Introduction to Spectre
Several threat groups and actors exist in online cybercrime communities with the express goal of hacktivism, which is defined as the use of computer-based techniques such as hacking as a form of civil disobedience to promote a political agenda or social change. These groups are not financially motivated, and are seldom seen extorting their victims or selling stolen data, but rather giving it away to the world. Historically, the same could be said for a threat actor known as Spectre (often seen going by spectre123, spectre05, and intelbroker online), a likely leader of a hacktivist group known as CyberGuerilla. Spectre maintains a telegram group and website where they publish typically government targeted leaks regularly, often containing files related to human rights or military activities.
Spectres Priorities Shift Financially
In Spectres telegram group, they have not once listed files for sale. Always publishing leaks for free, as is consistent with the motives of a hacktivist. However, earlier this month Spectre offered several gigabytes of the Italian Police’s data for the price of $5,000.

Fig 1 – Spectre listing Italian Federal Police files for sale
Last week, Spectre offered 20 gigabytes of Sri Lankan Naval and Operational data and documents for sale on a popular clearnet and darkweb cybercrime forum, for the price of $5,000, claiming to have sourced the data from a Sri Lankan military insider.

Fig 2 – Spectre claiming Sir Lankan military files were sourced from an insider
Spectres Massive Military and Law Enforcement Data Sale
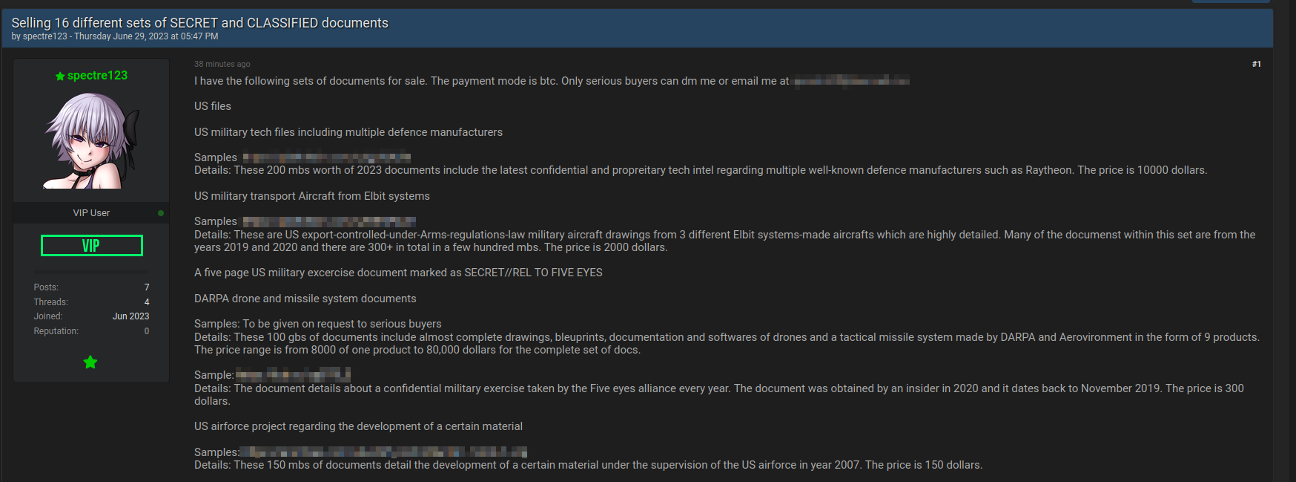
Fig 3 – Spectre posting from June 29th, 2023 of 16 sets of classified military documents.
This recent interest in commodifying their hacktivist activities culminated in Spectre offering a massive collection of government documents, covering a wide variety of military and commercial targets, for sale. This includes classified schematics, drone system software, and even remote access to the Philippines military systems.

