Dark Web

The nebulous part of the internet: the dark web, which traditional search engines don’t index, serves as a hub for cybercriminal activity, ranging from illicit trade in stolen data to planning sophisticated cyberattacks. Dark web analytics can help organizations detect potential threats and enable them to proactively protect their digital ecosystem. There are a number […]
Executive Threat Protection: Using Monitoring to Gain the Advantage

The risk of cyber threats has become an everyday reality for many organizations. This risk is amplified when it comes to company executives who, due to their high-profile nature and access to sensitive company data, are likely targets for malicious actors. Threat actors are employing new tactics such as double and triple extortion ransomware and […]
Threat Spotlight: Stealer Logs & Corporate Access

Executive Overview Over the last three years, infostealer malware variants have become a “popular trend” in the cybercriminal Malware-as-a-Service (MaaS) ecosystem. Doing precisely as their category implies, these malware variants steal information from users’ devices. After infecting the device, the malware employs various techniques to remain undetected while sending data to the malicious actors’ command […]
Threat Intelligence Sharing: 5 Best Practices

To combat sophisticated and relentless threats effectively, organizations must adopt a collaborative approach that goes beyond their individual security measures. Threat intelligence sharing has emerged as a powerful strategy to enhance cybersecurity defenses by leveraging the collective knowledge and insights of the cybersecurity community. By exchanging information about emerging threats, attack techniques, and indicators of […]
Actionable Threat Intelligence: Generating Risk Reduction from CTI

Organizations need to go beyond traditional security measures to effectively protect their valuable assets and maintain a strong security posture. They must harness the power of actionable threat intelligence, which provides timely and relevant insights that can drive proactive risk reduction strategies. Actionable threat intelligence empowers organizations to not only understand the threat landscape but […]
Actioning Threat Intelligence Data: The Definitive Guide

Threat intelligence data plays a pivotal role in strengthening any organization’s defense systems. Actionable threat intelligence is critical, and it is an important function in active defense measures. It provides immense benefits through providing context and priority. Adopting a SaaS platform for threat intelligence handling includes useful features such as automation, consolidated data sources, real-time […]
Cybersecurity AI: Threat Actor Profiling Provides Instant Insights

Generative artificial intelligence (AI) and large language models (LLM) dominate current technology conversations. From ChatGPT to DALLE 2, generative AI has become the new hype technology overtaking the corporate world. With all the hype around generative AI, the idea that it is a tool that can enable rather than replace people can get lost. According […]
Unveiling the Dark Web’s Massive Military Data Leak
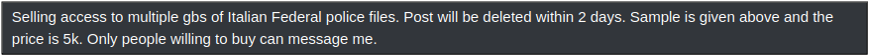
Introduction to Spectre Several threat groups and actors exist in online cybercrime communities with the express goal of hacktivism, which is defined as the use of computer-based techniques such as hacking as a form of civil disobedience to promote a political agenda or social change. These groups are not financially motivated, and are seldom seen […]