The victims, the files for sale, where the data was sources from and the leak prices are as follows:
| Leak Bundle | Source | Size of Bundle | Price |
| Raytheon files regarding confidential and proprietary defense technology | Not listed | 200 MBs | $10,000 |
| Detailed schematics of ITAR controlled Elbit Systems Aircraft | Not listed | 300+ files | $2,000 |
| DARPA Drone and Missile System Documents (several hundreds gigabytes of files covering 9 DARPA products including blueprints, documentation and software) | Not listed | 200+ GB | $80,000
OR $8,000 per product |
| Military exercise files marked as SECRET//REL TO FIVE EYES | Military Insider | Single file | $300 |
| Air Force files regarding development of a ‘certain material’ | Not listed | 150 MBs | $150 |
| Philippines Navy and Coast Guard | Not listed | 15,000 files, 3 GBs | $3,000 |
| Philippines Armed Forces Documents and Databases | Not listed | 15,000 files, 8 GB, database backups | $3,000 |
| Remote access to Philippines Armed Forces System via Shell | Not listed | 1 Shell | Included in above package |
| Indian Artillery Operations | Military Insider | 3.5 GBs | $2,500 |
| India and Pakistan Battle Plans | Not listed | 1.5GBs | $2,000 |
| Indian Army Files | Not listed | 21,000 files, 44 GB | $10,000 |
| Blueberry aviation files regarding military and commercial aircraft | Not listed | 20GB | $8,000 |
| Italian Federal Police Documents | Compromised email | 5.5GB | $5,000 |
| Ecuador Military and Presidency Files | Compromised government systems | 28,000 files, 6 GB | $5,000 |
| Sri Lankan Navy | Military Insider | 1 GB | $1,000 |
| Sri Lankan Naval Intelligence | Military Insider | 19.5 GB | $1,000 |
| British Armed Forces Special communications replacement programme (regarding military ATC, Tactical Data Links, and a variety of aircraft and weapons systems.) | Not listed | 210 MB | $6,000 |
| HJSC – South Korean Naval Assault Ship Manufacturer files | Compromised company system | 10+ GB | $8,000 |
Authenticity of The Leak
With previous leaks by Spectre covering typically politically motivated actions against targets like the Russian Government, this leak appears to be all over the place, covering a truly wide range of targets and programs. The most notable being the DARPA project blueprint, documentation, and software. For virtually all of these leaks, Spectre posts samples of each bundle for the potential buyer to verify its authenticity. Foretraces threat research team confirmed the files appeared to be authentic, though they continue to investigate for confirmation. Some analyzed samples are included below, which we have blurred to obfuscate sensitive content:

Fig 5 – Sample files from British Armed Forces special communication program

Fig 6 – Sample of files from Sri Lankan Military Insider

Fig 7 – Sample of Files from Italian Federal Police

Fig 8 – Sample of Files from the Philippines Armed Forces

Fig 9 – Sample of U.S. Military file marked as ‘SECRET’
Aside from the authenticity of the current files listed for sale, Spectre has a long history of posting military files for free online, often prompting response and investigation from the affected entities. Spectre does not maintain a reputation online as a scammer or a fraud, but rather an active and passionate hacktivist. Let’s take a look at his history online so far:
Spectres History of Online Hacktivism
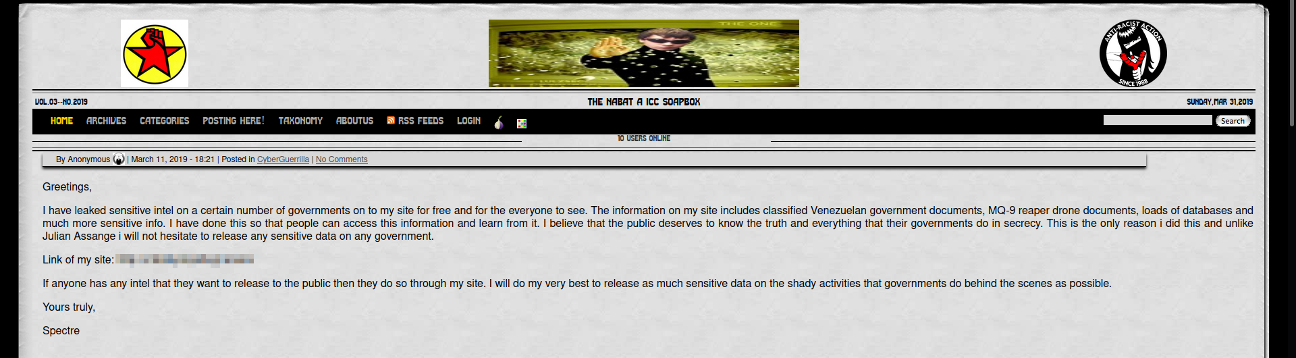
Fig 10 – Spectres role in CyberGuerrilla
Spectre came to prominence in March of 2019 with the publishing of his darkweb repository for stolen military intelligence documents and data, appropriately titled ‘Intel Repository’. Spectre, even as recently as this year, continues to post and purchase leaks from a variety of sources including cyber criminals, other hacktivists, and personnel within the military and post them to his telegram group and darkweb intel repository.
While very occasionally offering data for sale on the now defunkt RAID forums and the recently restored Breach forums, this is the first occurrence of Spectre listing a massive marketplace style post of new leaks for sale. Typically, Spectre simply posts leaks for free under the ‘Confidential/Sensitive Intel’ section of his website.
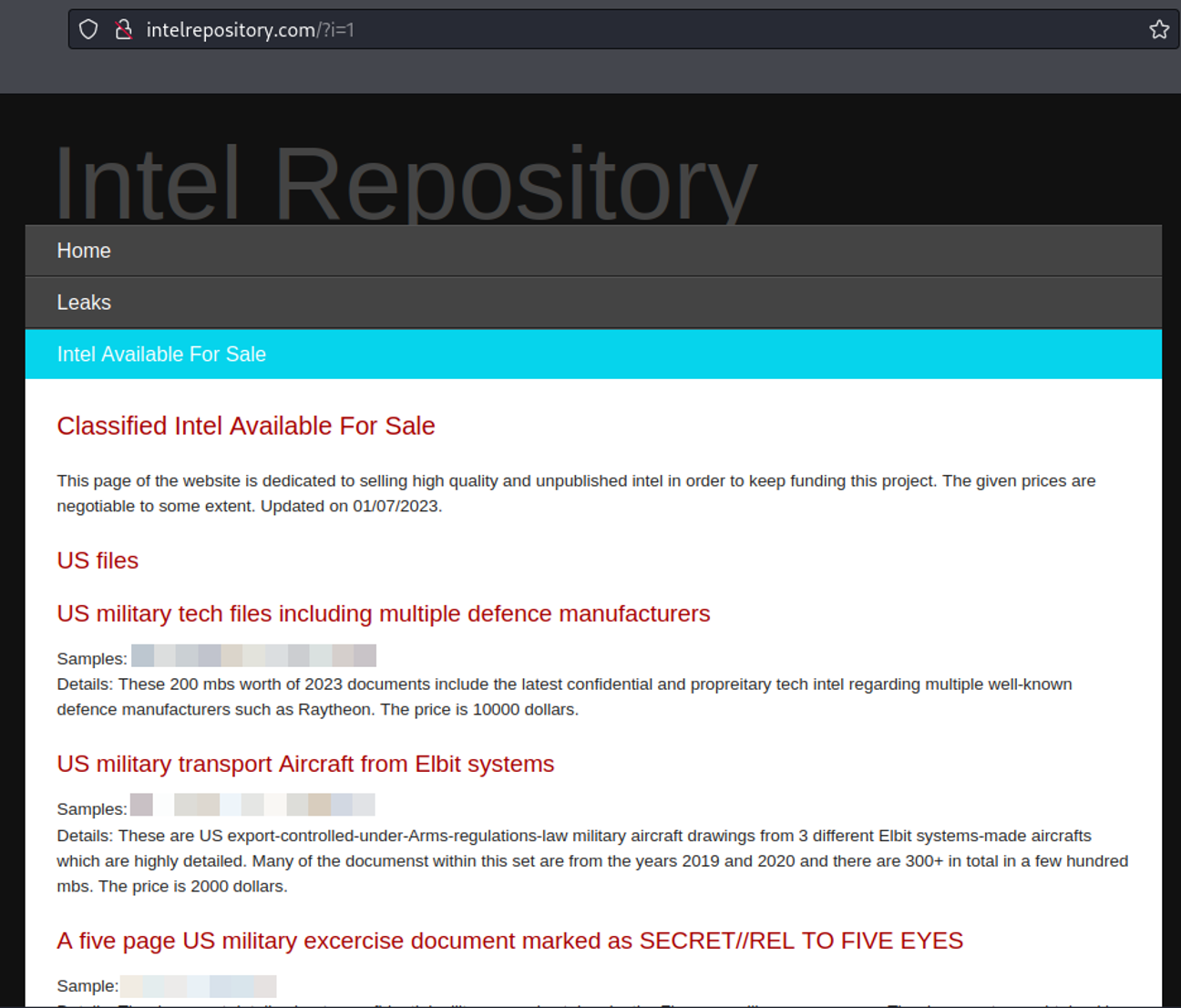
Fig 11 – The ‘Intel Available For Sale’ tab on Spectres Intel Repository – a free repository for data leaks sourced from military insiders, hackers, and hacktivists.
The increasing commodification of compromised military data represents an interesting shift in hacktivist goals. Typically, hacktivists rely on donations or simply act without compensation. The listing of this data for sale rather than free publication represent an interesting sign – potentially that even hacktivists are not immune from economic downturns, resorting to selling their compromised data instead of the usual publication.
Follow-Up with Spectre
![]()
Fig 12 – Screenshot of recent communication with Spectre
In exclusive communication with Spectre obtained by Foretrace’s Data Leak Research Team, Spectre explained their political motivations extend so far as to “have an effect of any kind on the larger and oppressive nations in addition to spreading the knowledge I have”. And to answer why these bundles are for sale, whereas Spectre typically releases for free – “I already have a large number of leaks available for free on my website. And I use the money I earn from this to sustain myself and my operations while also using the funds to acquire more intel to give away for free.”
Impacts and Trends
Victims
The victims in a sale like this are primarily those impacted by leaked intelligence, including the U.S, British, Indian, Philippine, South Korean, and Sri-Lankan militaries, as well as Raytheon, Elbit, Blueberry aviation and HJSC. In this case, documents related to a variety of classified sophisticated weapons systems, drone technology, manned aircraft, and military intelligence files are now available for a price. Specifically, a price that is likely pretty digestible for a government who benefits from simply buying schematics of their enemies systems and plans, rather than spending millions of dollars and countless man hours reverse engineering those systems and running espionage operations to capture additional intel. Now, they simply swipe their card and the hard work is done.
Insider Threats
More than one of Spectres data leaks are claimed to have been sourced from insiders. Typically, this means a military member or contractor who has privileged access to such data, is willingly handing it over to Spectre, or other groups who then share this data with Spectre, for either perceived greater good or some financial benefit. Insider threat has always been a priority for organizations and militaries, and despite increased efforts to address that risk, continues to cause massive incidents like this one.
Recommendations
Understand External Points of Contact
Contact with insiders was required to obtain several collections this confidential, and at times classified and proprietary, data. Understanding the footprint of contact points within your organization, including publicly enumerable emails, phone numbers, and social media profiles, are critical to understanding the full footprint of your exposure. Understanding the most accessible accounts and points of contact, and applying strict security configurations or enhanced logging policies to them, will enable you to keep tabs on the locations where people within your organizations are most often receiving communications and sending data.
Proactive Monitoring
Leverage automation to scour files, storage locations, and forums online for the presence or discussion of your organization’s data.
Foretrace provides data exposure detection capabilities to help our customers detect data leaks and exposures before they become costly data breaches. Follow Foretrace on Twitter and Linkedin to stay updated on our data leak research.


